Introduction to MACs
- A Message Authentication Code (MAC), also known as a cryptographic checksum or a keyed hash function, is a widely used cryptographic primitive.
- Functionality: MACs provide:
- Message Integrity: Ensuring a message has not been altered during transmission.
- Message Authentication: Verifying the origin of the message (authenticating the sender).
- Basis: MAC algorithms are typically based on either:
- Symmetric Block Ciphers (e.g., AES)
- Cryptographic Hash Functions (e.g., SHA-256)
MACs vs. Digital Signatures
| Feature | MACs | Digital Signatures |
|---|---|---|
| Key Type | Symmetric (shared secret key ) | Asymmetric (private key for signing, public key for verification) |
| Functionality | Integrity, Authentication | Integrity, Authentication, Non-repudiation |
| Non-repudiation | No - Cannot prove origin to a third party | Yes - Sender cannot deny sending the message |
| Speed | Generally much faster | Generally slower |
| Basis | Block ciphers or hash functions | Asymmetric algorithms (e.g., RSA, ECC) |
- Advantage of MACs: Speed, due to reliance on faster symmetric-key operations or hash functions.
12.1 Principles of Message Authentication Codes
- Core Idea: Similar to digital signatures, MACs append an authentication tag (the MAC value) to a message .
- Key Difference: MACs use a symmetric key , shared between the sender and receiver, for both generating and verifying the tag.
- Notation: The MAC tag generated for a message using key is denoted as:
MAC Process (Generation and Verification)
- Motivation: To allow communicating parties (e.g., Alice and Bob) who share a secret key to detect any manipulation of a message sent between them.
- Diagram Description (Fig. 12.1):
- Sender (e.g., Bob):
- Has the message and the shared secret key .
- Computes the MAC tag: .
- Sends the message and the tag pair to the receiver.
- Receiver (e.g., Alice):
- Receives the pair .
- Has the same shared secret key .
- Independently re-computes the MAC tag using the received message : .
- Verification: Compares the received tag with the re-computed tag . If , the message is considered authentic and integral. If , the message has been tampered with or did not originate from a party knowing .
- Sender (e.g., Bob):
Security Services Provided by MACs
- Message Integrity: The fundamental assumption is that if the message is altered in transit (maliciously or accidentally), the re-computed MAC will not match the original MAC . This detects the alteration.
- Message Authentication: Since only parties possessing the secret key can compute a valid MAC for a given message , the receiver (Alice) is assured that the message originated from the sender (Bob) who also possesses . An adversary (Oscar) without cannot create a valid pair for a modified or new message .
Properties of Message Authentication Codes
- Cryptographic Checksum: A MAC generates a secure, key-dependent checksum (the tag ) for a message .
- Symmetric: MACs rely on shared secret keys. Both the party generating the MAC and the party verifying it must possess the same key .
- Arbitrary Message Size: MAC algorithms can process input messages of any length.
- Fixed Output Length: The generated MAC tag has a fixed bit length, regardless of the input message size. This length depends on the specific MAC algorithm used.
- Message Integrity: As described above, MACs allow detection of message modifications.
- Message Authentication: As described above, MACs assure the receiver of the message’s origin (from someone holding the key ).
- No Non-repudiation: This is a crucial limitation. Because the key is shared, either party (Alice or Bob) could have generated a specific pair. Therefore, neither party can prove to a neutral third party (e.g., a judge) that the other party created the message and MAC. The judge cannot distinguish who generated it. MACs protect the two parties from outsiders, but not from each other in disputes.
12.2 MACs from Hash Functions: HMAC
- One common way to construct MACs is by using cryptographic hash functions (e.g., SHA-1, SHA-256) as the core building block.
- HMAC (Hash-based Message Authentication Code) is a very popular and widely used standard (e.g., in TLS, IPsec).
Basic (Insecure) Hash-Based Constructions
The most intuitive idea is to simply hash the key and the message together. The symbol denotes concatenation.
- Secret Prefix MAC:
- Secret Suffix MAC:
- Warning: While seemingly secure due to hash function properties (one-wayness, collision resistance), these simple constructions have security weaknesses.
