CHAPTER 18: Security at the Network Layer: IPSec
Introduction
-
Security at the application and transport layers (like PGP, S/MIME, SSL/TLS) may not be sufficient because:
- Not all client/server programs are protected at the application layer.
- Not all programs use TCP (which SSL/TLS relies on); some use UDP.
- Many applications (e.g., routing protocols) use IP directly and need security at the IP layer.
-
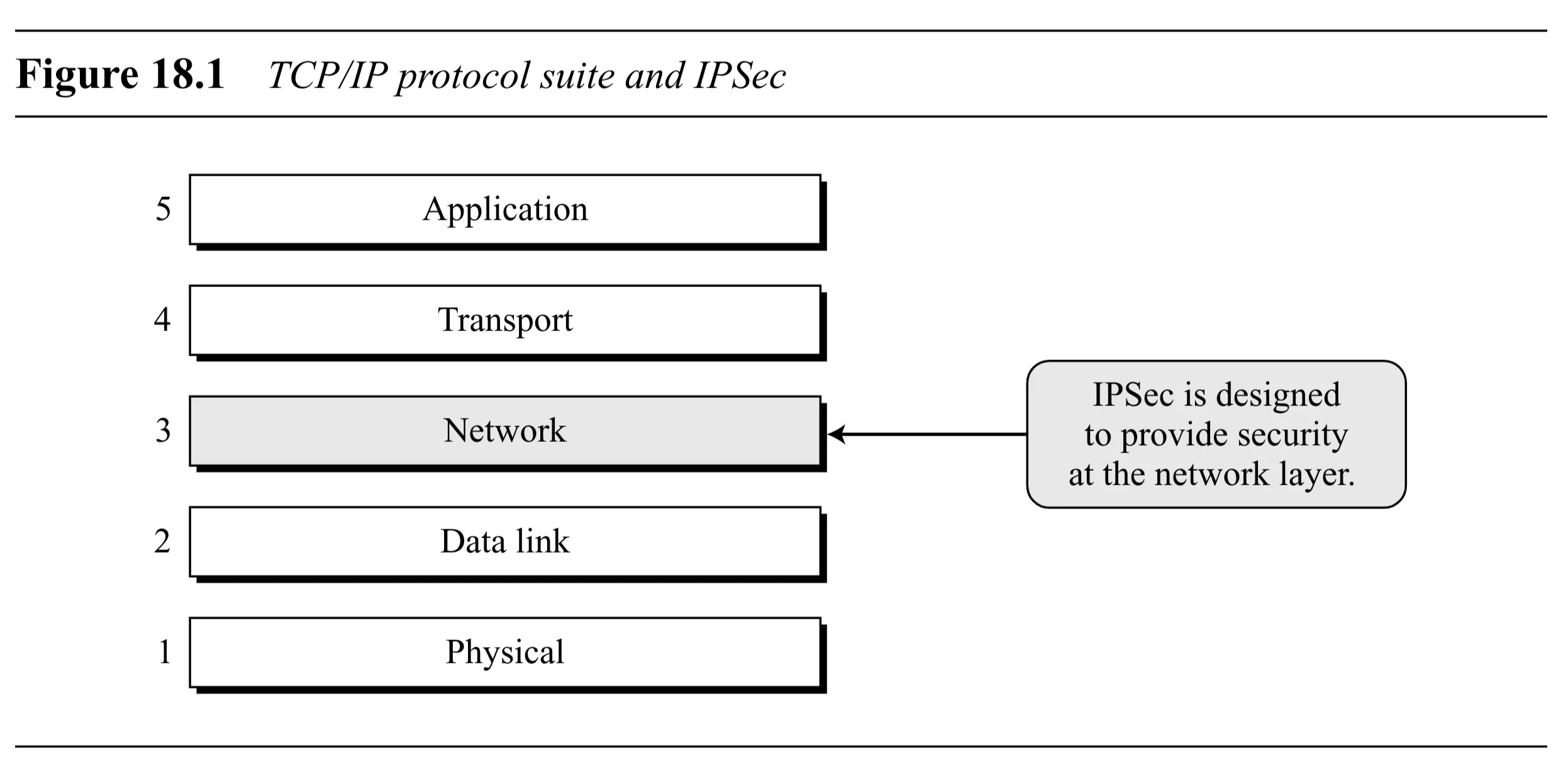
IP Security (IPSec): A collection of protocols designed by the IETF to provide security for packets at the network (IP) layer.
-
IPSec helps create authenticated and confidential packets for the IP layer.
-
Usefulness of IPSec:
- Enhances security for applications with their own security protocols (e.g., email).
- Enhances security for applications using transport layer security (e.g., HTTP with TLS).
- Provides security for applications not using transport layer security.
- Provides security for node-to-node communication (e.g., routing protocols).
18.1 TWO MODES
IPSec operates in two different modes: transport mode or tunnel mode.
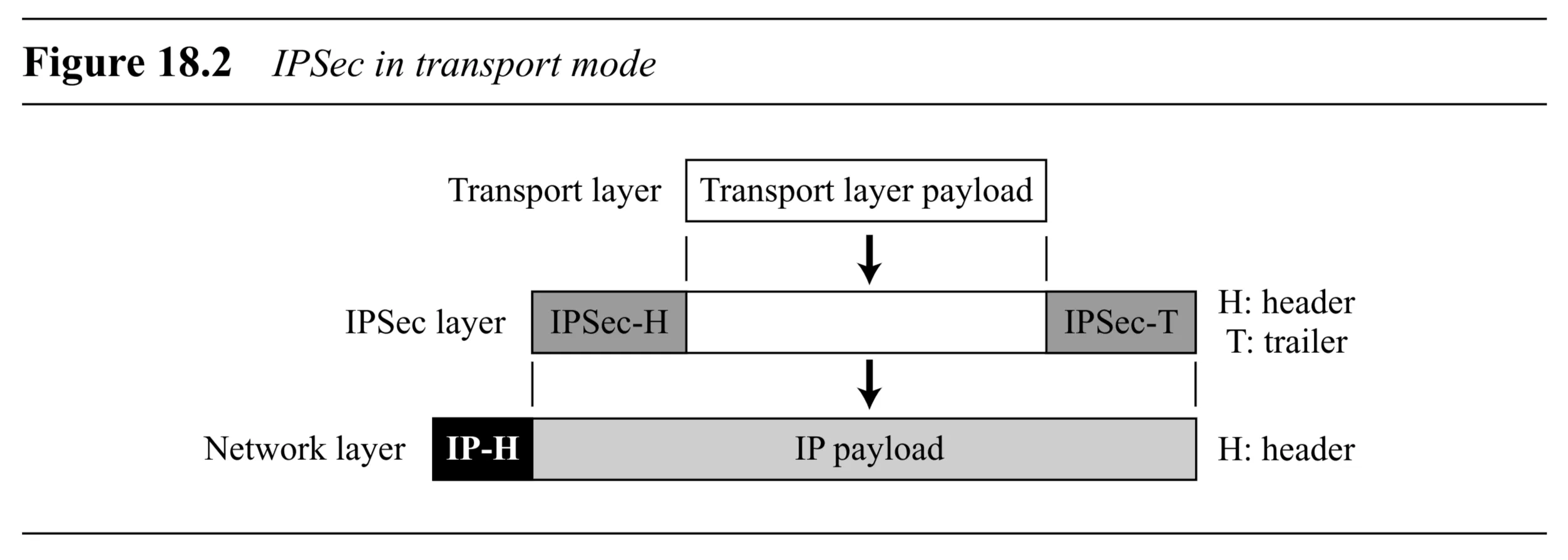
Transport Mode
-
Protection Scope: Protects the payload delivered from the transport layer to the network layer (i.e., the network layer payload).
-
Encapsulation: The IPSec header and trailer are inserted between the original IP header and the transport layer payload.
-
IP Header: The original IP header is not protected by IPSec in transport mode; it is added after IPSec processing.
-
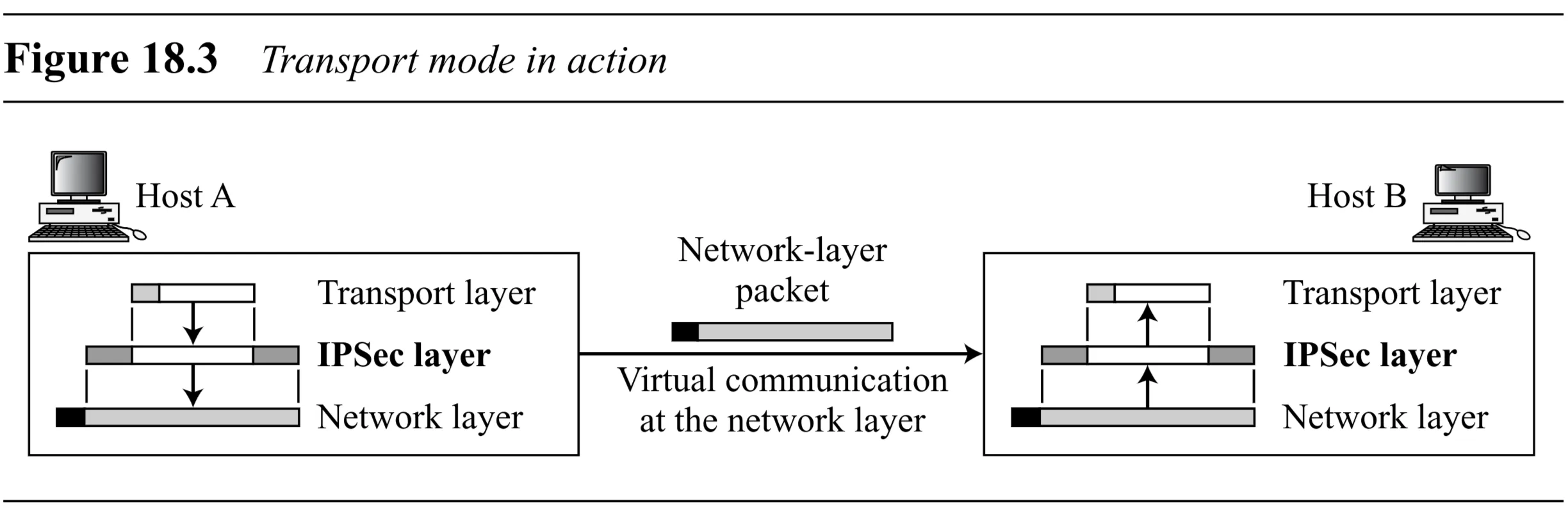
Usage: Typically used for host-to-host (end-to-end) protection.
- Sending host uses IPSec to authenticate/encrypt the transport layer payload.
- Receiving host uses IPSec to check authentication/decrypt the packet before delivering to the transport layer.
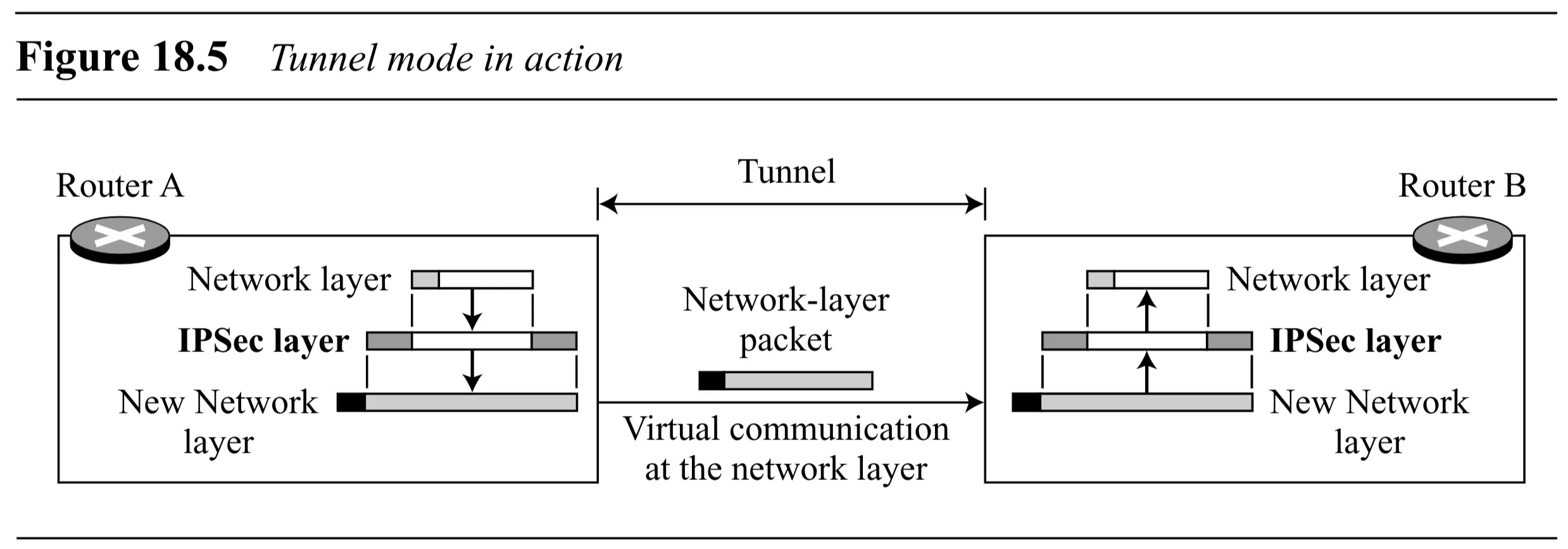
Tunnel Mode
- Protection Scope: Protects the entire original IP packet, including the original IP header.
- Encapsulation: IPSec takes the entire IP packet, applies security, and then adds a new IP header.
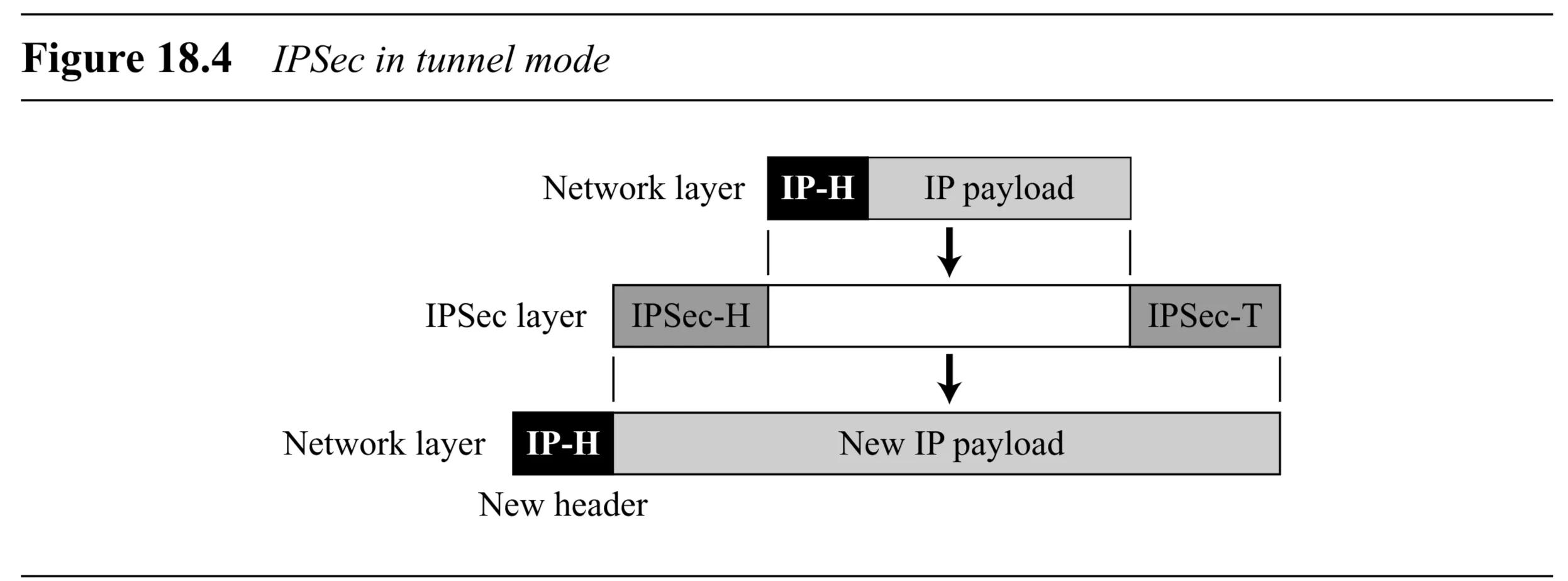
- New IP Header: Contains different information (e.g., different source/destination addresses, often addresses of security gateways like routers) than the original IP header.
- Usage: Typically used when at least one endpoint is a security gateway (e.g., router).
- Between two routers.
- Between a host and a router.
- Between a router and a host.
- Used when the sender or receiver is not the final host. Protects the packet over an “imaginary tunnel”.
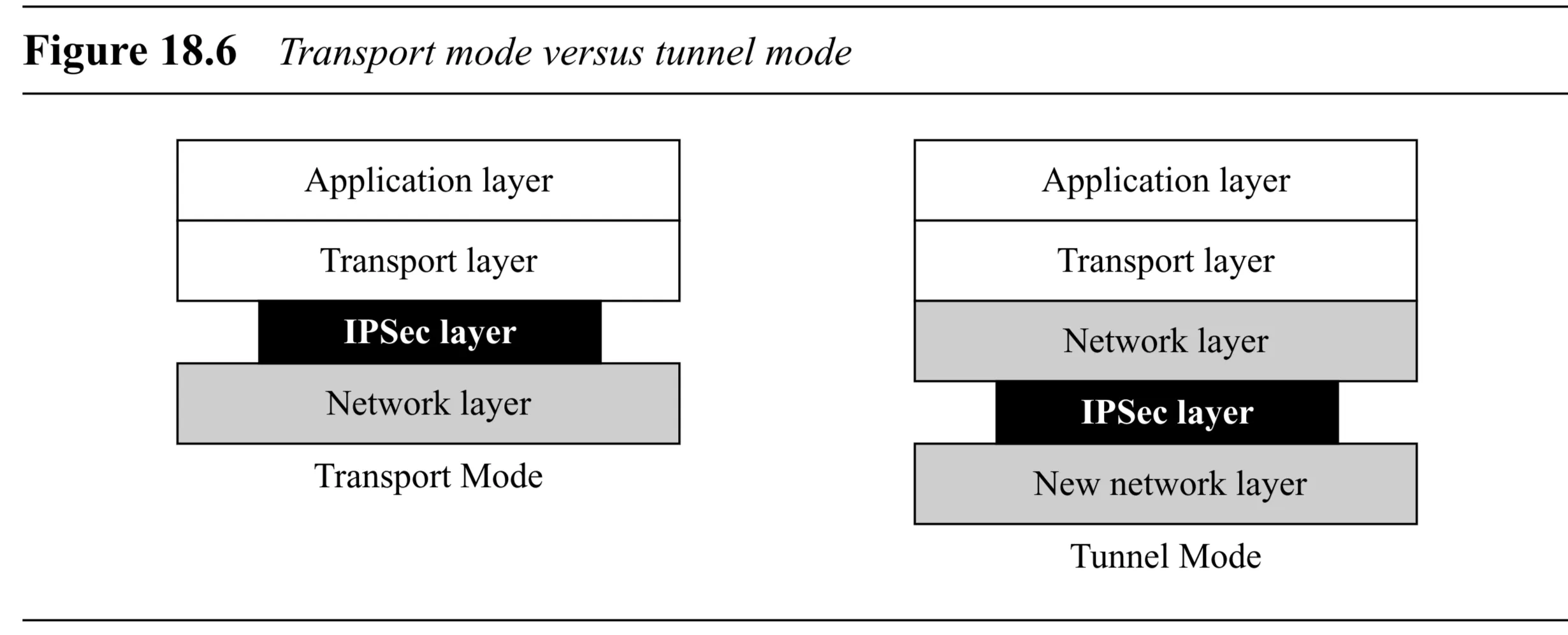
Comparison (Transport vs. Tunnel)
- Transport Mode:
- IPSec layer is between the Transport and Network layers.
- Protects Transport layer payload.
- Original IP header is exposed.
- Tunnel Mode:
- IPSec layer effectively encapsulates the Network layer packet and passes it back to the Network layer to add a new header.
- Protects the entire original IP packet (including header).
- Original IP header is hidden inside the new packet.
18.2 TWO SECURITY PROTOCOLS
IPSec defines two main protocols:
- Authentication Header (AH)
- Encapsulating Security Payload (ESP)
Authentication Header (AH)
-
Purpose:
- Provides source host authentication.
- Ensures data integrity of the payload.
-
Mechanism: Uses a hash function and a symmetric key to create a message digest (Authentication Data).
-
Placement: The AH header is placed in the packet based on the mode (transport or tunnel).
