Chapter 7: Advanced Encryption Standard (AES)
7.1 Introduction
History & Basics
- Replacement for DES, selected by NIST in 2001 (FIPS 197).
- Winning algorithm: Rijndael.
- Symmetric-key block cipher.
- Non-Feistel structure.
- Block Size: 128 bits.
- Key Sizes & Rounds ():
- AES-128: 128-bit key, rounds.
- AES-192: 192-bit key, rounds.
- AES-256: 256-bit key, rounds.
Data Units
- Byte: 8 bits.
- Word: 32 bits (4 bytes).
- Block: 128 bits (16 bytes).
- State: 128 bits arranged as a 4x4 matrix of bytes.
- Block-to-State Conversion: Fill state column by column.
- Input block:
- State:
Example (Fig 7.4): “AESUSESAMATRIXZZ”
- Hex:
00 04 12 14 12 04 12 00 OC 00 13 11 08 23 19 19 - State:
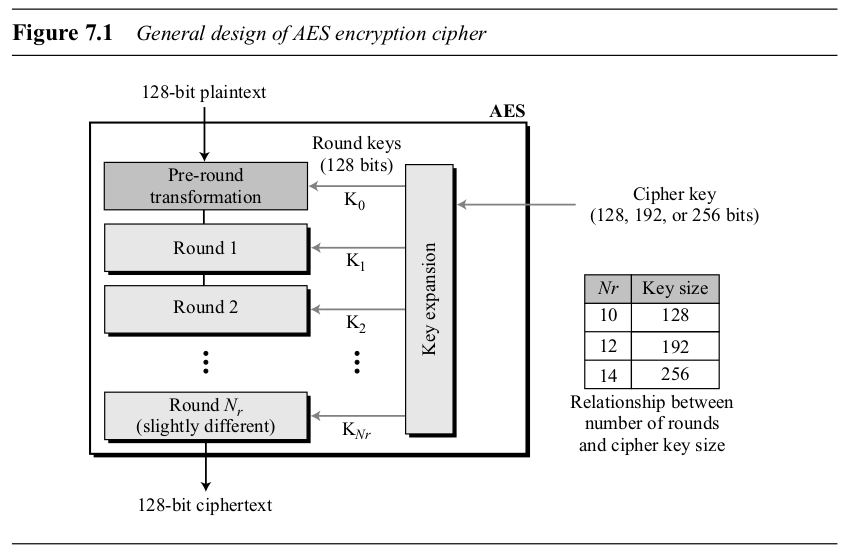
Round Structure (Encryption)
- Pre-round: AddRoundKey.
- Rounds 1 to :
- SubBytes
- ShiftRows
- MixColumns
- AddRoundKey
- Final Round ():
- SubBytes
- ShiftRows
- AddRoundKey (No MixColumns)
7.2 Transformations
Operations are performed on the State matrix.
SubBytes (Substitution)
- Purpose: Non-linear byte substitution for confusion.
- Process: Replace each byte using a fixed S-box (Table 7.1). .
- GF() View:
- Find multiplicative inverse of the byte in with irreducible polynomial . (Inverse of is ). Let the inverse be .
- Apply affine transformation: , where is treated as a column vector of its bits, is bitwise XOR.
- InvSubBytes: Use Inverse S-box (Table 7.2) or inverse affine transformation: . Then find multiplicative inverse of .
Example (Byte 0C → FE):
- Byte is .
- Multiplicative inverse in is . Let (LSB top).
- Matrix multiplication (details omitted) gives .
- XOR with : .
ShiftRows (Permutation)
- Purpose: Diffusion across bytes in a row.
- Process: Cyclically shift bytes in rows to the left:
- Row 0: No shift.
- Row 1: Shift 1 byte left.
- Row 2: Shift 2 bytes left.
- Row 3: Shift 3 bytes left.
- InvShiftRows: Shift rows to the right by the same offsets.
Example (Fig 7.10):
- Input State:
- ShiftRow 1 left by 1:
F2 63 26 F2 - ShiftRow 2 left by 2:
7D D4 C9 C9 - ShiftRow 3 left by 3:
D4 FA 63 82 - Output State:
MixColumns (Mixing)
- Purpose: Diffusion across bytes within a column.
- Process: Treat each column as a vector and multiply by a constant matrix in .
- Addition is XOR ().
- Multiplication is in (mod ).
- (left shift, if original MSB was 1, XOR with ).
- .
- InvMixColumns: Multiply by (See Fig 7.12 for ).
- Note: Skipped in the last round.
Example (Mix one column element):
- Let , .
- : (MSB was 1, but overflow bit is lost, no need to XOR with 1B? Wait, xtime is shift then XOR if needed).
- Correct xtime: . MSB is 1. Left shift: . XOR with . . So .
- .
- : . MSB is 0. Left shift: . So .
- .
AddRoundKey
- Purpose: Combine the round key with the state.
- Process: XOR the state matrix with the current round key matrix (128 bits). Each byte (where is the corresponding byte of the round key).
- Self-Inverse: .
7.3 Key Expansion
- Goal: Generate round keys () from the cipher key.
- Each round key is 128 bits (4 words). Total words .
- Uses RotWord, SubWord, and RCon (Round Constant).
- RotWord: Circular left shift of bytes in a word. .
- SubWord: Apply S-box to each byte of a word.
- RCon: where in .
- . (See Table 7.4).
Key Expansion for AES-128 (, )
- Need 44 words ( to ). Cipher key forms .
- For to 43:
- Calculate temp word .
- If :
- If :
Key Expansion for AES-192 (, )
- Need 52 words ( to ). Cipher key forms .
- For to 51:
- .
- If : .
- .
Key Expansion for AES-256 (, )
- Need 60 words ( to ). Cipher key forms .
- For to 59:
- .
- If : .
- Else if : . (Extra SubWord step specific to AES-256)
- .
7.4 Ciphers (Encryption/Decryption)
Original Design
- Encryption: As described in Round Structure. Uses keys to .
- Decryption: Inverse transformations applied in reverse order. Key schedule used in reverse ( to ). Order within rounds differs from encryption.
- Initial AddRoundKey ()
- Rounds 1 to : InvShiftRows, InvSubBytes, AddRoundKey(), InvMixColumns.
- Final Round (): InvShiftRows, InvSubBytes, AddRoundKey(). (No InvMixColumns)
Alternative Design
- Goal: Make Decryption structure more similar to Encryption.
- Key Idea: Swap InvShiftRows/InvSubBytes (okay). Swap AddRoundKey/InvMixColumns by modifying the round keys used in decryption.
- Modified Decryption Keys: For rounds 1 to (of decryption), use . Keys and are used unchanged.
- Alternative Decryption Structure:
- Initial AddRoundKey ()
- Rounds 1 to : InvSubBytes, InvShiftRows, InvMixColumns, AddRoundKey().
- Final Round (): InvSubBytes, InvShiftRows, AddRoundKey(). (No InvMixColumns)
- Requires pre-computation of .
7.6 Analysis of AES
- Security: Strong against known attacks (brute-force, linear, differential, etc.). Large key space. Good diffusion and confusion. No weak keys.
- Implementation: Efficient in hardware and software (table lookups or GF math). Can be byte or word oriented.
- Simplicity: Relatively simple and elegant design.