Attacks Against Secret Prefix MACs (Length Extension Attack)
- Assumption: This attack applies when the underlying hash function uses an iterative structure like Merkle-Damgård (common in MD5, SHA-1, SHA-2). The message is processed in blocks: .
- Process: Bob computes . The value is the final hash output.
- The Attack: An adversary Oscar, who intercepts , can compute a valid MAC for a new message (where is an arbitrary block chosen by Oscar) without knowing the secret key .
- How it works: The output of represents the internal state of the hash function after processing and . Oscar can use as the initial state (IV) for hashing additional data (, along with necessary padding derived from the original message length). The result will be the correct MAC for the extended message .
- Diagram Explanation (Implied by Attack Description & Figure on p.323):
- Oscar intercepts where .
- Oscar chooses an extension block .
- Oscar computes the necessary padding for the original message based on its length (this might be implicitly handled by the hash continuation).
- Oscar computes (conceptually, continuing the hash from state ).
- Oscar sends the forged message and the forged MAC to Alice.
- Alice, upon receiving , computes . Due to the iterative nature, this computation yields , so Alice accepts the forged message.
- Consequence: This is serious. For example, Oscar could append unfavorable clauses to an electronic contract and compute a valid MAC for the modified contract .
Attacks Against Secret Suffix MACs
- Construction:
- Weakness: The security of this construction can be limited by the collision resistance of the underlying hash function , independent of the key .
- The Attack (Birthday Attack based):
- If an attacker Oscar can find a collision for the hash function itself (i.e., find two different messages and such that ), this may compromise the MAC. (Note: The text’s claim that is also valid for just because is not generally true for the suffix method, but the underlying security concern is valid).
- More accurate concern: The security level might be lower than expected based on the key length . Finding a collision for a hash function with an -bit output using a birthday attack takes approximately operations.
- If is less than (the complexity of brute-forcing the key), then an attacker might target the hash function’s collision resistance rather than the key.
- Example: Using SHA-1 ( bits) with a -bit key ().
- Brute-force key search takes operations.
- Finding a SHA-1 collision takes roughly operations (and possibly fewer due to known weaknesses).
- In this case, the effective security is limited by the complexity of the collision attack on the hash function, not the strength suggested by the key length.