-
Protocol Number: When AH is used, the
Protocolfield in the preceding IP header is set to . -
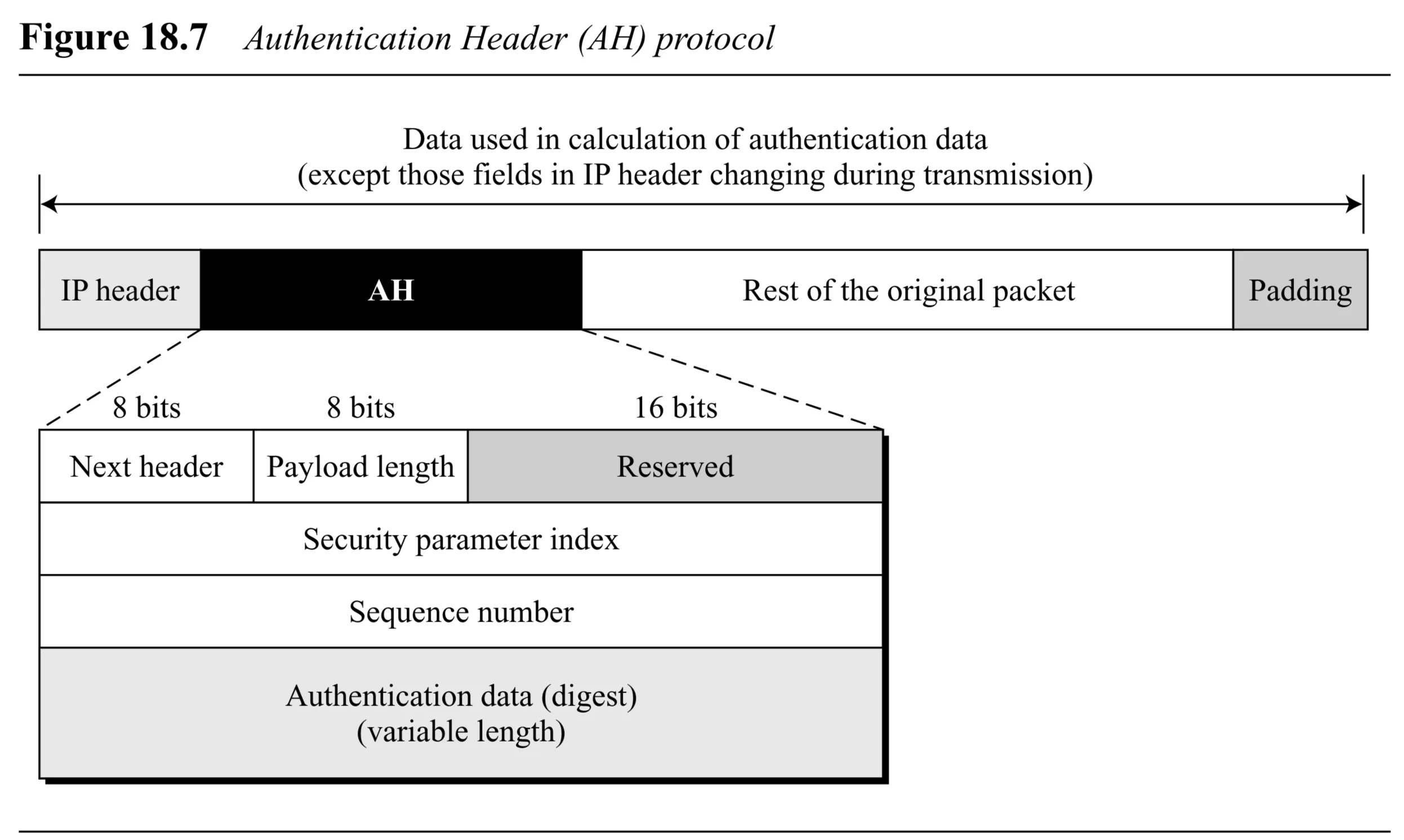
AH Header Format (Figure 18.7):
- Next Header ( bits): Stores the original value of the
Protocolfield (e.g., TCP, UDP, ICMP). Identifies the type of payload following AH. - Payload Length ( bits): Defines the length of the AH header itself in -byte multiples, excluding the first bytes. (Misleading name).
- Reserved ( bits): Reserved for future use.
- Security Parameter Index (SPI) ( bits): Identifies the Security Association (SA) for this packet. Acts like a virtual circuit identifier.
- Sequence Number ( bits): Provides ordering information, prevents replay attacks. Starts at , increments, does not wrap around (new SA needed after ). Not repeated for retransmissions.
- Authentication Data (digest) (variable length): The message digest calculated over parts of the IP packet (including parts of the IP header that don’t change in transit, the AH header itself with this field zeroed, and the payload). Padding may be added before hashing.
- Next Header ( bits): Stores the original value of the
-
Process for Adding AH:
- Add AH header to payload (Authentication Data field = ).
- Add padding if required by the hash algorithm.
- Calculate hash (message digest) over the packet (excluding mutable IP header fields).
- Insert the calculated hash into the Authentication Data field.
- Add/Modify the IP header, setting the
Protocolfield to and storing the original protocol type in AH’sNext Headerfield.
-
Security Provided: Source authentication and data integrity. Does not provide confidentiality (privacy).
Encapsulating Security Payload (ESP)
- Purpose:
- Provides source authentication.
- Provides data integrity.
- Provides confidentiality (privacy) through encryption.
- Mechanism: Adds an ESP header and an ESP trailer. Authentication data is added at the end.
- Placement: Figure 18.8 shows ESP header and trailer placement (likely in transport mode, though not explicitly stated for this figure).
- Protocol Number: When ESP is used, the
Protocolfield in the preceding IP header is set to .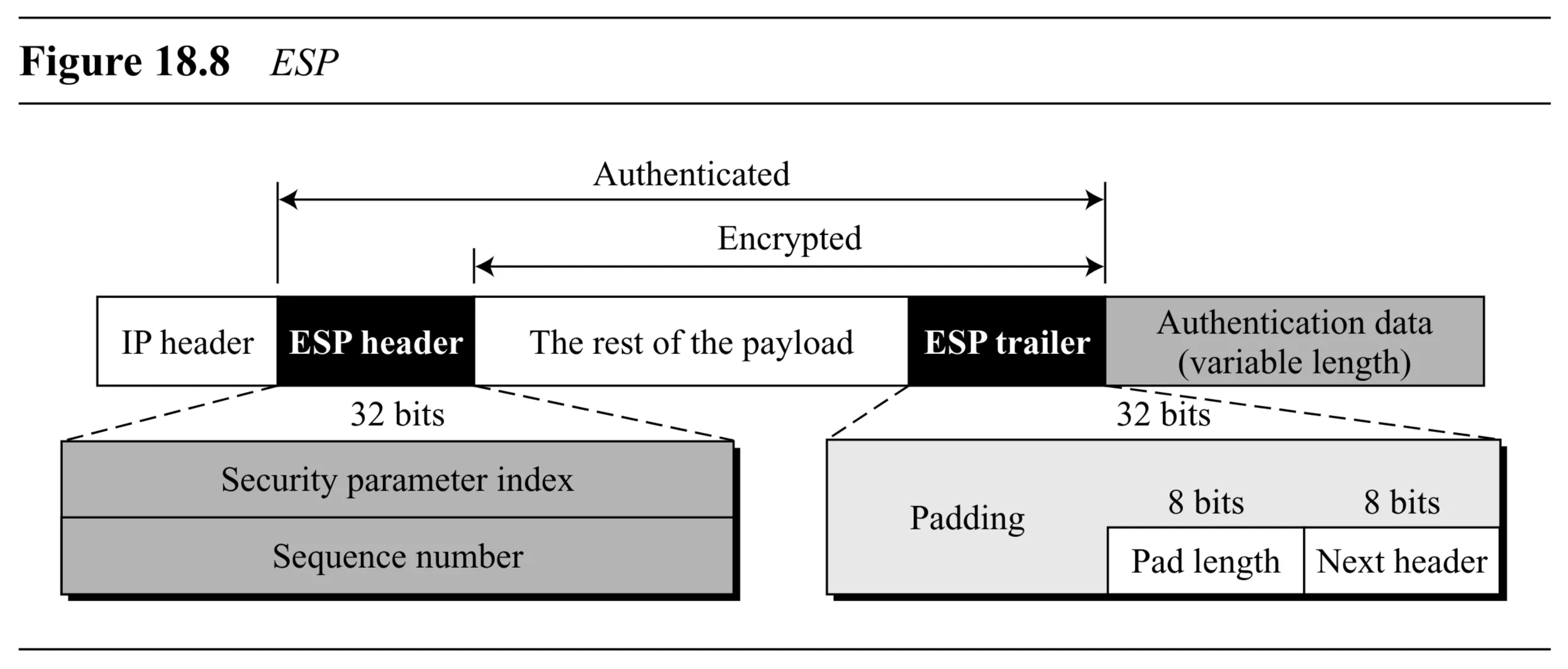
- ESP Format (Figure 18.8):
- ESP Header:
- Security Parameter Index (SPI) ( bits): Same function as in AH. Identifies the SA.
- Sequence Number ( bits): Same function as in AH. Prevents replay.
- Payload Data (variable length): The original payload (e.g., transport layer segment). This part is encrypted.
- ESP Trailer:
- Padding (0-255 bytes): Used for block cipher padding requirements and to align the Pad Length and Next Header fields. Content is often s. This part is encrypted.
- Pad Length ( bits): Specifies the number of padding bytes added. This part is encrypted.
- Next Header ( bits): Stores the original value of the
Protocolfield (identifies the type of payload data). This part is encrypted.
- Authentication Data (variable length): A digest calculated over the ESP header, payload data, and ESP trailer. This part is not encrypted. Added after encryption.
- ESP Header:
- Process for Adding ESP:
- Add ESP trailer to the original payload.
- Encrypt the combined payload and ESP trailer.
- Add the ESP header before the encrypted data.
- Calculate the authentication data over the ESP header and the encrypted (payload+trailer).
- Append the authentication data.
- Add/Modify the IP header, setting the
Protocolfield to and storing the original protocol type in ESP’sNext Headerfield (inside the trailer).
- Security Provided: Source authentication, data integrity, and confidentiality.
- Authentication Scope Difference: AH authentication includes parts of the IP header, ESP authentication typically does not (it authenticates from the ESP header onwards).
IPv4 and IPv6
- IPSec supports both IPv4 and IPv6.
- In IPv6, AH and ESP are implemented as extension headers.
AH versus ESP
- ESP was designed after AH and provides all the services of AH plus confidentiality.
- Logically, AH might seem redundant.
- However, AH implementations exist in commercial products, so it remains part of the standard until phased out.
Services Provided by IPSec
Table 18.1 IPSec services
| Service | AH | ESP | Description |
|---|---|---|---|
| Access control | yes | yes | Indirectly provided via Security Association Database (SAD). Packets without a matching SA are discarded. |
| Message integrity | yes | yes | Ensured by the keyed hash (Authentication Data field) created by the sender and verified by the receiver. |
| Entity authentication | yes | yes | Provided by the Security Association (SA) establishment and the keyed hash, authenticating the sender. |
| Confidentiality | no | yes | Provided by encryption in ESP. AH does not encrypt data. Use ESP if confidentiality is needed. |
| Replay attack protection | yes | yes | Prevented using sequence numbers and a fixed-size sliding receiver window (default size ). (See Figure 18.9). |
Replay Attack Protection Details (Sliding Window)
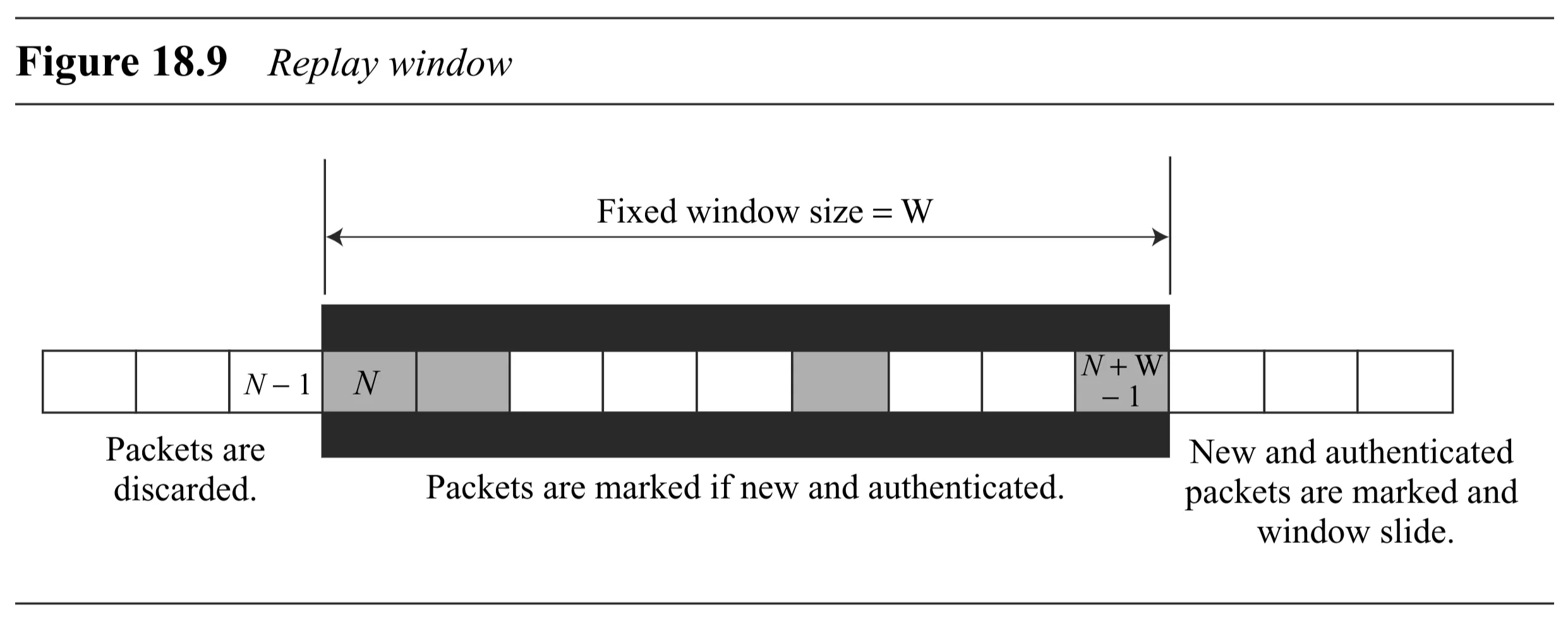
- Each IPSec header (AH or ESP) has a unique sequence number per SA.
- Starts at , increments, reset to when is reached (requires a new SA).
- Receiver maintains a sliding window of expected sequence numbers, size (default ). The window represents sequence numbers .
- Packet Arrival Processing (Figure 18.9):
- Sequence Number : Packet is to the left of the window. Discarded (duplicate or too old).
- Sequence Number : Packet is inside the window.
- If packet is new (sequence number not marked as received) AND passes authentication: Mark sequence number as received, accept packet.
- Otherwise (already received or fails authentication): Discard packet.
- Sequence Number : Packet is to the right of the window.
- If packet passes authentication: Mark sequence number as received, slide window to the right so the new sequence number is the rightmost edge (new = received_seq_num - ). Accept packet.
- Otherwise: Discard packet.
- Note: If a packet arrives with a sequence number much larger than , sliding the window might cause unmarked sequence numbers to fall to the left, meaning those packets will be discarded if they arrive later.
18.3 SECURITY ASSOCIATION (SA)
- Concept: A logical relationship or contract between two communicating entities (hosts or gateways) required by IPSec. It defines the security parameters for communication in one direction.
- Unidirectional: For bidirectional communication, two SAs are needed (one inbound, one outbound).
- Simple SA Example (Figure 18.10): Alice sending confidentially to Bob.
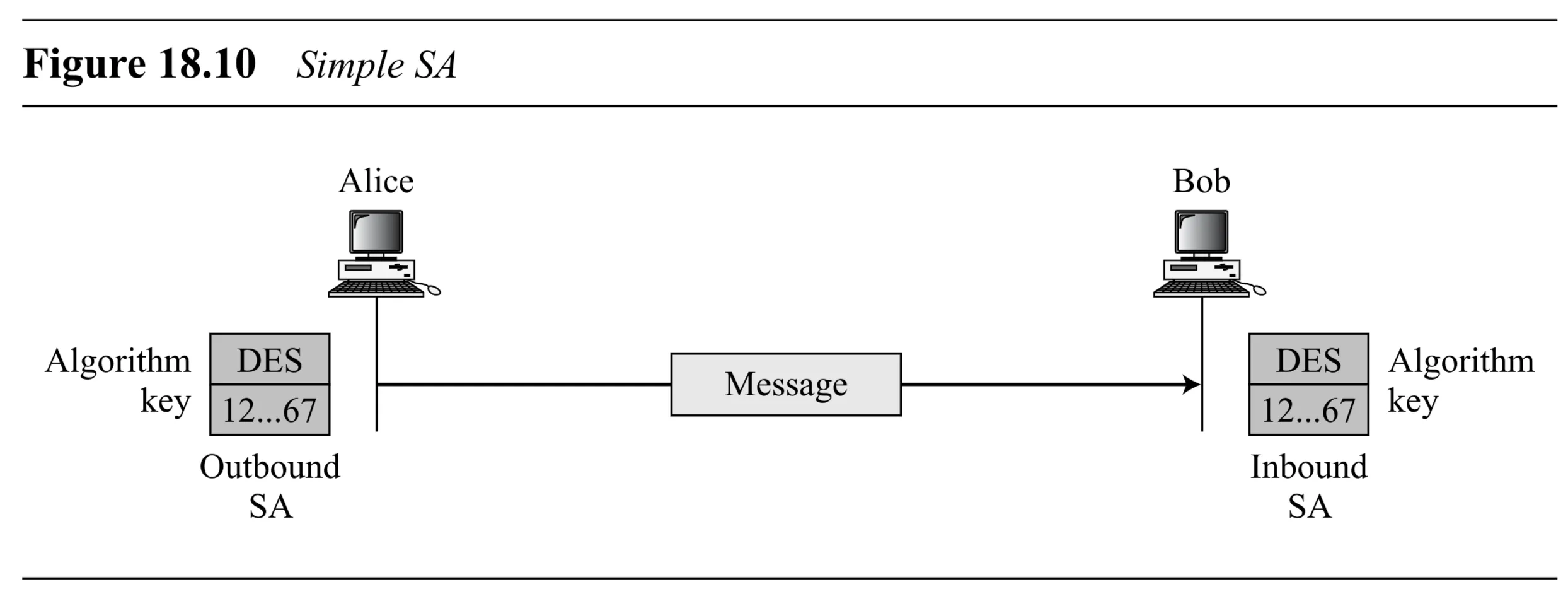
- Alice’s Outbound SA: Stores shared secret key, encryption algorithm (e.g., DES).
- Bob’s Inbound SA: Stores the same shared secret key, decryption algorithm (e.g., DES).
- Complexity: SAs can be more complex, including parameters for integrity algorithms, keys, lifetimes, etc., especially when using AH or ESP.
Security Association Database (SAD)
- Hosts/gateways using IPSec need to store multiple SAs (for different peers, different protocols, inbound/outbound).
- This collection of SAs is stored in a Security Association Database (SAD).
- Typically, two SADs exist: one for inbound SAs and one for outbound SAs.
