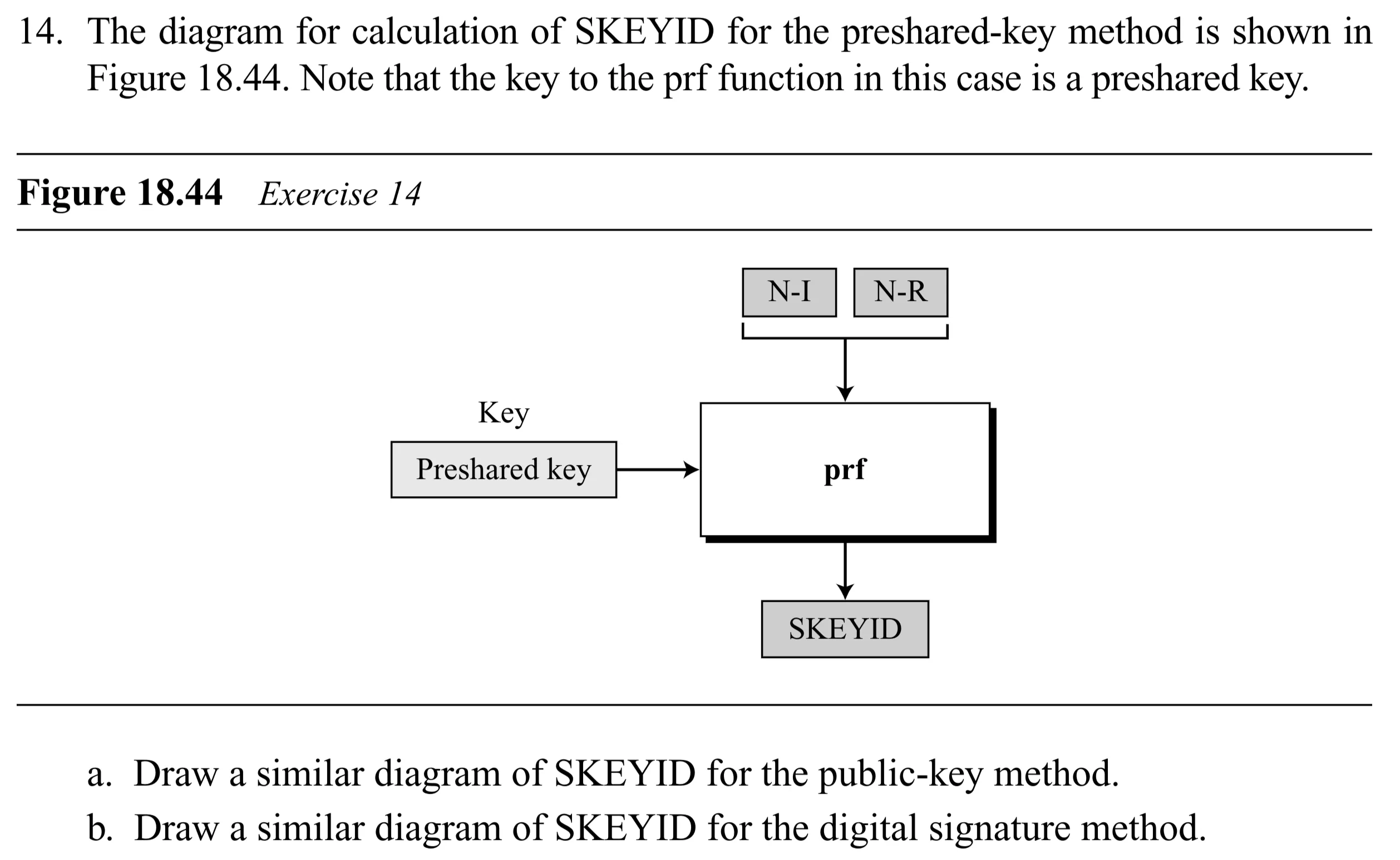
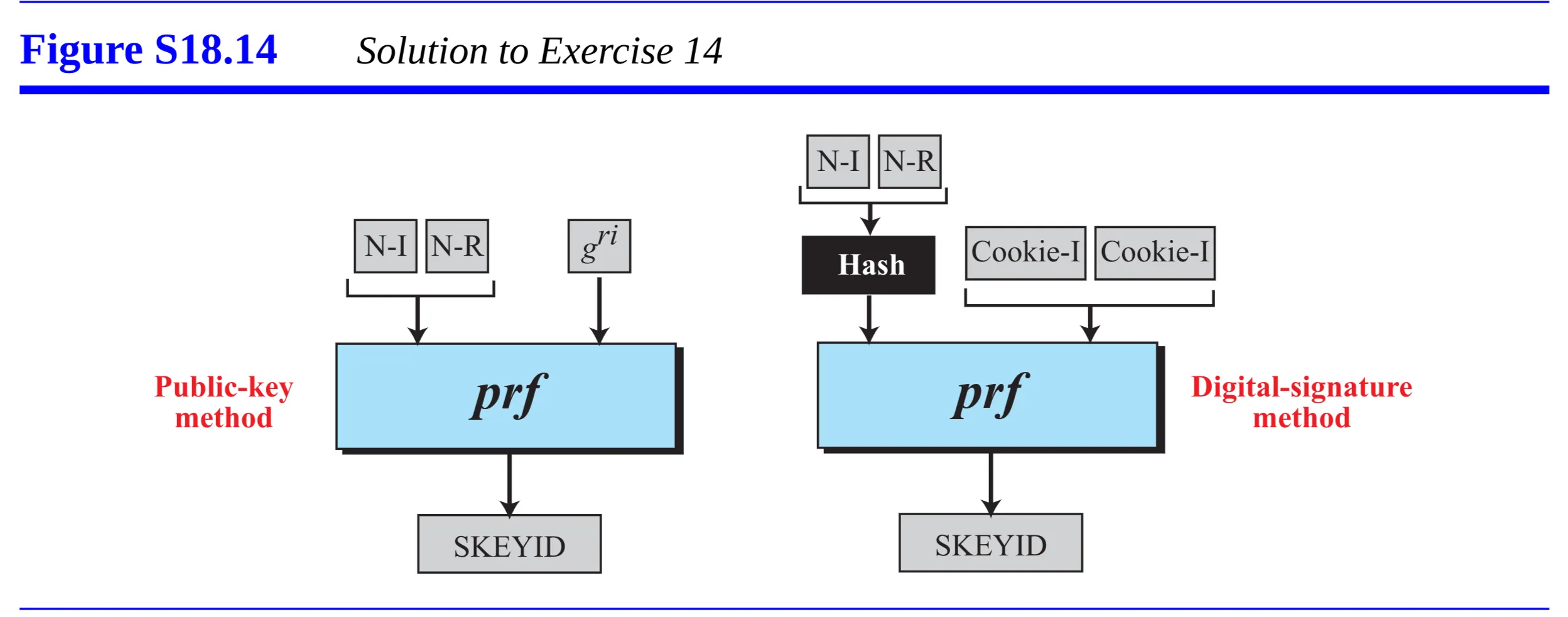
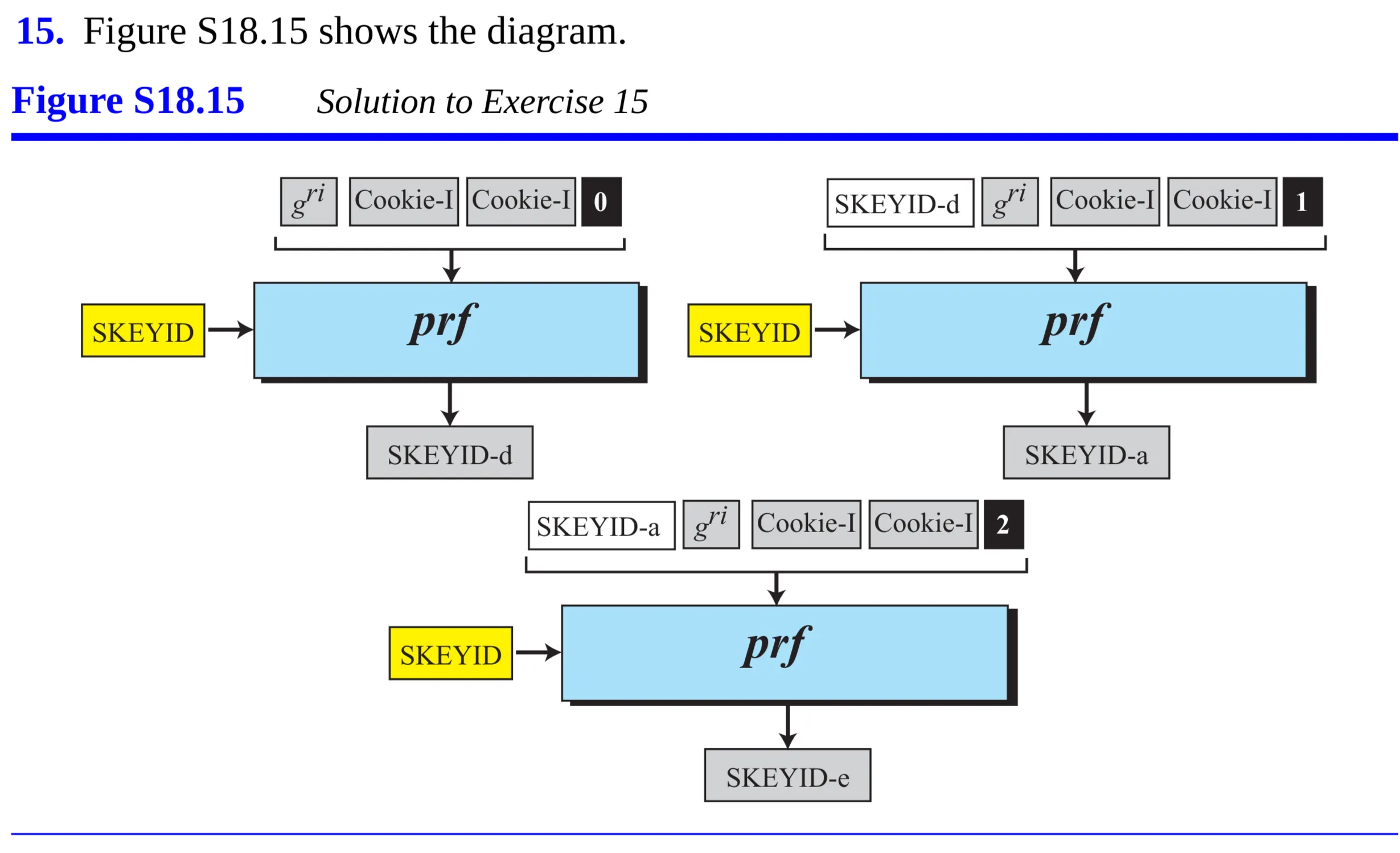
- Discuss replay attack prevention using sequence numbers and a sliding receiver window in IPSec protocol. Assume the following scenario to answer
-
A host receives an authenticated packet with the sequence number 181. The replay window spans from 200 to 263. What will the host do with the packet? What is the window span after this event? Since the sequence number of the packet (181) is out of the window (200 to 264), the packet is discarded. It is either duplicate or its arrival time has expired. The window span does not change.
-
A host receives an authenticated packet with the sequence number 208. The replay window spans from 200 to 263. What will the host do with the packet? What is the window span after this event? The sequence number of the packet (208) is inside the window (200 to 263). If the packet is new (the corresponding slot is not marked), the packet is accepted and the corresponding slot is marked. If the corresponding slot is marked, the packet is a duplicate packet; it is discarded. There is no change in the window span in either case.
-
A host receives an authenticated packet with the sequence number 331. The replay window spans from 200 to 263. What will the host do with the packet? What is the window span after this event? The sequence number of the packet (331) is at the right of the window. Since the packet is authenticated, it is accepted and the window span will change as shown in Figure S18.13.