HMAC Construction
- Proposed by Bellare, Canetti, and Krawczyk (1996) to overcome the weaknesses of the simpler prefix/suffix constructions.
- Structure: Uses two nested hash computations (inner and outer). Let be the hash function, be the secret key, and be the message. Let be the input block size of the hash function in bits, and be the output size in bits.
HMAC Steps & Diagram Description (Fig 12.2)
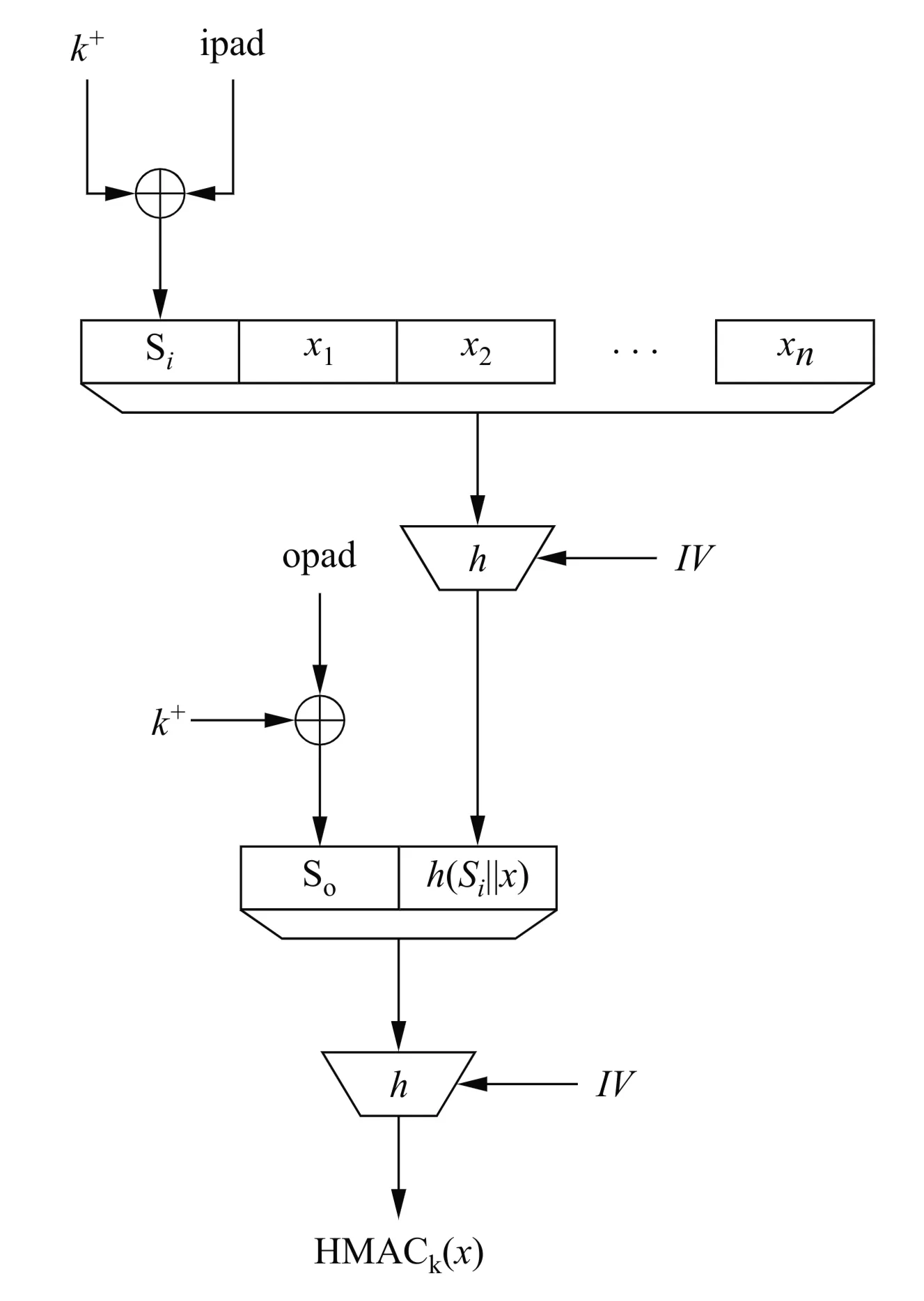
- Key Preparation:
- If the key is longer than the block size , hash the key first: .
- If the key (or hashed ) is shorter than bits, pad it with zeros on the left to create a -bit block .
- If is exactly bits, .
- Define Pads: Two constant -bit strings are used:
ipad(inner pad): Byte0x36repeated times. (Binary:00110110...)opad(outer pad): Byte0x5Crepeated times. (Binary:01011100...)
- Inner Hash:
- Compute the -bit block .
- Concatenate with the message : .
- Compute the hash: . (The hash function’s IV is used here).
- Outer Hash:
- Compute the -bit block .
- Concatenate with the result of the inner hash: .
- Compute the hash: . (The hash function’s IV is used again here).
- Result: The HMAC is the output of the outer hash:
HMAC Formula
The entire construction can be expressed as:
- Note on Sizes: Often, the hash output length is smaller than the block size (e.g., SHA-1: , ). The inner hash result (length ) needs to be processed by the outer hash, which expects -bit blocks. Hash functions inherently handle this through their padding and preprocessing steps defined in their standards (e.g., Section 11.4.1 for SHA-1 preprocessing).
HMAC Efficiency
- The potentially long message is hashed only once (in the inner hash).
- The outer hash operates on only two blocks: the derived outer key and the inner hash result .
- The computational overhead compared to simply hashing the message is minimal (one extra hash computation on short, fixed-size blocks).
HMAC Security
- HMAC has a proof of security.
- Its security is formally related to the security properties of the underlying hash function .
- Result: If the hash function meets certain requirements (primarily pseudorandomness when keyed via the HMAC structure, related to collision resistance and preimage resistance), then HMAC is a secure MAC.
- Specifically, it can be shown that an attacker able to break HMAC (e.g., forge a MAC without the key, distinguish HMAC output from random) could also be used to break the underlying hash function (e.g., find collisions, compute hash output without knowing the initial state/IV).
12.3 MACs from Block Ciphers: CBC-MAC
- An alternative to hash-based MACs is to use symmetric block ciphers (like AES).