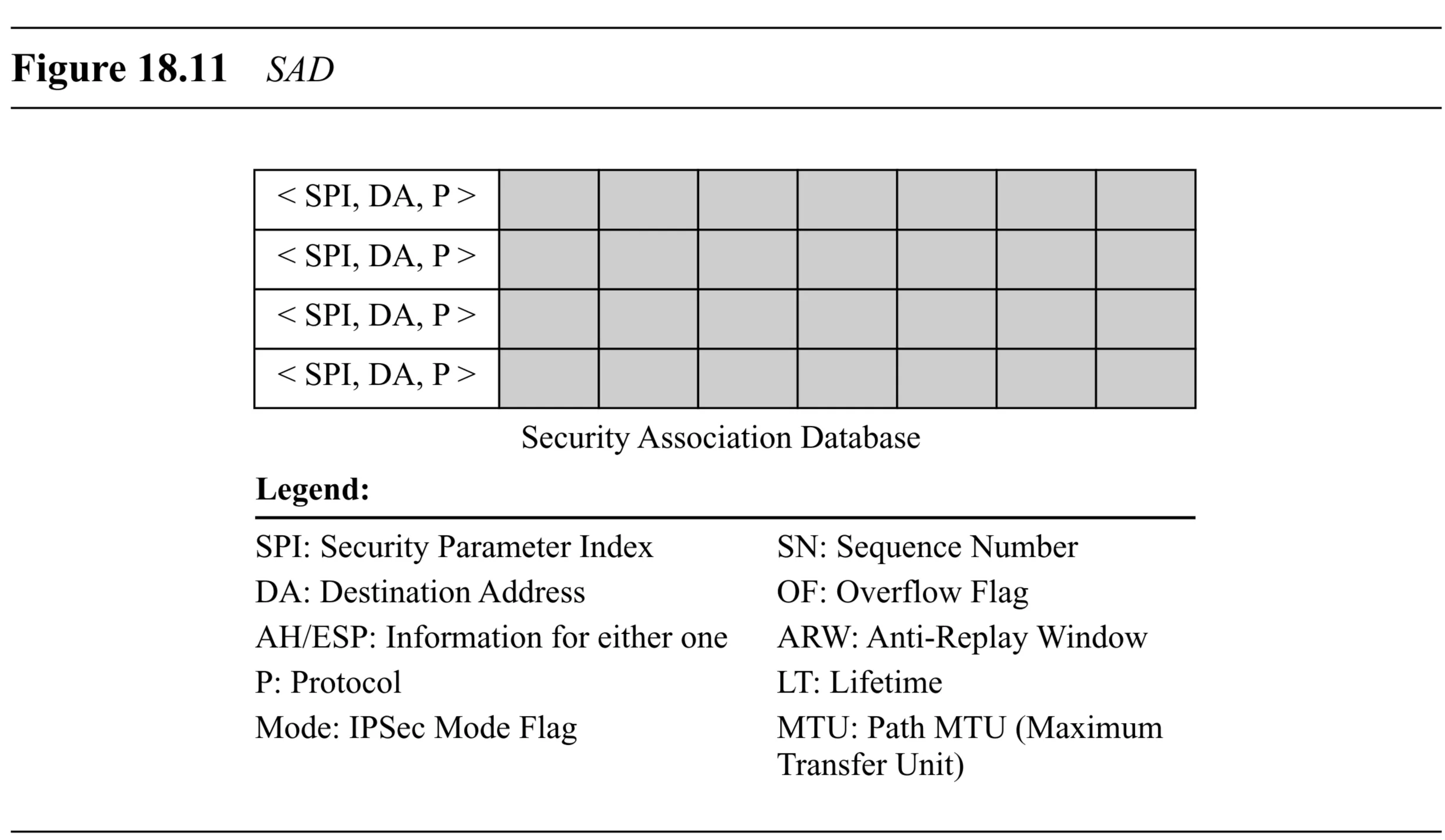
- Inbound SA Selection: An inbound SA is selected using a triple index:
- Security Parameter Index (SPI): A -bit value carried in the AH/ESP header that uniquely identifies the SA at the destination. Determined during SA negotiation (e.g., via IKE).
- Destination Address: The IP address of the receiving host/gateway. Needed because a host might have multiple addresses (unicast, multicast).
- Protocol: The IPSec protocol being used (AH or ESP). Different SAs are needed for AH and ESP.
- Outbound SA Selection: (Not explicitly indexed in the same way by incoming packet fields, but selected based on policy matching, see SPD section).
SA Parameters
Each entry (row) in the SAD defines an SA and contains parameters. Typical parameters include (Table 18.2): Table 18.2 Typical SA Parameters
| Parameter | Description |
|---|---|
| Sequence Number Counter | -bit value used to generate the next sequence number for AH/ESP headers. |
| Sequence Number Overflow | Flag indicating action on sequence number counter overflow (e.g., trigger SA renegotiation). |
| Anti-Replay Window | Information for replay detection (e.g., window size , received packet bitmap). |
| AH Information | Parameters specific to AH (Authentication algorithm, keys, key lifetime, etc.). |
| ESP Information | Parameters specific to ESP (Encryption algorithm, Authentication algorithm, keys, key lifetime, IVs, etc.). |
| SA Lifetime | Defines how long the SA is valid (time-based or byte-based). |
| IPSec Mode | Transport or Tunnel mode. |
| Path MTU | Maximum Transmission Unit for the path (relevant for fragmentation). |
18.4 SECURITY POLICY (SP)
- Concept: Defines what type of security (if any) should be applied to IP packets based on their characteristics.
- Determines whether and how IPSec should be used before consulting the SAD.
Security Policy Database (SPD)
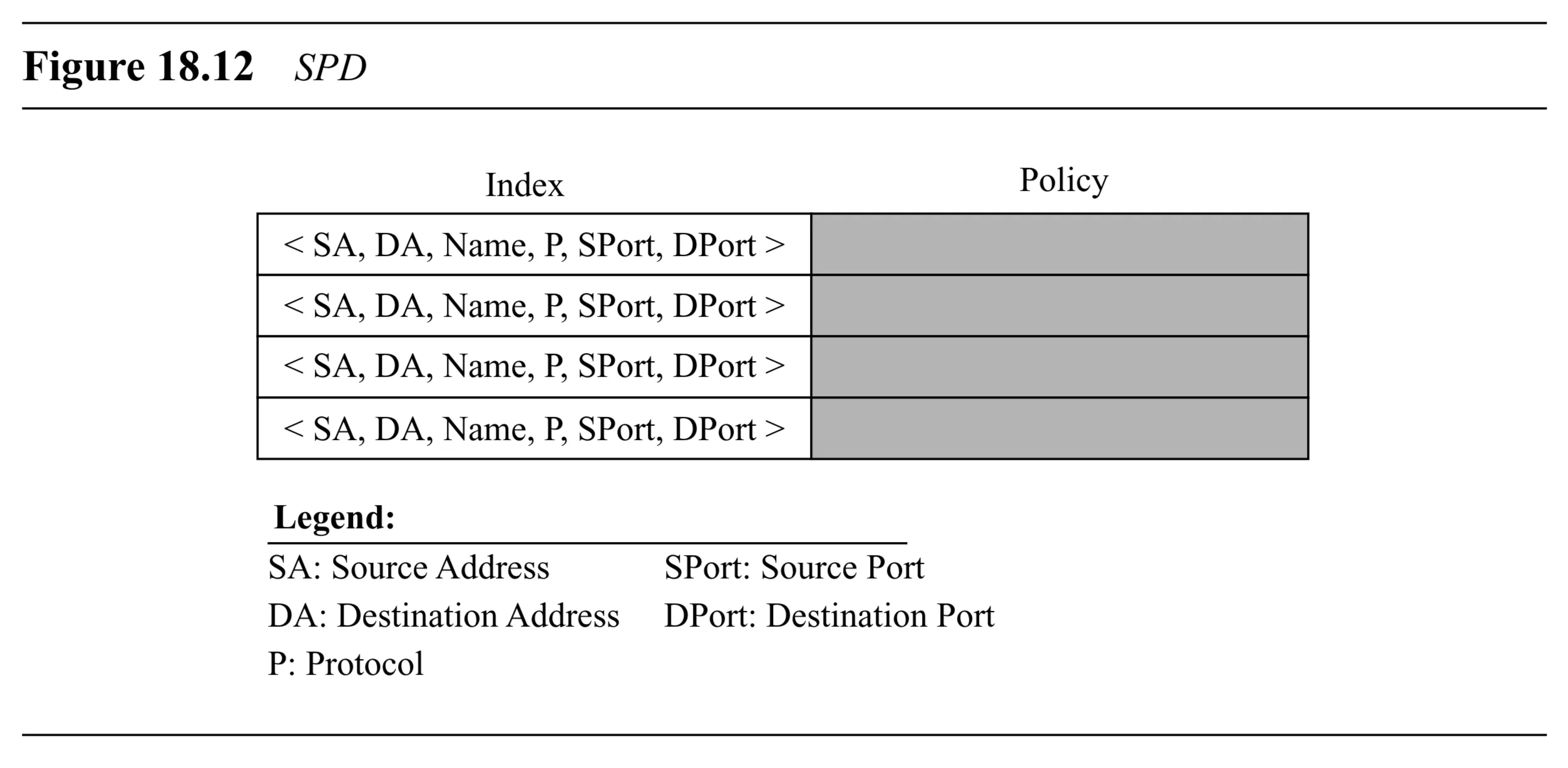
- Hosts/gateways using IPSec maintain a Security Policy Database (SPD).
- Separate inbound and outbound SPDs exist.
- SPD Entry Selection: Each policy entry is indexed by a sextuple index (selectors):
- Source Address
- Destination Address (can be unicast, multicast, wildcard)
- Name (e.g., DNS entity)
- Protocol (e.g., TCP, UDP, ICMP, or AH/ESP themselves if processing nested tunnels)
- Source Port
- Destination Port
Outbound SPD Processing
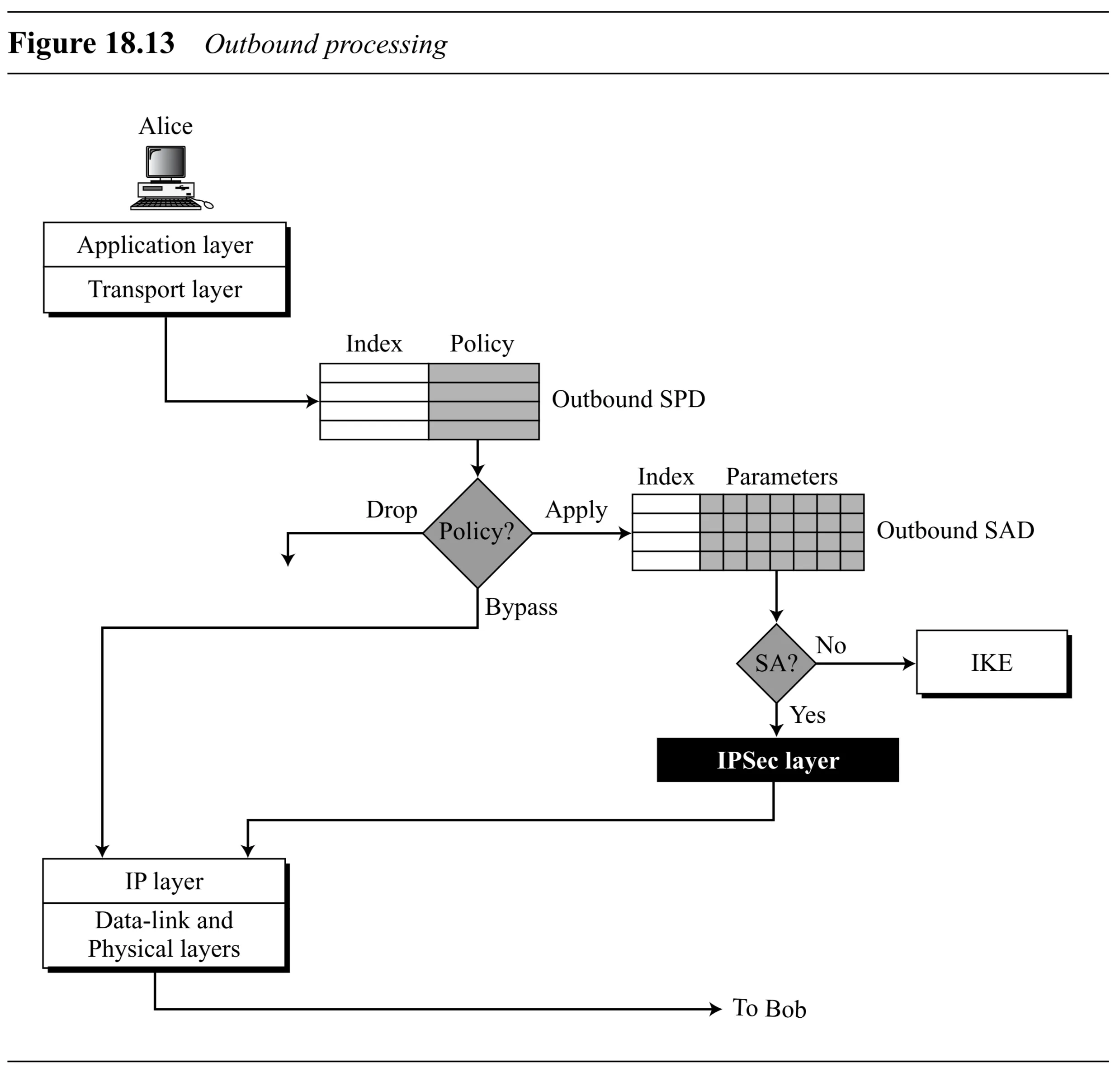
- Packet selectors (source/dest IP, ports, protocol) are used to find a matching policy in the outbound SPD.
- The output of the SPD lookup determines the action:
- Drop: Policy dictates the packet should be discarded.
- Bypass: Policy dictates IPSec is not needed for this packet. Packet is sent without IPSec processing.
- Apply: Policy dictates IPSec must be applied.
- If matching Outbound SA exists in SAD: Retrieve the SA parameters (identified by the policy, perhaps via an SA pointer in the SP entry). Apply AH/ESP processing using the SA. Transmit the packet.
- If no matching Outbound SA exists: The Internet Key Exchange (IKE) protocol is invoked to negotiate and establish the required SA(s) (both outbound for the source and inbound for the destination). Once established, the new outbound SA is added to the SAD, and processing continues as above.
Inbound SPD Processing
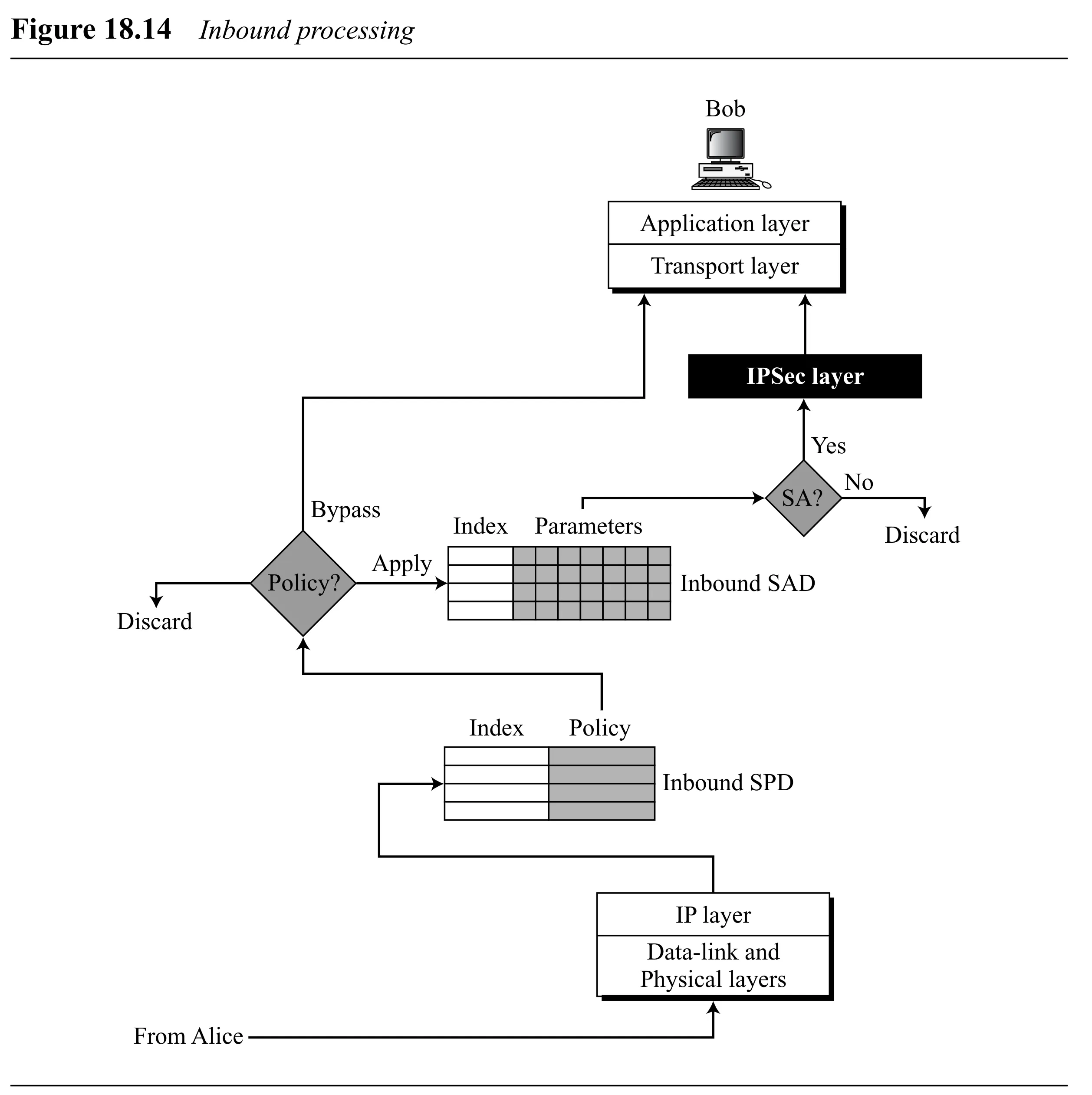
- Packet selectors are used to find a matching policy in the inbound SPD.
- The output of the SPD lookup determines the action:
- Discard: Policy dictates the packet should be dropped (even if it arrived with IPSec headers).
- Bypass: Policy dictates IPSec is not expected for this packet. If the packet arrived with IPSec headers, they might be ignored (or it could be an error condition depending on specifics). Packet is delivered to the transport layer (or next processing step).
- Apply: Policy dictates IPSec processing is required.
- If packet arrived without IPSec headers: Discard the packet (policy requires IPSec, but it wasn’t applied).
- If packet arrived with IPSec headers:
- Use the triple index (SPI, Dest Addr, Protocol from IP header) to look up the corresponding inbound SA in the SAD.
- If matching Inbound SA exists: Perform IPSec verification (decryption, authentication check) using the SA parameters. If successful, discard the AH/ESP header/trailer and deliver the inner packet to the transport layer. If verification fails, discard the packet.
- If no matching Inbound SA exists: Discard the packet. (An SA should have been established previously).
18.5 INTERNET KEY EXCHANGE (IKE)
- Purpose: Protocol designed to negotiate, create, and manage Security Associations (SAs) for IPSec (both inbound and outbound).
- Trigger: Called when the SPD lookup indicates “Apply” but no suitable SA exists in the SAD.
- IKE creates SAs for IPSec.
- Complexity: IKE is complex and builds upon three other protocols
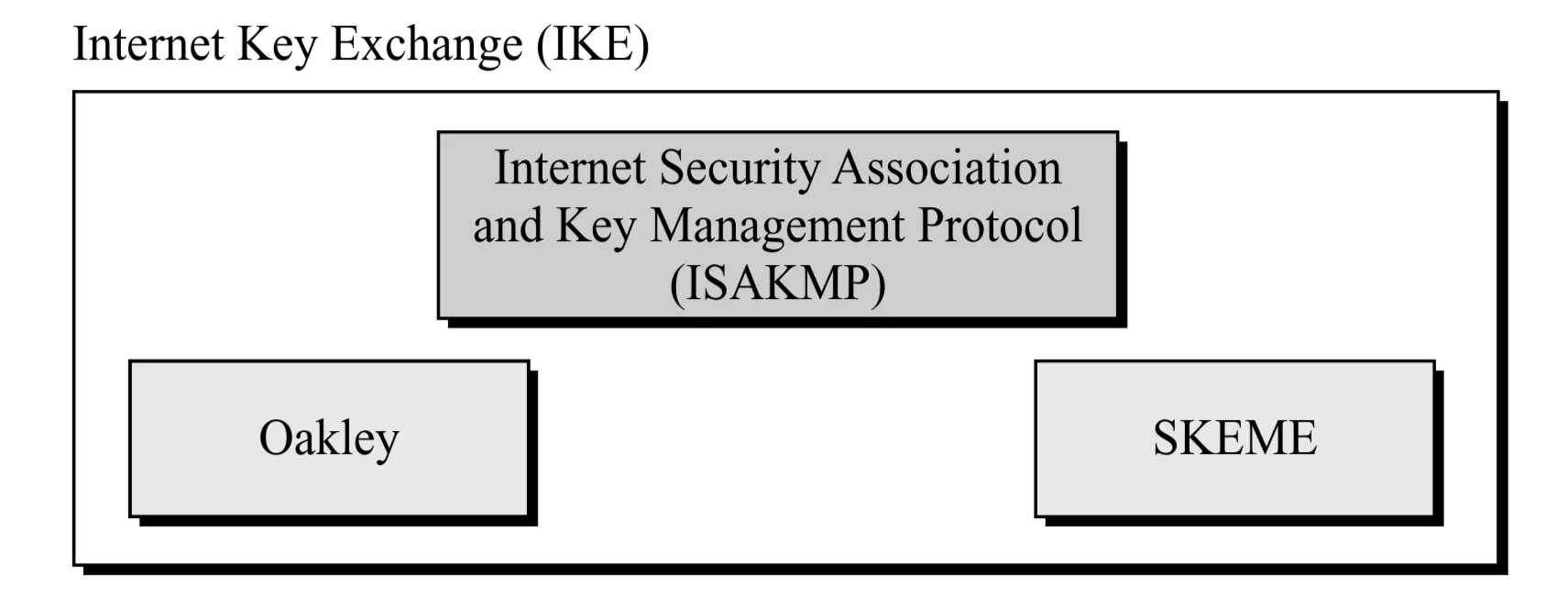
- Oakley: A key agreement protocol based on Diffie-Hellman, with improvements (e.g., cookies, nonces, authentication). Defines mechanisms but not message formats.