-
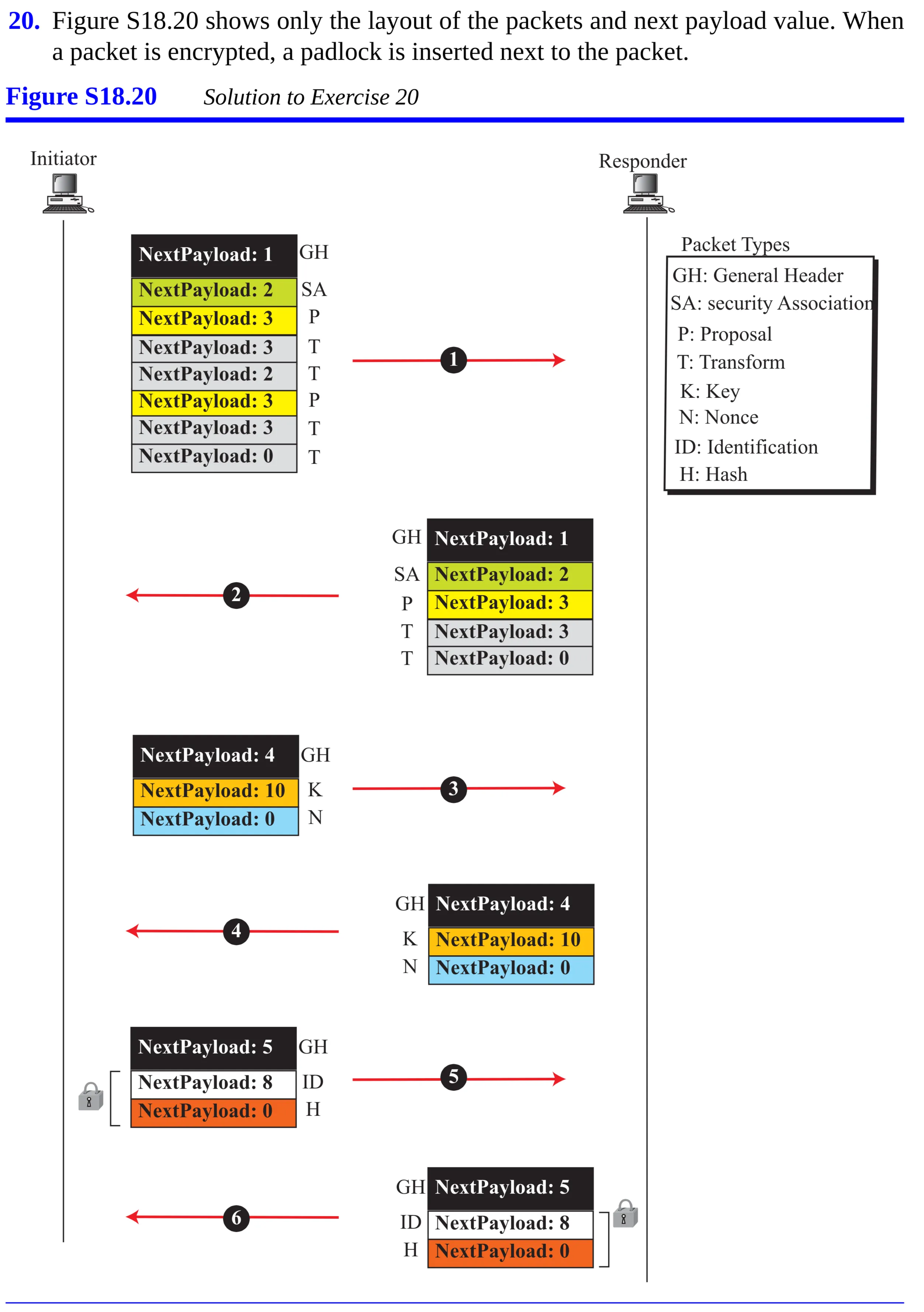
- Draw a diagram and show actual ISAKMP packets that are exchanged between an initiator and a responder using the
preshared-keymethod in themainmode. Use at least two proposal packets with at least two transform packets for each proposal.