- The most common method is based on the Cipher Block Chaining (CBC) mode of operation, hence CBC-MAC.
MAC Generation (CBC-MAC)
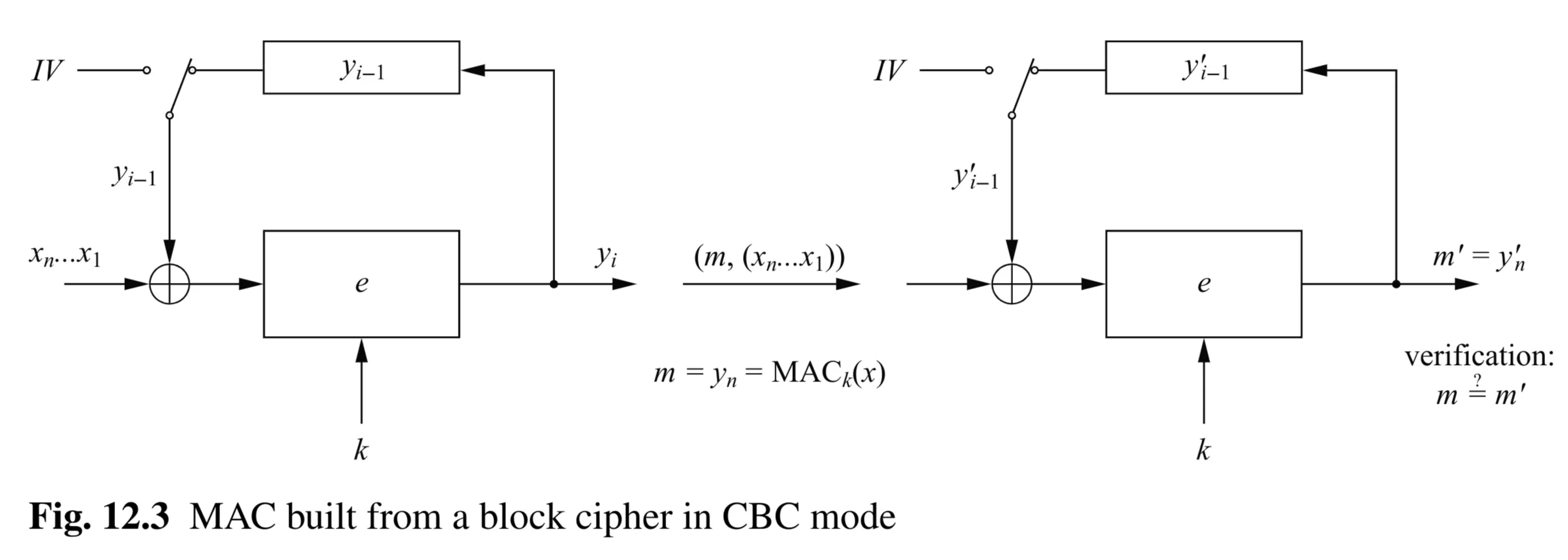
- Setup: Requires a block cipher encryption function , a secret key , and an Initial Value . The message is divided into blocks matching the block cipher’s block size.
- Process (Diagram Fig 12.3 - Left/Sender):
- First Block: Compute .
- Subsequent Blocks ( to ): Compute . (The output of the previous encryption block is XORed with the current message block before encrypting).
- Final MAC: The MAC tag is the entire output of the last encryption: .
- Important Notes:
- The can be public, but should ideally be unpredictable (random or nonce) for certain security proofs, though a fixed IV (e.g., IV=0) is common in basic CBC-MAC standards (with security implications if not handled carefully, especially regarding message prefixes).
- The intermediate values are internal state and are not transmitted or revealed. Only the final is the MAC.
MAC Verification (CBC-MAC)
- Process (Diagram Fig 12.3 - Right/Receiver):
- The receiver gets the message and the MAC tag .
- Using the same shared secret key , the same , and the received message blocks , the receiver performs the exact same CBC-MAC computation as the sender:
- for .
- This yields a computed tag .
- Verification: Compare the computed tag with the received tag .
- If , the MAC is valid; accept the message.
- If , the MAC is invalid; reject the message (it was altered or forged).