- SKEME: Another key exchange protocol, uses public-key encryption for entity authentication.
- ISAKMP (Internet Security Association and Key Management Protocol): Defines packet formats, message exchanges, and parameters to implement the key exchange mechanisms specified by IKE. ISAKMP is the carrier protocol for IKE exchanges.
Improved Diffie-Hellman Key Exchange
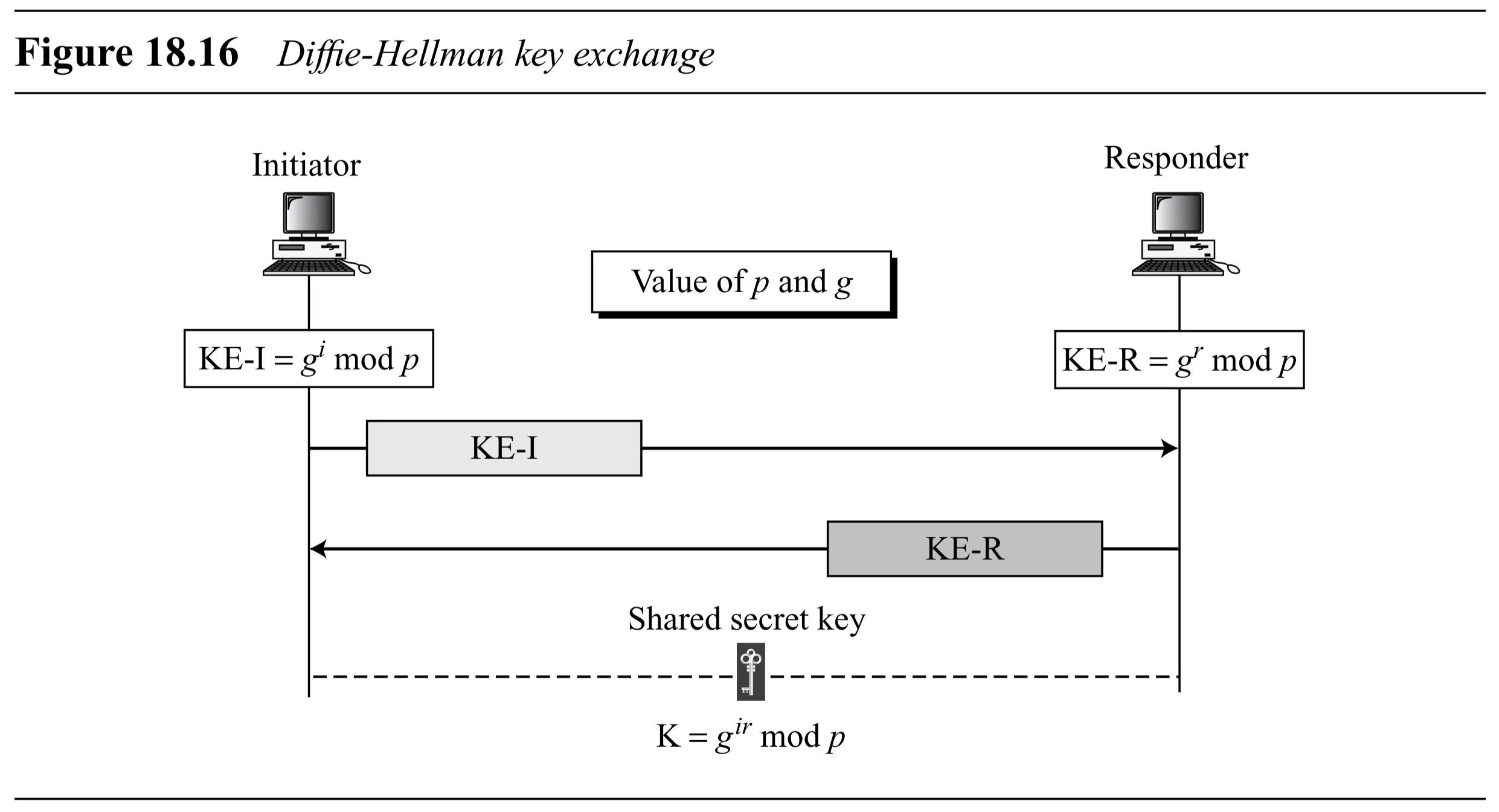
- IKE uses Diffie-Hellman as the basis for key exchange.
- Basic Diffie-Hellman (Figure 18.16):
- Agree on large prime and generator ( generates group ).
- Alice chooses random secret , computes , sends to Bob.
- Bob chooses random secret , computes , sends to Alice.
- Shared symmetric key .
- Weaknesses of Basic Diffie-Hellman:
- Clogging Attack (DoS): Attacker sends many fake half-keys () to Bob. Bob wastes CPU resources calculating responses () and full keys ().
- Replay Attack: Attacker records messages from one session and replays them later.
- Man-in-the-Middle Attack: Eve intercepts messages, establishes separate keys with Alice () and Bob (), and relays messages, potentially modifying them.
- IKE Improvements (based on Oakley/SKEME ideas):
- Cookies for Clogging Attack Prevention (Figure 18.17):
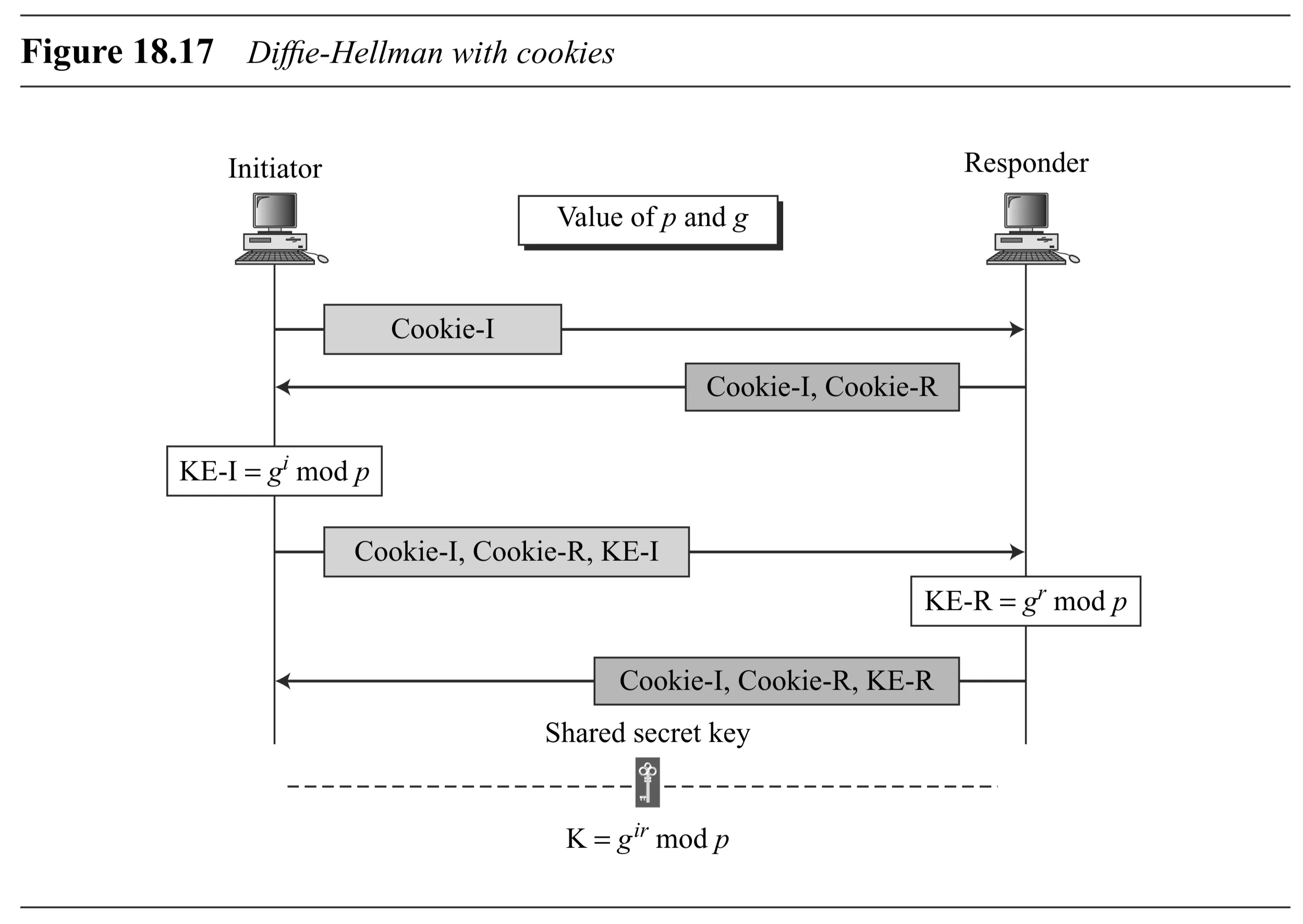
- Parties exchange cookies in initial messages before performing expensive Diffie-Hellman calculations.
- Cookie = Hash(Peer Identifier (IP, port, etc.), Local Secret, Timestamp).
- Initiator sends Cookie-I. Responder sends Cookie-R (and repeats Cookie-I). Initiator sends KE-I (and repeats Cookie-I, Cookie-R).
- If a peer is fake (e.g., spoofed IP), it won’t receive the cookie response and cannot proceed. The legitimate peer avoids computation until cookies are verified (by receiving them back).
- To protect against clogging attack, IKE uses cookies.
- Nonces for Replay Attack Prevention:
- Parties exchange unpredictable random numbers (nonces) in later messages (e.g., messages 3 & 4 in Main Mode).
- Nonces ensure freshness and are included in cryptographic calculations (hashes, keys).
- To protect against replay attack, IKE uses nonces.
- Authentication for Man-in-the-Middle Prevention:
- Parties must authenticate themselves and the integrity of messages exchanged.
- Requires each party to prove possession of a secret.
- To protect against man-in-the-middle attack, IKE requires that each party shows that it possesses a secret.
- Types of Secrets in IKE: a. Preshared Secret Key: Symmetric key known only to the two parties beforehand. b. Public/Private Key Pair (Encryption): Party proves identity by decrypting a message encrypted with its public key. c. Public/Private Key Pair (Digital Signature): Party proves identity by signing a message with its private key, verifiable with its public key.
- Cookies for Clogging Attack Prevention (Figure 18.17):
IKE Phases
- To avoid an infinite loop of needing SAs to create SAs, IKE is divided into two phases:
- Phase I: Establishes a secure, authenticated channel between the two IKE peers. Creates the IKE SA (or ISAKMP SA). This phase is generic.
- Phase II: Uses the secure channel (IKE SA) established in Phase I to negotiate SAs for other protocols, typically IPSec (AH/ESP). This phase is specific to the protocol needing the SA.
- Phase I Protection: Phase I messages themselves are initially unprotected but become progressively protected as keys are derived and authentication occurs during the exchange.
Phases and Modes
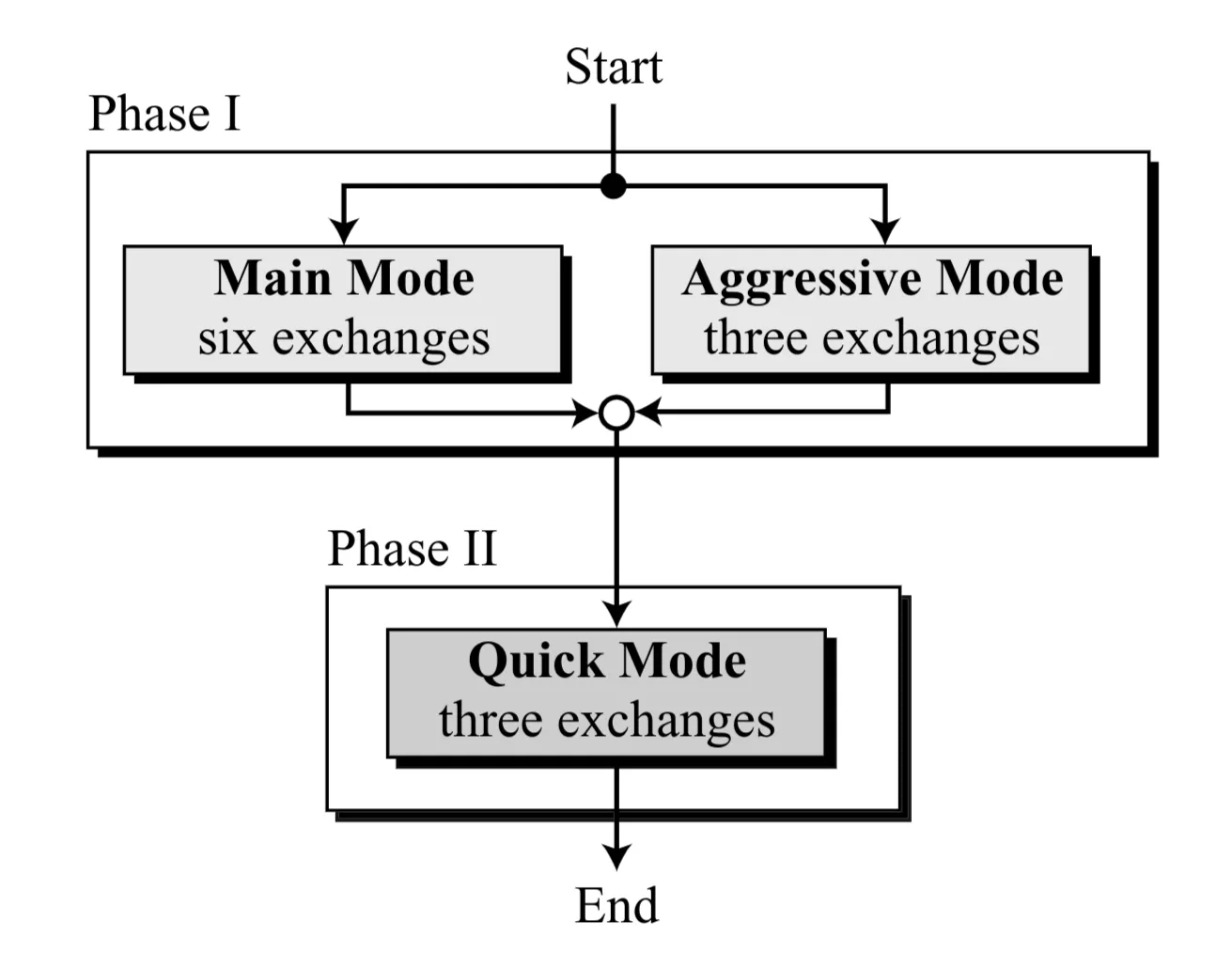
- Phase I Modes:
- Main Mode: Provides identity protection for peers. Involves six messages.
- Aggressive Mode: Faster, fewer messages (three messages). Does not provide identity protection during the exchange.
- Phase II Mode:
- Quick Mode: Used to negotiate IPSec SAs under the protection of the Phase I IKE SA. Involves three messages.
Phase I Authentication Methods
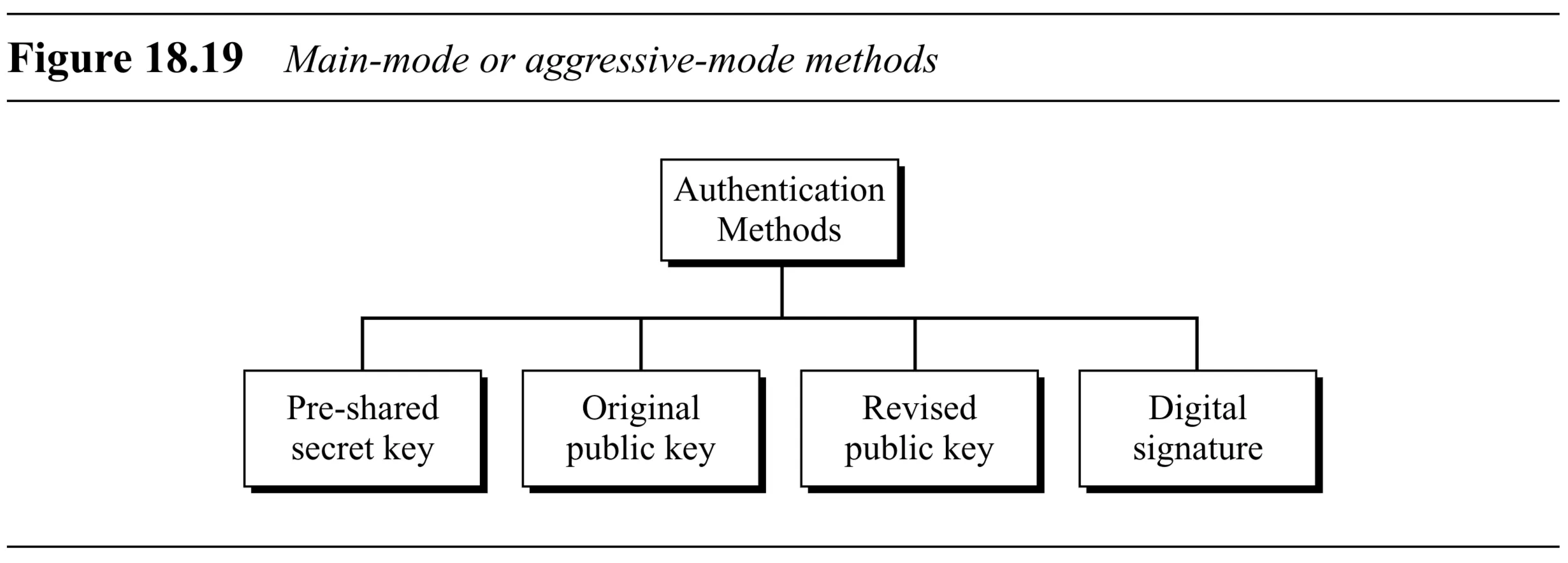 Based on the type of pre-existing secret, Phase I (Main or Aggressive mode) can use one of four authentication methods:
Based on the type of pre-existing secret, Phase I (Main or Aggressive mode) can use one of four authentication methods:
- Preshared Secret Key
- Original Public Key (using public key encryption for nonce/ID)
- Revised Public Key (using public key encryption only for nonce, derives temporary key)
- Digital Signature
Phase I: Main Mode (6 Messages)
- Messages 1 & 2: Exchange cookies (in ISAKMP header), negotiate Phase I SA parameters (encryption/hash algorithms, Diffie-Hellman group, authentication method). Initiator proposes, Responder chooses. Establishes peer liveness (no clogging).
- Messages 3 & 4: Exchange Diffie-Hellman public values (, ) and nonces (, ). Other method-specific data may be included (e.g., IDs in some public key methods).
- Key Calculation: After message 4, both parties can calculate the shared secret Diffie-Hellman key . From this, several keys are derived using a pseudorandom function (prf) (e.g., HMAC):
- : Base keying material, calculation depends on auth method:
- Preshared:
- Public Key (Orig/Rev):
- Signature:
- : Key used for deriving further keys.
- : Key used for authenticating Phase I messages.
- : Key used for encrypting Phase I messages (after message 4).
- : Base keying material, calculation depends on auth method:
- Hash Calculation (Authentication): Both parties calculate hashes to authenticate each other and the exchange. Hashes depend on the authentication method, but generally:
- is the initiator’s proposed SA payload. / are initiator/responder identities. Using protects the initiator’s proposal from modification.
- Messages 5 & 6: Exchange identities (, ) and the calculated hashes (, ) for authentication. These messages are encrypted using . Each party verifies the received hash using its own calculated version.
Main Mode: Preshared Secret-Key Method (Figure 18.20)
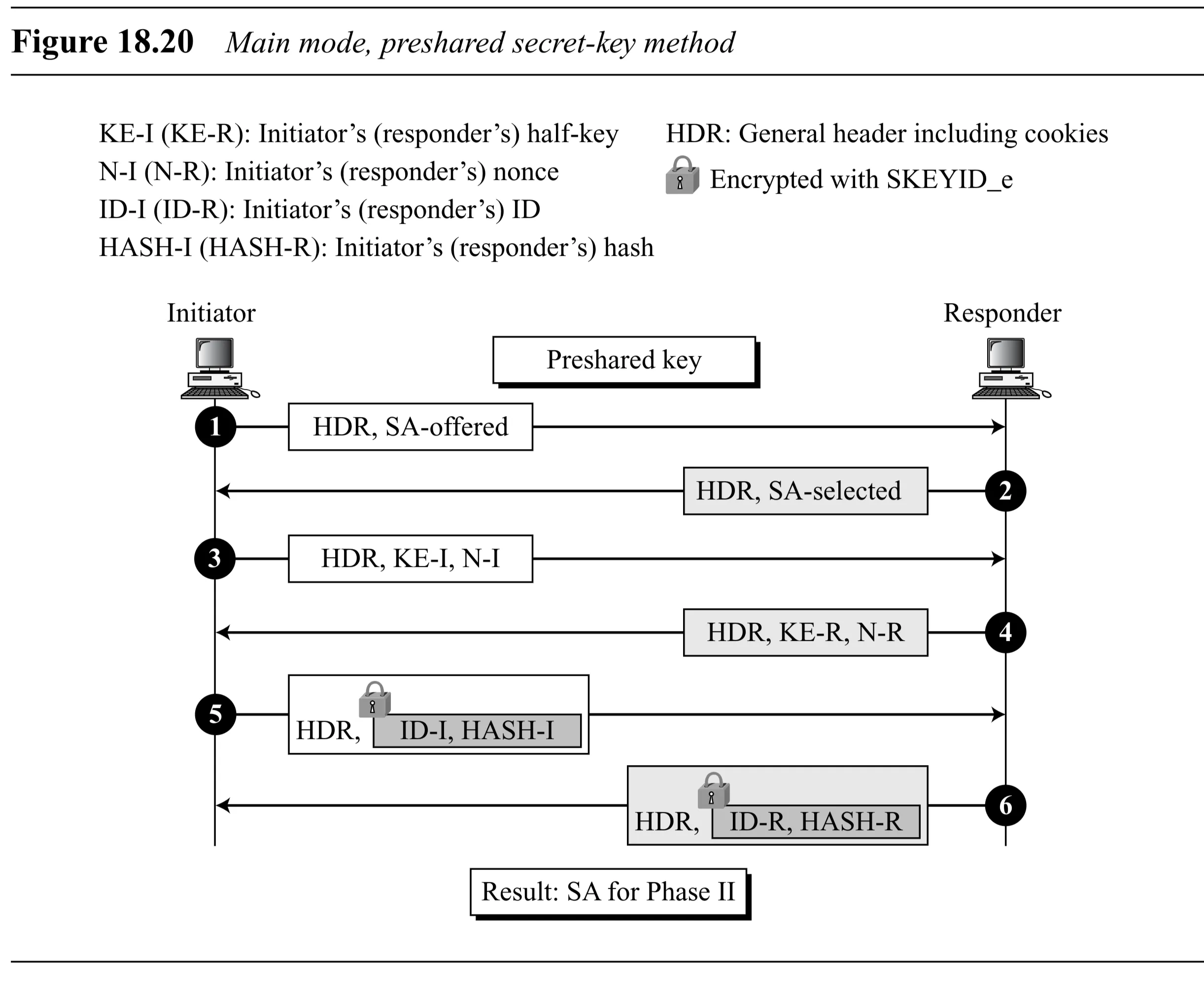
- Secret: Preshared symmetric key.
- Messages 1-4: Exchange cookies, SA params, nonces, DH values.
- Messages 5 & 6: Exchange encrypted IDs and Hashes (, ). derived from preshared key and nonces.
- Issue: Responder needs Initiator’s ID to know which preshared key to use for calculation before decrypting message 5 which contains the ID. Often assumes ID = IP address (problematic for mobile hosts).
Main Mode: Original Public-Key Method (Figure 18.21)
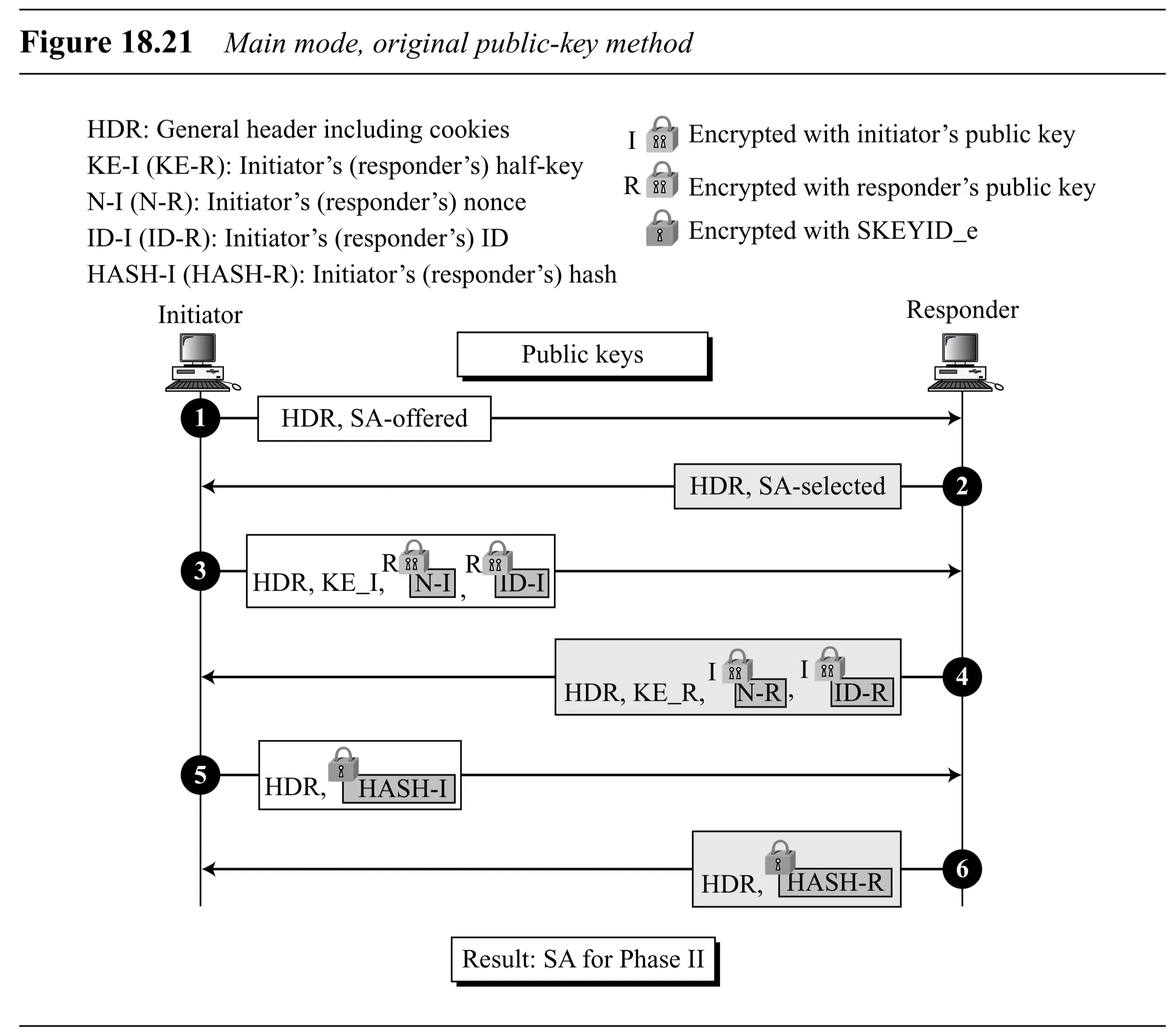
- Secret: Pre-known public/private key pairs for encryption/decryption.
- Messages 1 & 2: Cookies, SA params.
- Messages 3 & 4: Exchange DH values. Also exchange Nonces and IDs, encrypted with the recipient’s public key.
- Messages 5 & 6: Exchange Hashes (, ), encrypted with .
- derived from nonces and DH key . Authentication relies on the fact that only the legitimate owner of the private key could decrypt the nonce/ID needed to compute the correct and subsequent hashes. Uses double hashing (hash of nonces as key for HMAC).
Main Mode: Revised Public-Key Method (Figure 18.22)
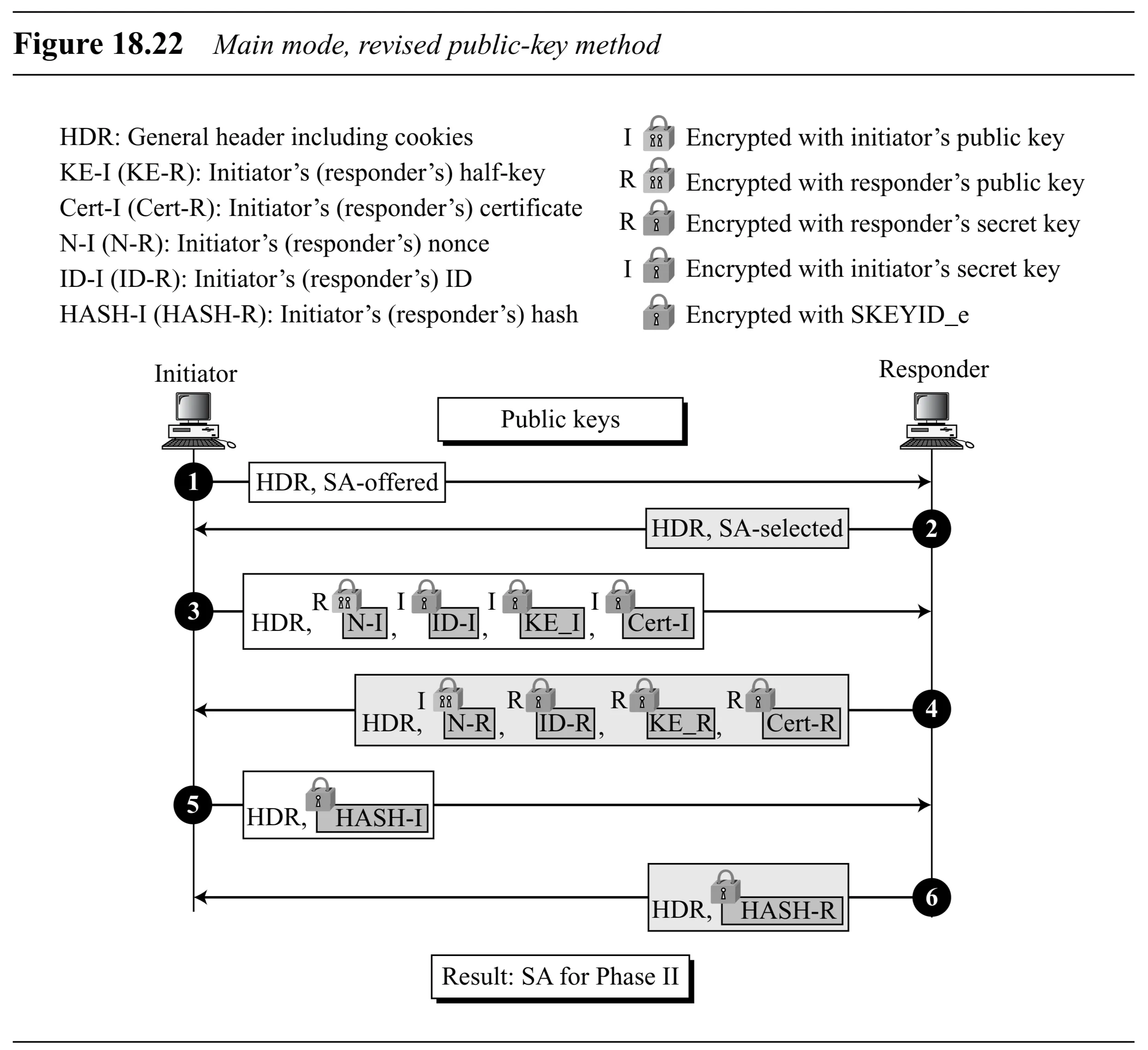
- Secret: Public/private key pairs, but public key crypto used only to establish temporary secrets. Certificates (Cert-I, Cert-R) may be exchanged.
- Messages 1 & 2: Cookies, SA params.
- Messages 3 & 4: Exchange DH values, IDs, and Nonces. Initiator encrypts and with Responder’s public key (R). Responder encrypts and with Initiator’s public key (I). Optional certificates are sent encrypted with derived .
- Temporary Keys: , . These might be used for encrypting parts of messages 3/4 (details complex).
- Messages 5 & 6: Exchange Hashes (, ), encrypted with .
- Reduces public key operations compared to original method.
Main Mode: Digital Signature Method (Figure 18.23)
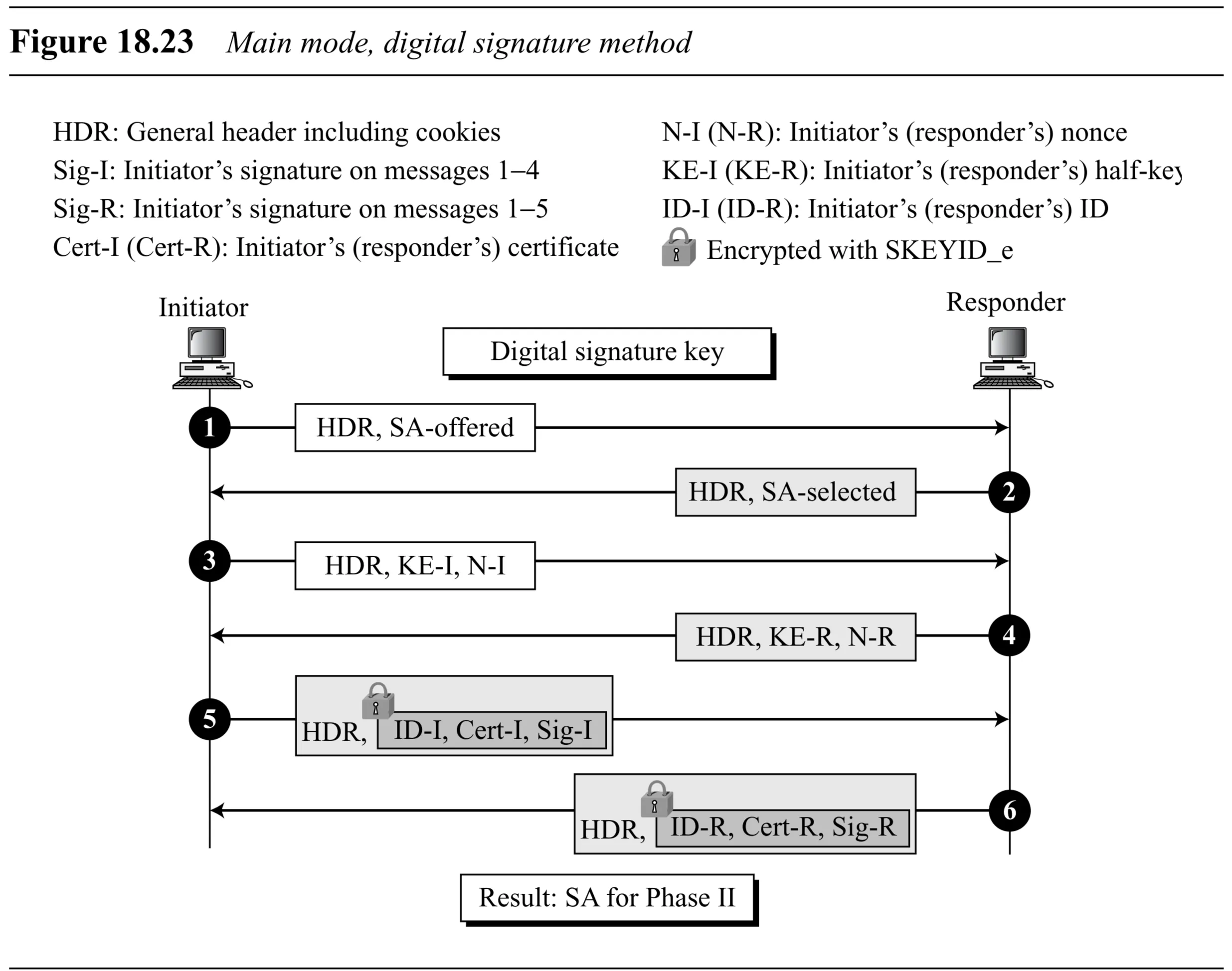
- Secret: Public/private key pairs for signing. Certificates (Cert-I, Cert-R) often used.
- Messages 1-4: Exchange cookies, SA params, nonces, DH values.
- Messages 5 & 6: Exchange IDs, optional Certificates, and Signatures (, ). These are encrypted with .
- = Signature using Initiator’s private key over all data from messages 1-4.
- = Signature using Responder’s private key over all data from messages 1-5.
- derived from hash of nonces and cookies. Authentication comes from verifying the signatures using the sender’s public key (obtained from certificate or pre-known).
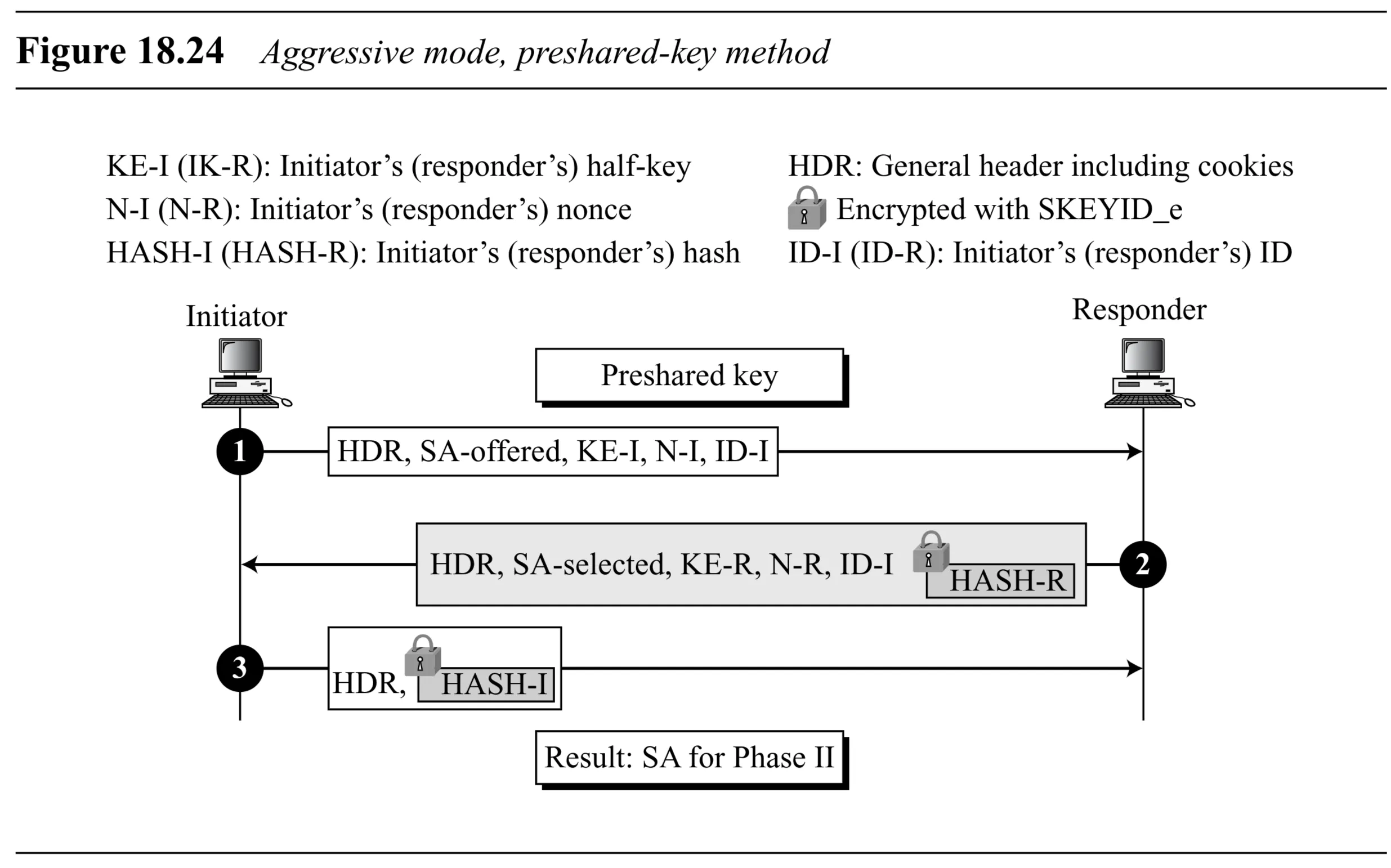
Phase I: Aggressive Mode (3 Messages)
- Compressed version of Main Mode. Faster, but exposes identities.
- Message 1: Initiator sends Cookie-I, SA proposal, KE-I, N-I, ID-I.
- Message 2: Responder sends Cookie-R (and Cookie-I), chosen SA, KE-R, N-R, ID-R, and authentication payload (e.g., HASH-R or Sig-R).
- Message 3: Initiator sends authentication payload (e.g., HASH-I or Sig-I).
- Key calculation and authentication happen similarly, but timings differ. Responder can authenticate after message 1 (if using signatures/public keys) or message 3 (if using preshared keys). Initiator authenticates after message 2.
Aggressive Mode Methods (Figures 18.24-18.27)
-
Preshared-Key (Fig 18.24): Similar flow, HASH-R in Msg 2, HASH-I (encrypted) in Msg 3.
-
Original Public-Key (Fig 18.25): Nonces/IDs encrypted with public keys in Msgs 1 & 2. HASH-R in Msg 2, HASH-I (encrypted) in Msg 3.
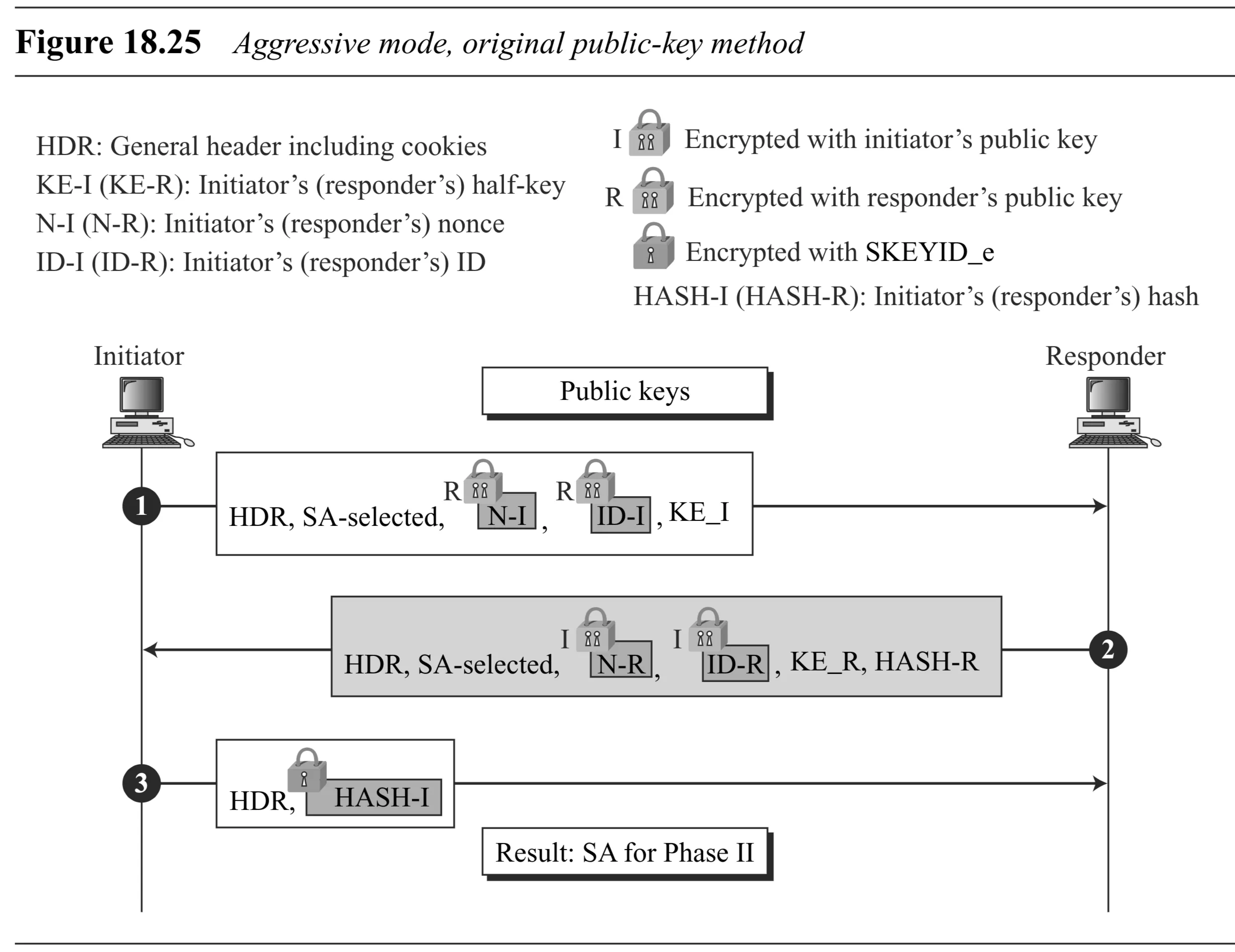
-
Revised Public-Key (Fig 18.26): Nonces/IDs encrypted with public keys, temporary keys derived. Certs exchanged. HASH-R in Msg 2, HASH-I (encrypted) in Msg 3.
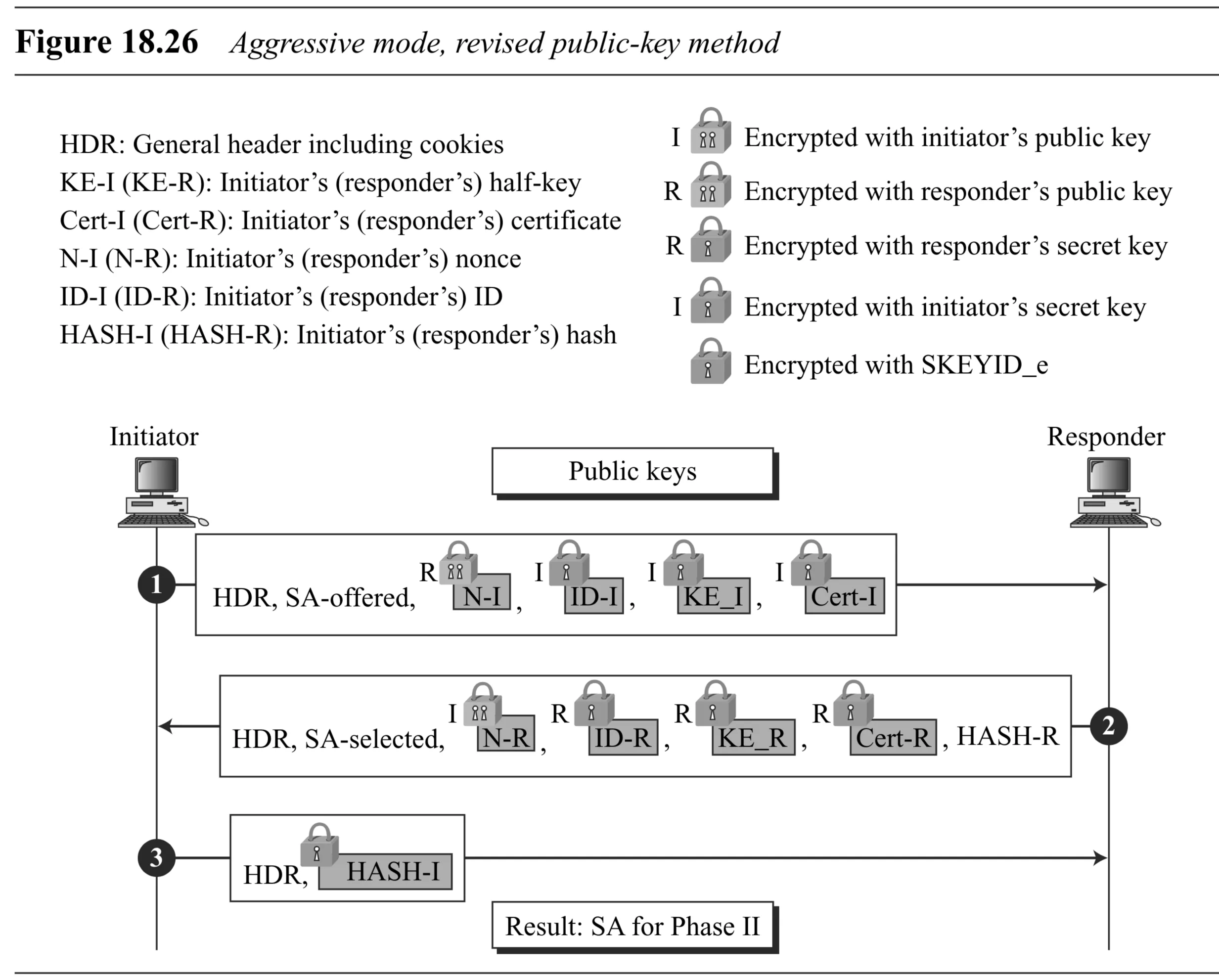
-
Digital Signature (Fig 18.27): Sig-R in Msg 2, Sig-I (encrypted) in Msg 3.
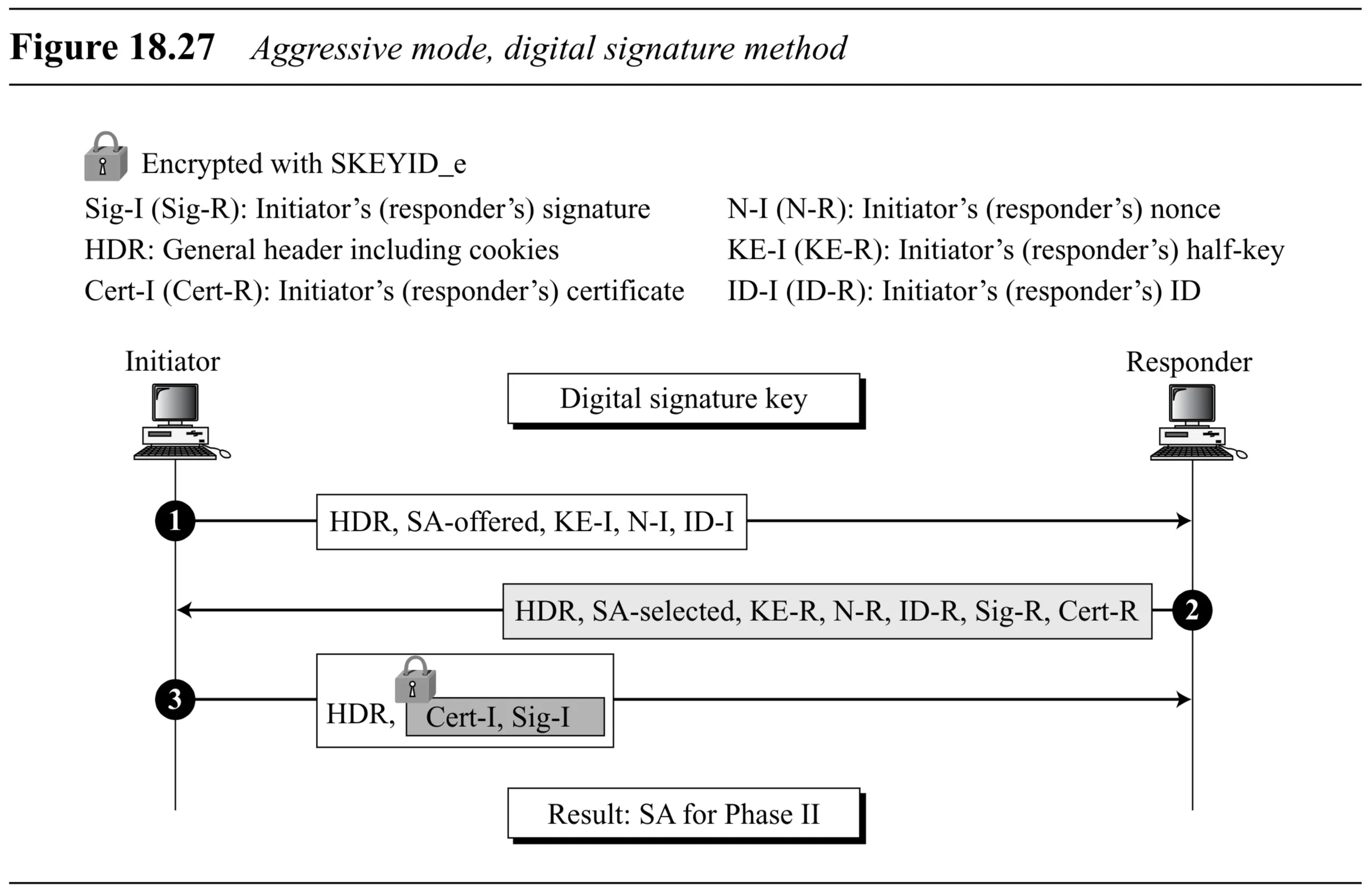
Phase II: Quick Mode (3 Messages)
-
Purpose: Negotiate SAs for data protocols (like IPSec AH/ESP).
-
Protection: Runs under the protection of the Phase I IKE SA (uses and from Phase I).
-
Initiator: Either party from Phase I can initiate Phase II.
-
Messages (Figure 18.28): All messages are encrypted using from Phase I.
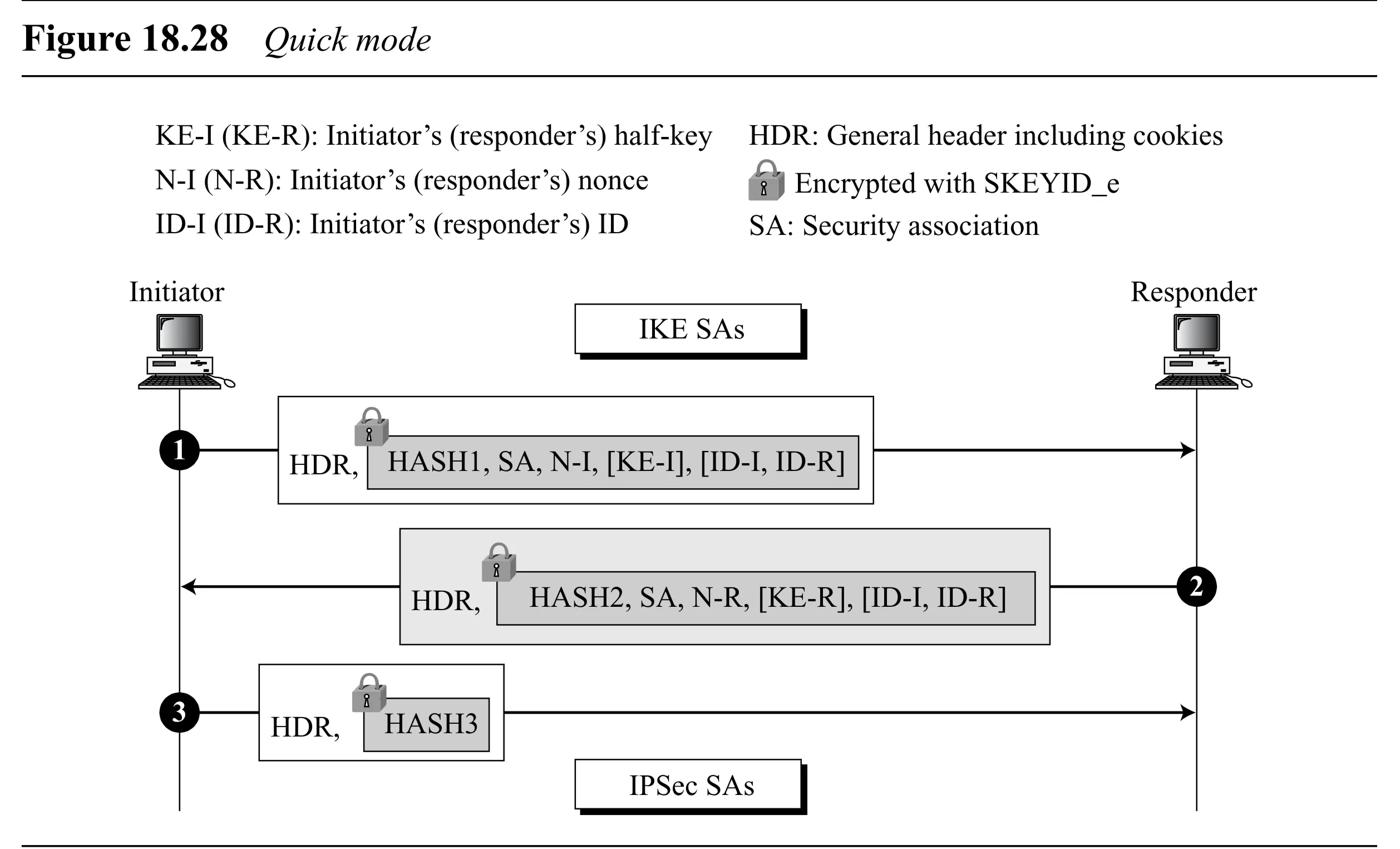
- Initiator → Responder: , SA proposal (for IPSec), , [optional for PFS ], [optional for selectors].
- Responder → Initiator: , chosen SA, , [optional for PFS], [optional ].
- Initiator → Responder: .
-
Authentication: Uses keyed HMACs derived from Phase I keys: Quick Mode Hash 1: Quick Mode Hash 2: Quick Mode Hash 3:
MsgIDis a unique identifier for this Quick Mode exchange (from ISAKMP header), prevents collisions.
-
Perfect Forward Security (PFS) - Optional:
- If PFS is desired, an additional Diffie-Hellman exchange () occurs during Quick Mode.
- The resulting new shared secret is mixed into the key derivation for the IPSec keys.
- Ensures that compromising the Phase I long-term keys () does not compromise the keys for IPSec SAs negotiated with PFS enabled.
- Requires deleting the temporary DH key () immediately after use.
Key Materials (for IPSec SA)
- After Phase II Quick Mode completes, the key material for the new IPSec SA is derived:
- Without PFS:
- With PFS:
protocol= AH or ESP,SPI= SPI for the new IPSec SA, are nonces from Quick Mode.
- Unidirectional: Key derivation is done independently by both peers. Since the SPI value will differ for each direction of the IPSec SA, the resulting keys will be different for inbound and outbound traffic.
- Key Length: If the required key length for the chosen cipher is longer than the output of
prf, theprfis applied iteratively:- …
SA Algorithms (Negotiated in IKE)
- Diffie-Hellman Groups (Table 18.3): Defines the prime and generator (or elliptic curve parameters) for the DH exchange.
- Group 1: -bit modulus
- Group 2: -bit modulus
- Group 5: -bit modulus
- Group 3, 4: Elliptic Curve groups (-bit, -bit fields)
- Hash Algorithms (Table 18.4): Used for authentication (PRF often based on these).
- MD5 (Value )
- SHA-1 (Value )
- Tiger (Value )
- SHA2-256, SHA2-384, SHA2-512 (Values )
- Encryption Algorithms (Table 18.5): Used for confidentiality (in ESP and IKE Phase 1 messages 5&6). Typically used in CBC mode.
- DES (Value )
- IDEA (Value )
- Blowfish (Value )
- RC5 (Value )
- 3DES (Value )
- CAST (Value )
- AES (Value )
18.6 ISAKMP (Internet Security Association and Key Management Protocol)
- Purpose: Defines the framework and packet formats for negotiating, establishing, modifying, and deleting SAs. It carries the IKE messages.
ISAKMP General Header
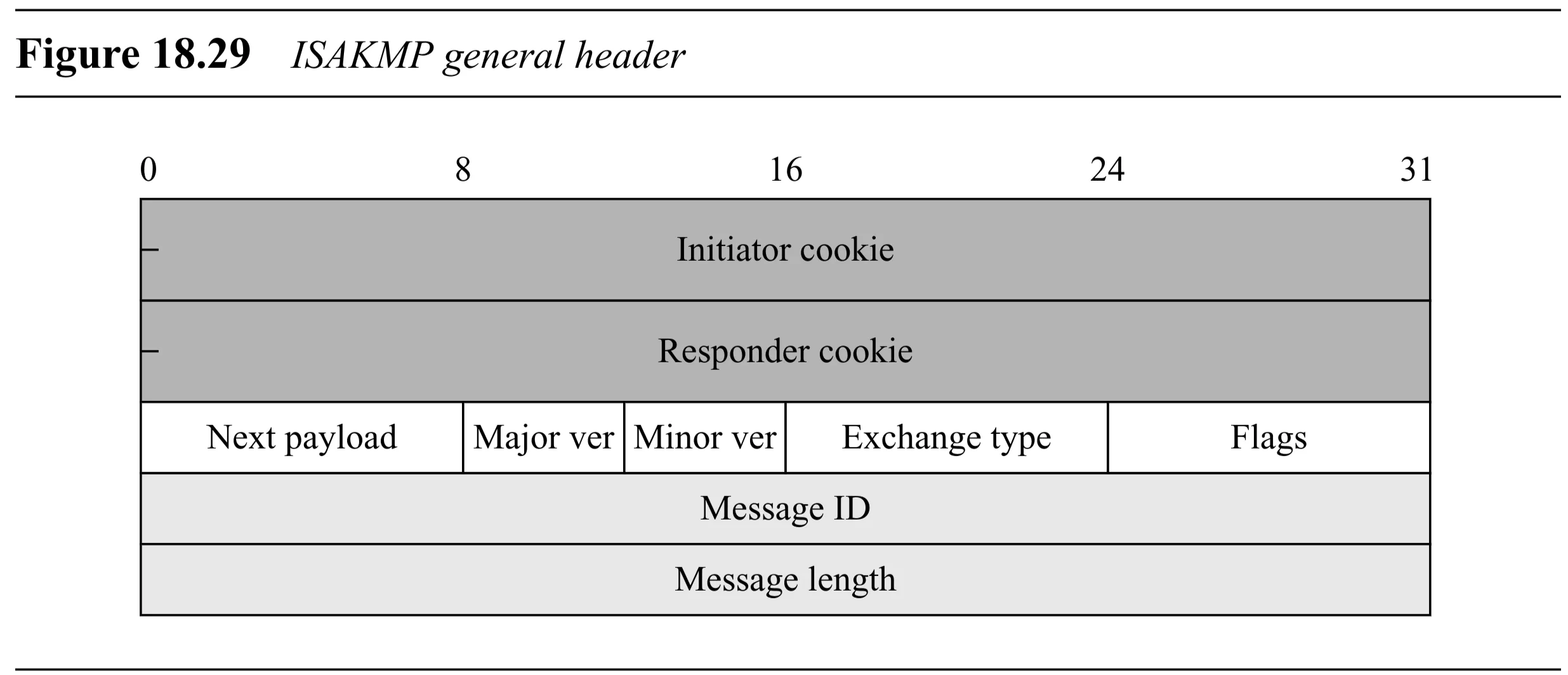
- Initiator Cookie ( bits): Unique value generated by the initiator of the SA establishment/notification/deletion. Helps identify the IKE SA state.
- Responder Cookie ( bits): Unique value generated by the responder. Value is in the first message from the initiator.
- Next Payload ( bits): Identifies the type of the first payload immediately following this header (See Table 18.6).
- Major Version ( bits): Current value is .
- Minor Version ( bits): Current value is .
- Exchange Type ( bits): Defines the type of IKE exchange being performed (e.g., Main Mode, Aggressive Mode, Quick Mode).
- Flags ( bits): Indicate options.
- Encryption bit (E): If set (), payloads following the header are encrypted.
- Commitment bit (C): If set (), indicates notification about encryption material not being received before SA establishment.
- Authentication bit (A): If set (), indicates the rest of the payload is authenticated for integrity (but not encrypted).
- Message ID ( bits): Unique ID used to identify messages within Phase II Quick Mode exchanges. Set to during Phase I.
- Message Length ( bits): Total length of the ISAKMP message (header + all payloads) in bytes.
ISAKMP Payloads
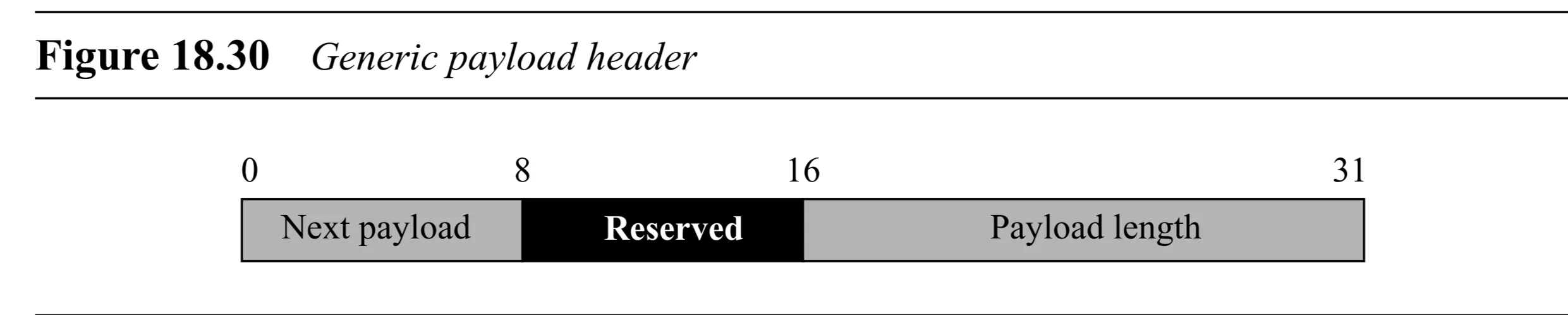
- Messages are constructed by chaining payloads after the general header.
- Generic Payload Header (Figure 18.30): Precedes each specific payload type.
- Next Payload ( bits): Identifies the type of the next payload in the chain. Value means this is the last payload.
- Reserved ( bits): Must be .
- Payload Length ( bits): Length of the current payload, including its generic header, in bytes.
- Payload Types (Table 18.6):
| Type | Name | Brief Description |
|---|---|---|
| None | Marks end of payloads. | |
| SA | Starts negotiation; contains proposals/transforms. | |
| Proposal | Contains information for one protocol during negotiation. | |
| Transform | Defines specific security attributes/algorithms. | |
| Key Exchange (KE) | Carries data for key generation (e.g., DH half-key). | |
| Identification (ID) | Carries peer identification information. | |
| Certificate (CERT) | Carries a public-key certificate. | |
| Certificate Req (CR) | Requests a certificate from the peer. | |
| Hash (HASH) | Carries hash output for authentication/integrity. | |
| Signature (SIG) | Carries digital signature output. | |
| Nonce (NONCE) | Carries random data for replay protection/liveliness. | |
| Notification (NOTIFY) | Carries error or status information. | |
| Delete (DELETE) | Indicates specific SAs have been deleted by the sender. | |
| Vendor ID (VENDOR) | Defines vendor-specific extensions. |
Specific Payload Formats (Selected)
-
SA Payload (Figure 18.31):
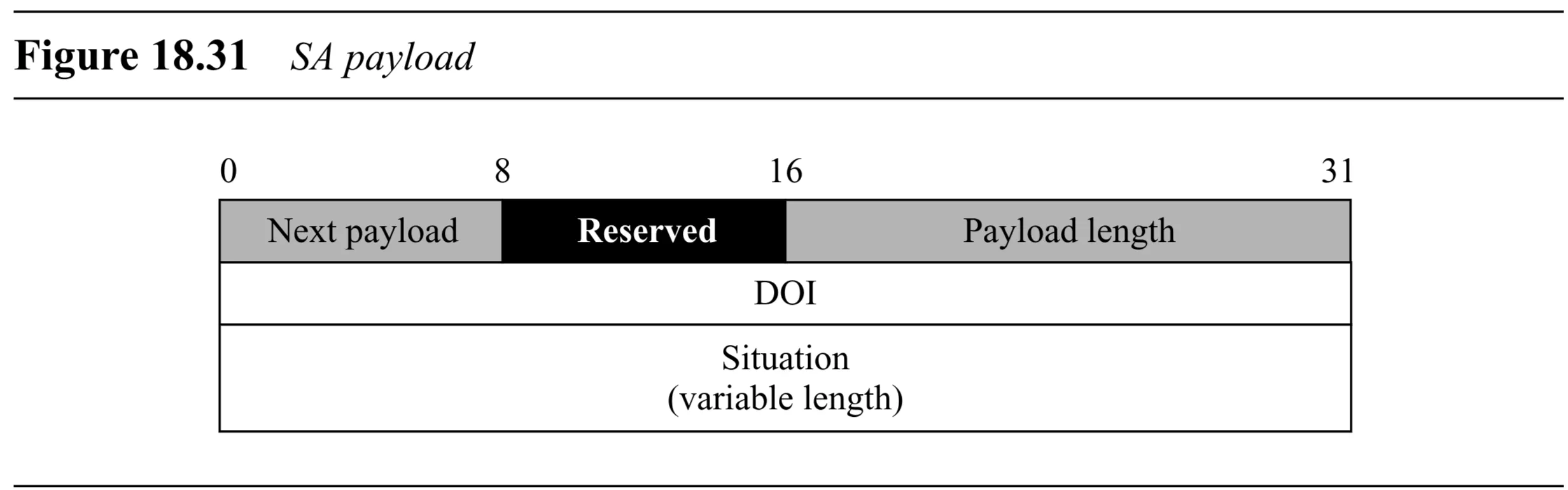
- Generic Header
- Domain of Interpretation (DOI) ( bits): Specifies context (e.g., for IPSec).
- Situation (variable length): Defines the context/situation for the negotiation.
- Followed by one or more Proposal payloads.
-
Proposal Payload (Figure 18.32):
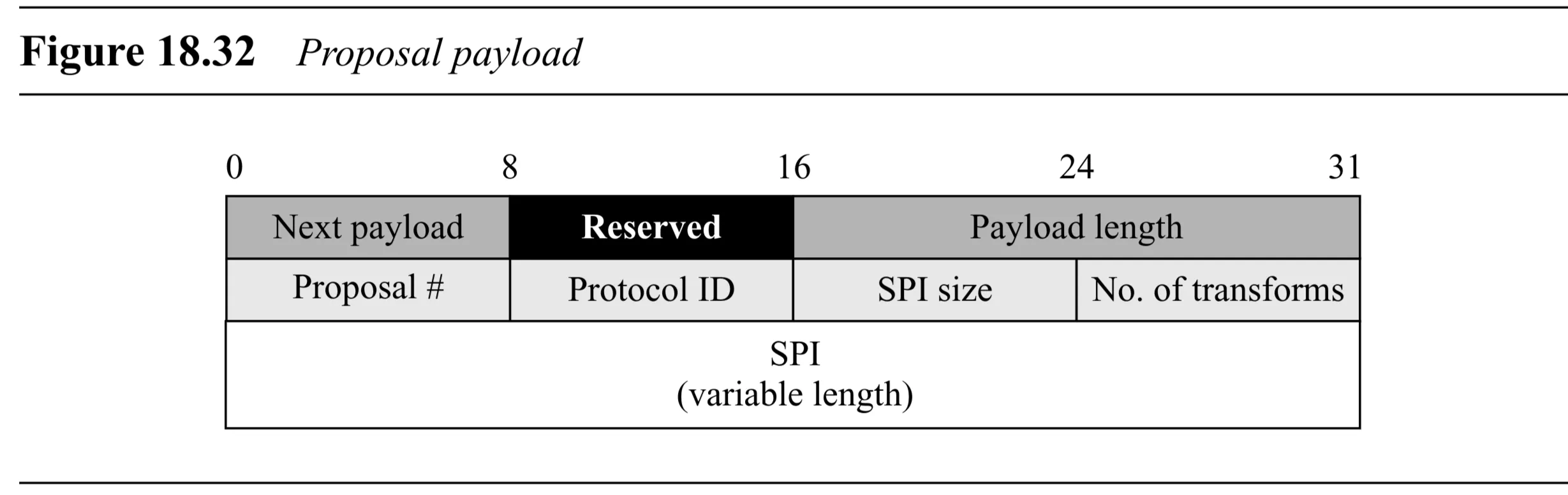
- Generic Header
- Proposal # ( bits): Number assigned by initiator.
- Protocol ID ( bits): Protocol for this proposal (e.g., =ISAKMP, =AH, =ESP).
- SPI Size ( bits): Size of the SPI for this protocol (bytes).
- Number of Transforms ( bits): How many Transform payloads follow for this proposal.
- SPI (variable length): The actual Security Parameter Index.
- Followed by one or more Transform payloads.
-
Transform Payload (Figure 18.33):
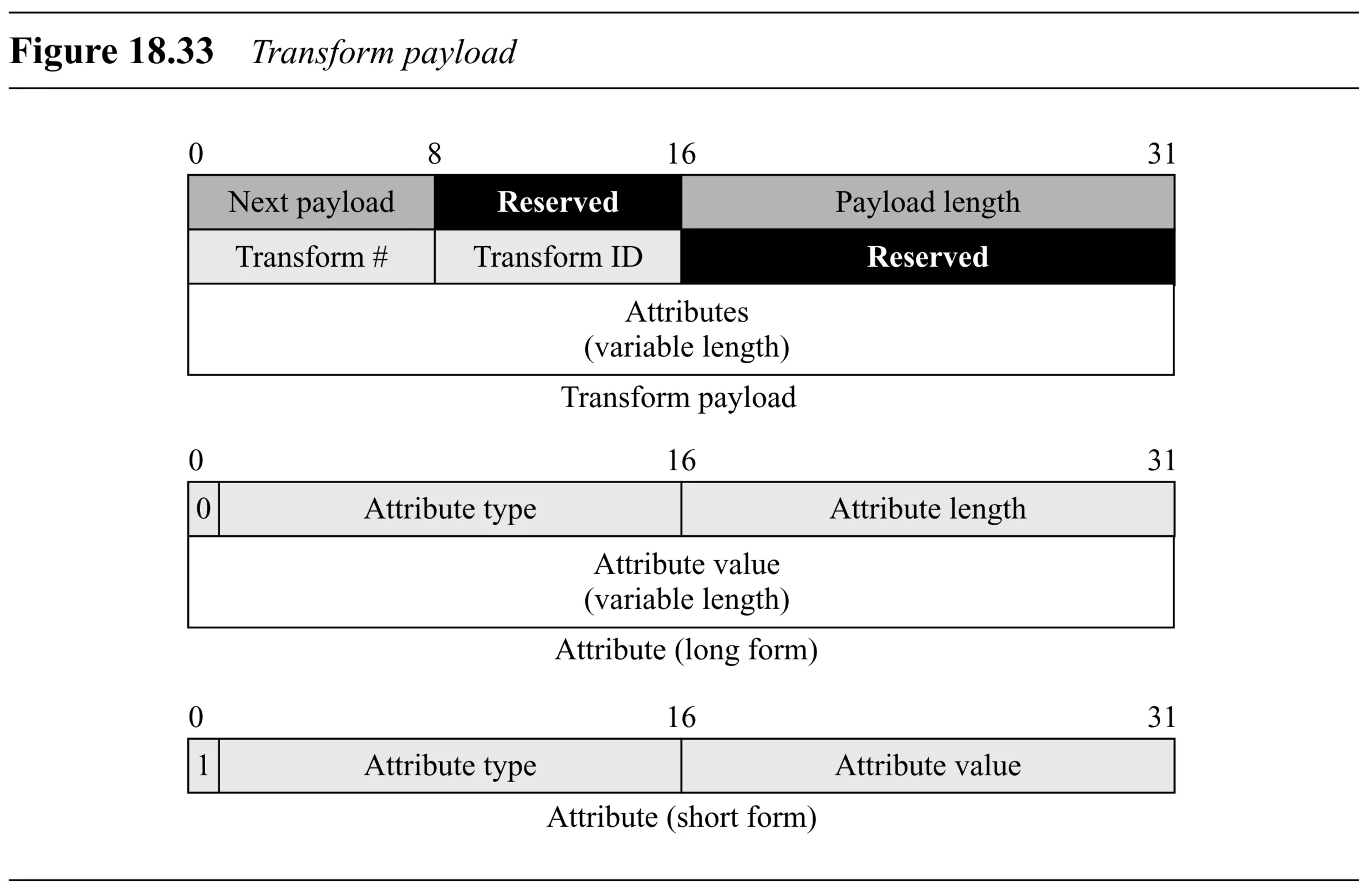
- Generic Header
- Transform # ( bits): Number for this transform within the proposal.
- Transform ID ( bits): Identifies the specific transform (e.g., encryption algorithm, hash algorithm).
- Reserved ( bits): Must be .
- SA Attributes (variable length): Carries specific attributes (e.g., key length, algorithm mode) as Type/Length/Value triplets. Can be short form (Type/Value) or long form (Type/Length/Value).
-
Key Exchange Payload (Figure 18.34):
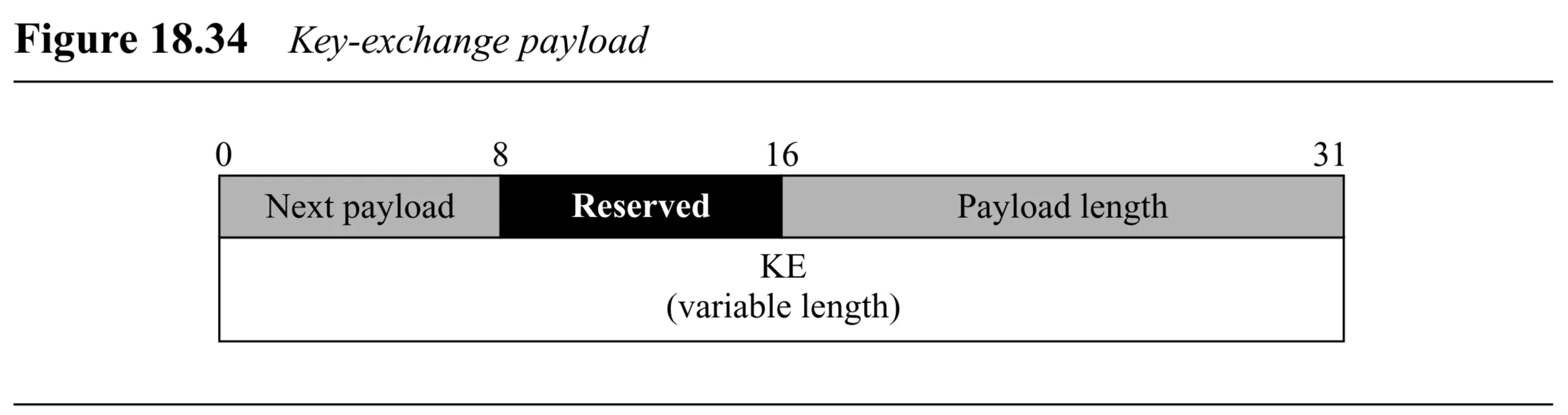
- Generic Header
- KE Data (variable length): Data needed for key creation (e.g., Diffie-Hellman public value ).
-
Identification Payload (Figure 18.35):
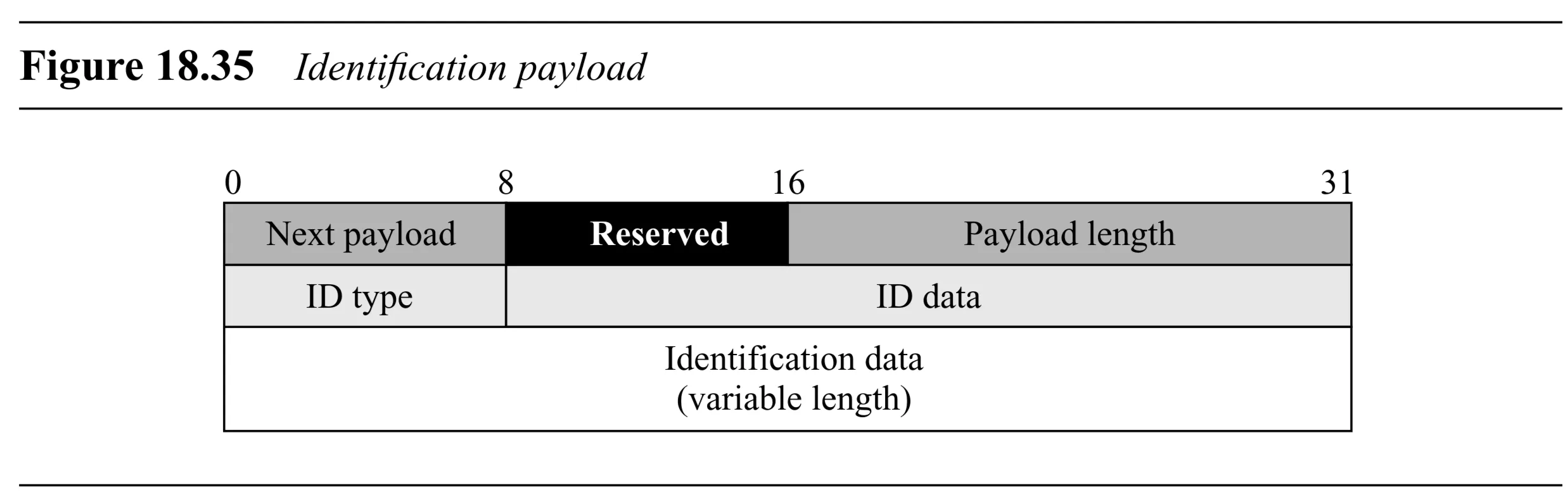
- Generic Header
- ID Type ( bits): Type of identifier (e.g., IP address, FQDN). DOI specific.
- ID Data ( bits): Usually .
- Identification Data (variable length): The actual identity value.
-
Certificate Payload (Figure 18.36):
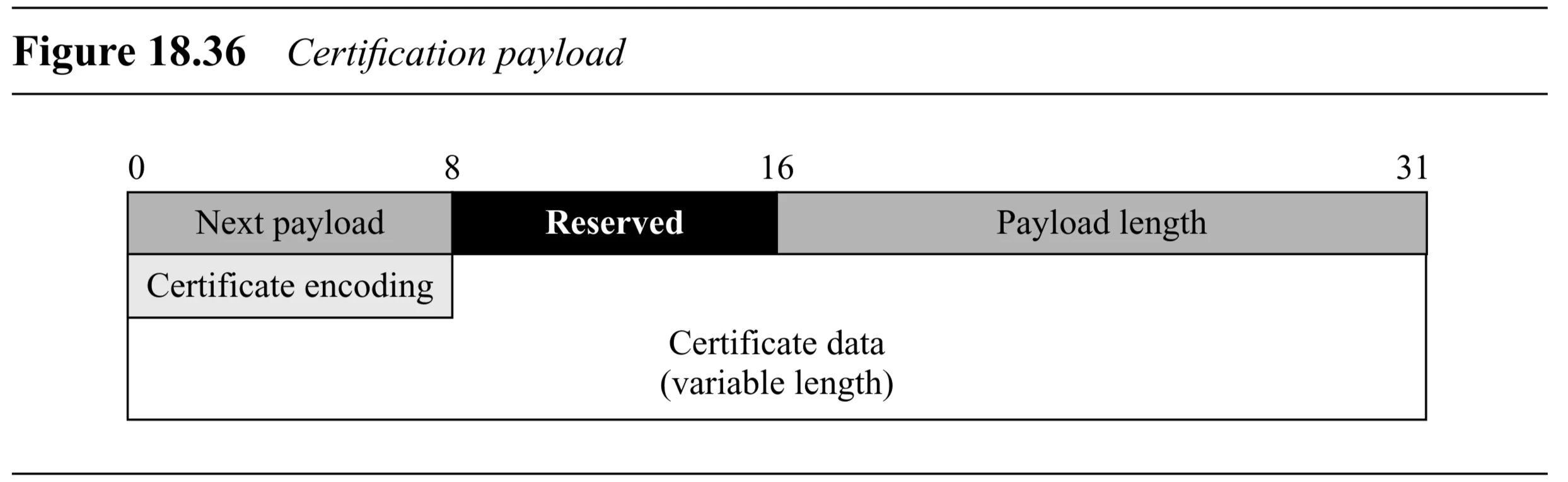
- Generic Header
- Certificate Encoding ( bits): Type of certificate
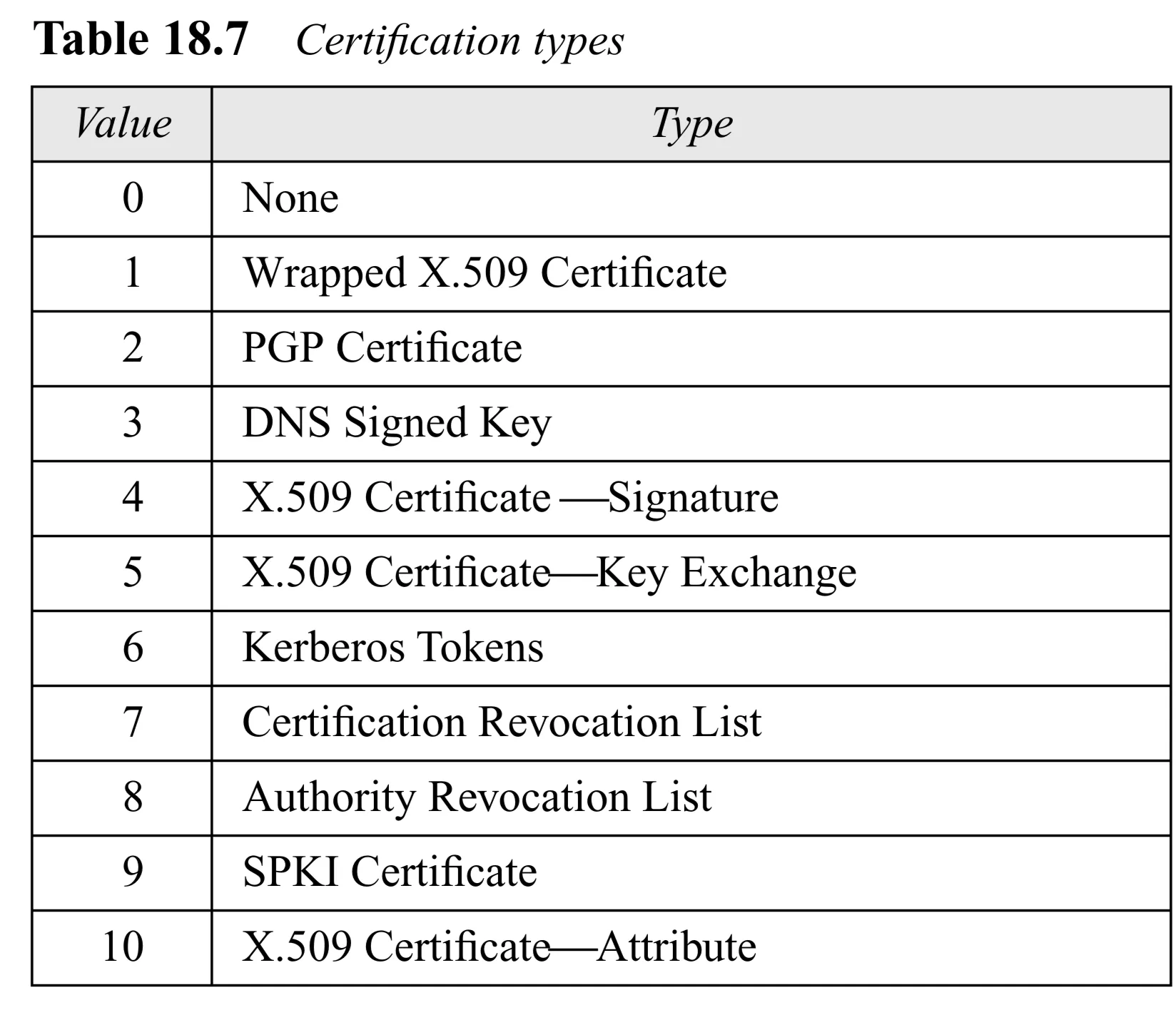
- Certificate Data (variable length): The actual certificate content.
-
Hash Payload (Figure 18.38):
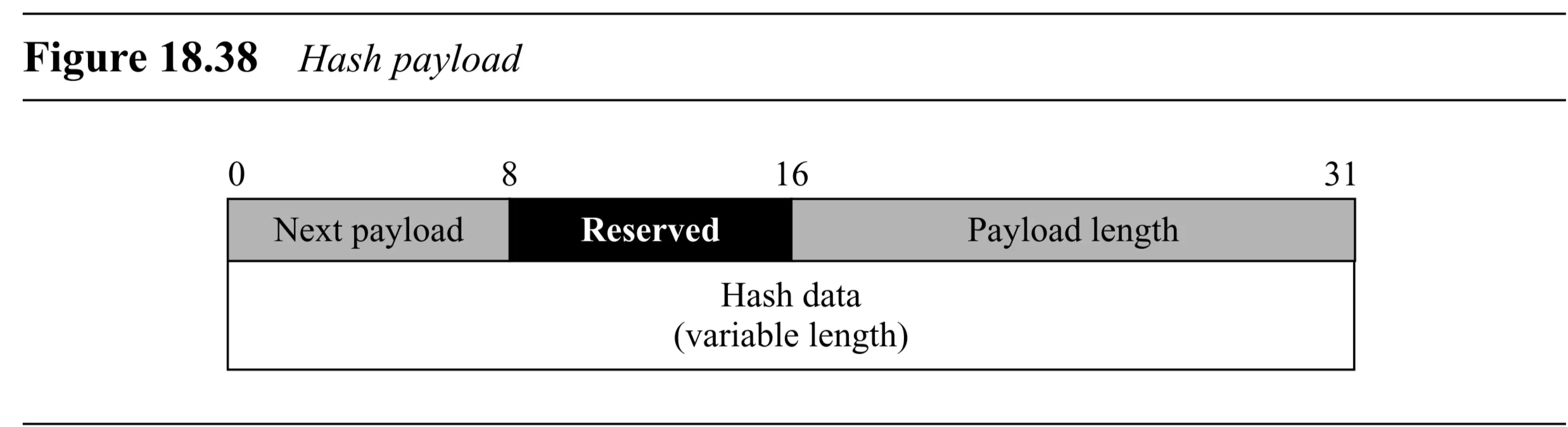
- Generic Header
- Hash Data (variable length): The calculated hash value.
-
Signature Payload (Figure 18.39):
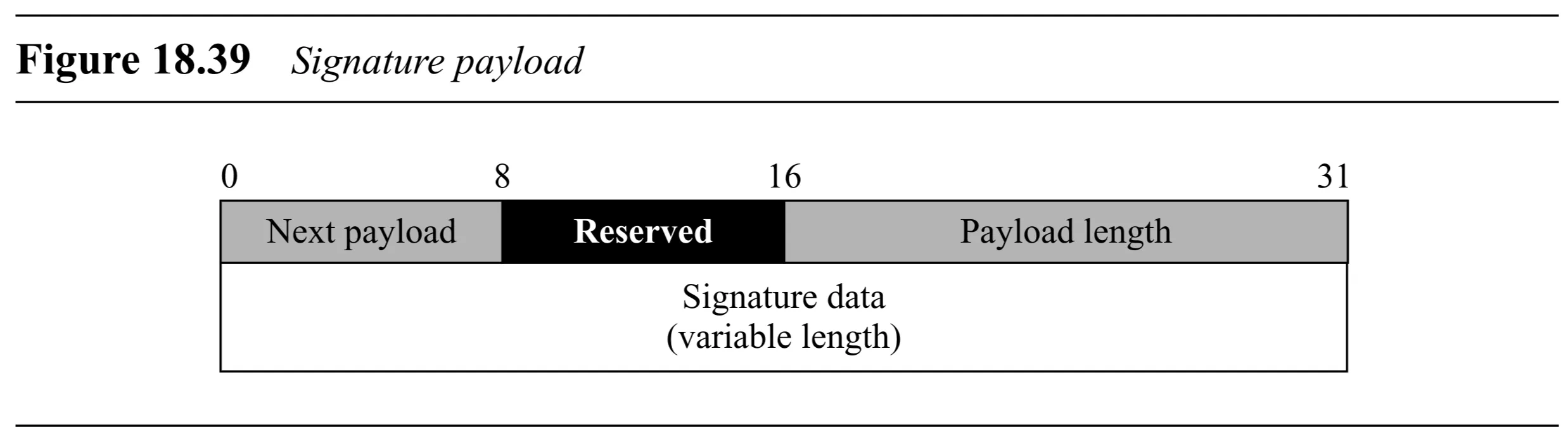
- Generic Header
- Signature Data (variable length): The calculated digital signature value.
-
Nonce Payload (Figure 18.40):
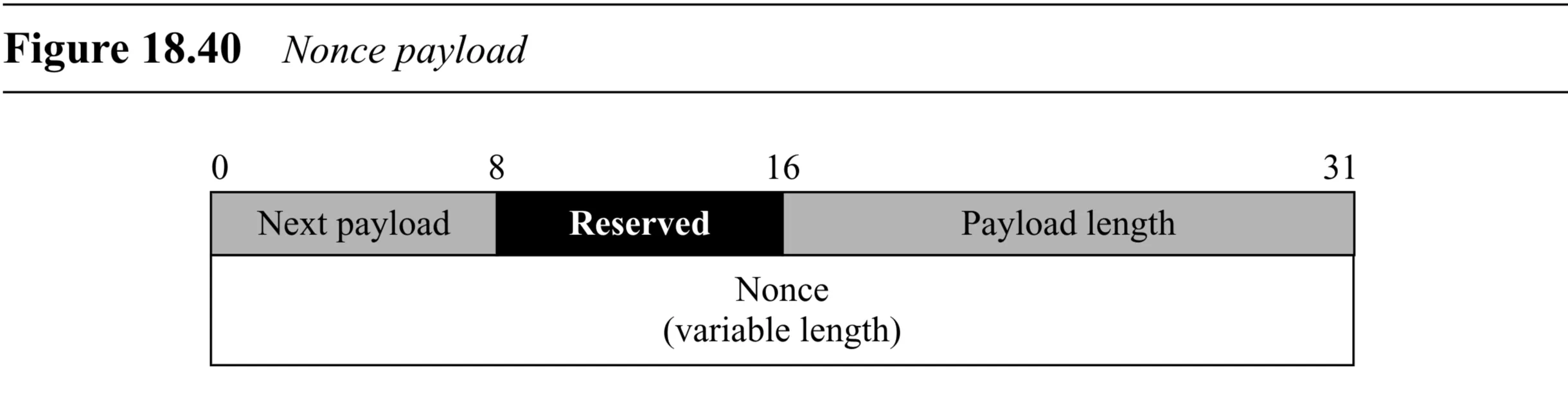
- Generic Header
- Nonce Data (variable length): The random nonce value.
-
Notification Payload (Figure 18.41):
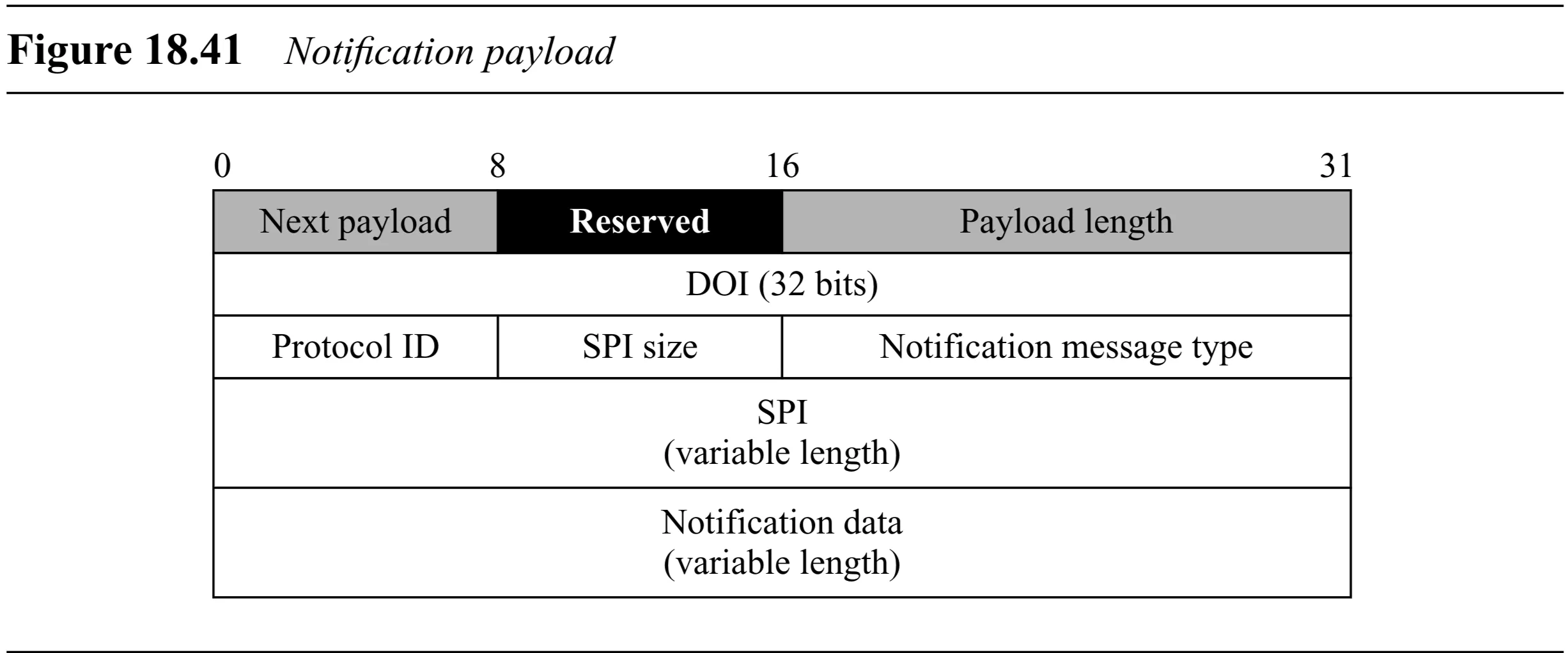
- Generic Header
- DOI ( bits): Domain of Interpretation.
- Protocol ID ( bits): Protocol involved.
- SPI Size ( bits): Size of SPI.
- Notify Message Type ( bits): Code indicating status or error type (See Table 18.8 for errors, 18.9 for status).
- SPI (variable length): Associated SPI.
- Notification Data (variable length): Optional extra info.
-
Delete Payload (Figure 18.42):
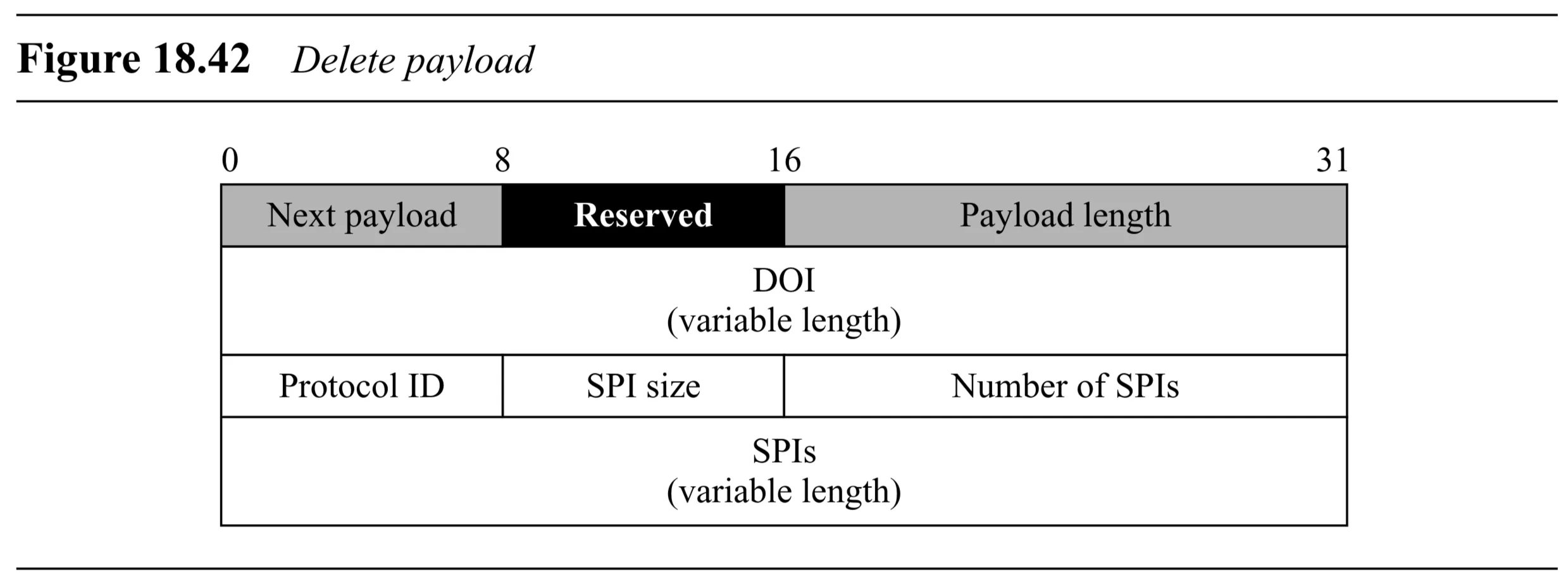
- Generic Header
- DOI ( bits): Domain of Interpretation.
- Protocol ID ( bits): Protocol of SAs being deleted.
- SPI Size ( bits): Size of SPIs.
- Number of SPIs ( bits): How many SPIs follow.
- SPIs (variable length): List of SPIs for the SAs that have been deleted.
-
Vendor ID Payload (Figure 18.43):
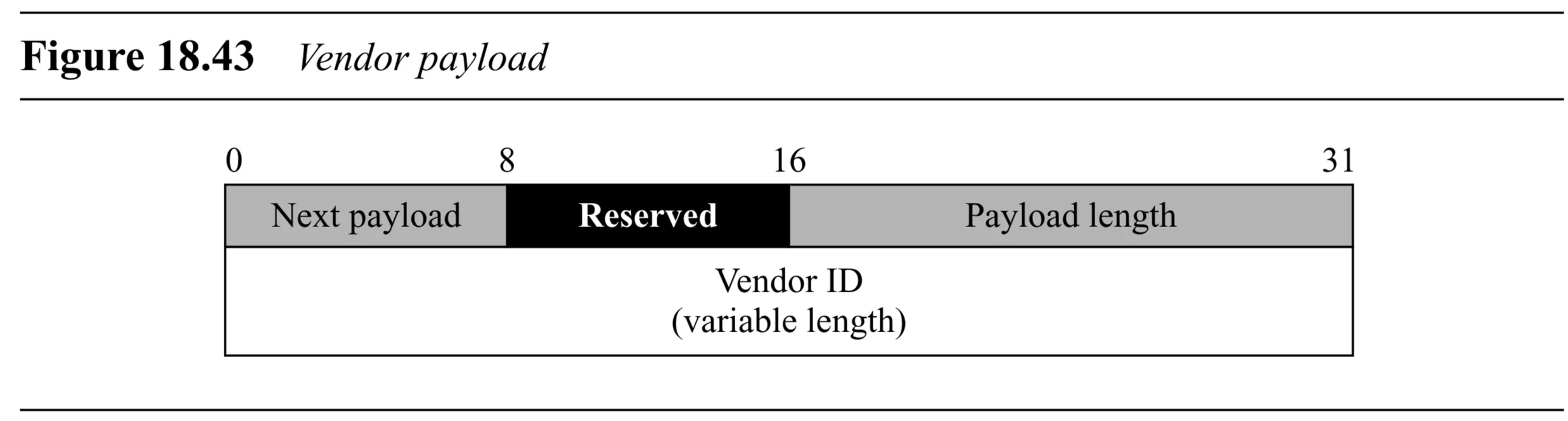
- Generic Header
- Vendor ID (variable length): Constant identifying the vendor.