Working Procedure
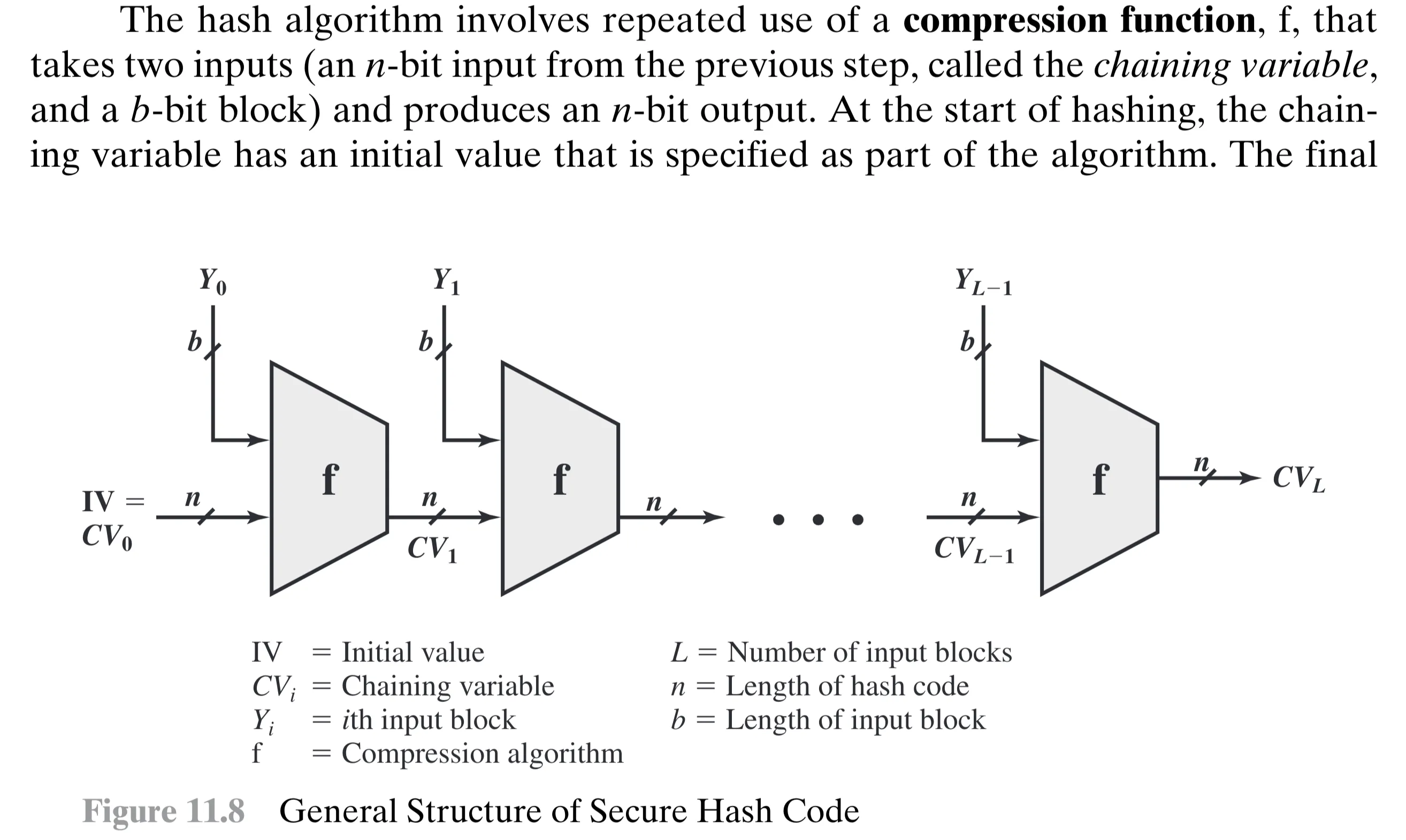 [[W.Stallings - Cryptography and Network Security 6th ed.pdf#page=350&rect=121,72,497,296|]]
[[W.Stallings - Cryptography and Network Security 6th ed.pdf#page=350&rect=121,72,497,296|]]
Motivation: Signing Long Messages
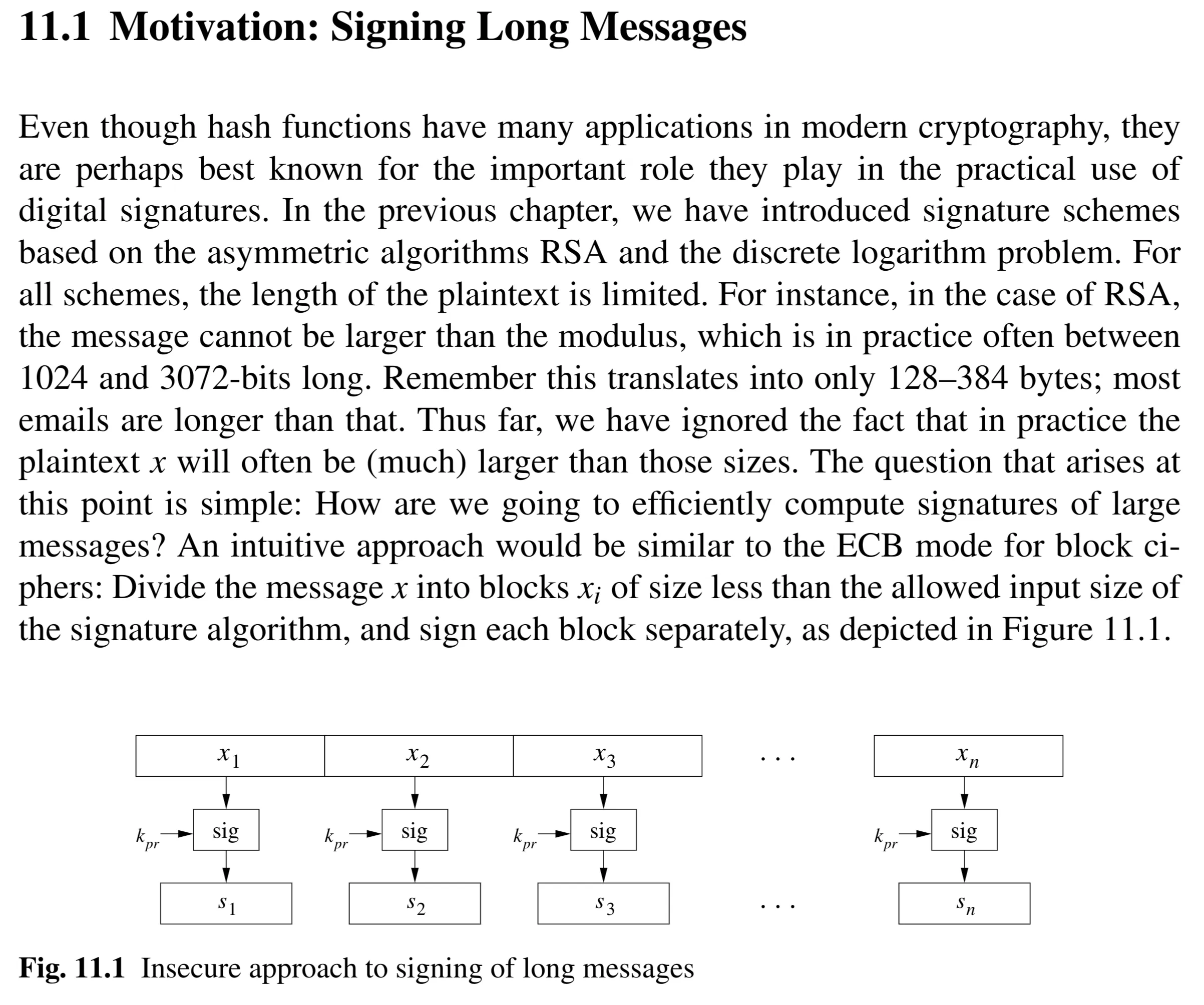 [[2.understanding-cryptography-by-christof-paar-.pdf#page=306&rect=49,325,393,612|]]
[[2.understanding-cryptography-by-christof-paar-.pdf#page=306&rect=49,325,393,612|]]
Problem 1
 [[2.understanding-cryptography-by-christof-paar-.pdf#page=306&rect=50,203,392,294|]]
[[2.understanding-cryptography-by-christof-paar-.pdf#page=306&rect=50,203,392,294|]]
Problem 2
 [[2.understanding-cryptography-by-christof-paar-.pdf#page=306&rect=49,152,391,204|]]
[[2.understanding-cryptography-by-christof-paar-.pdf#page=306&rect=49,152,391,204|]]
Problem 3
 [[2.understanding-cryptography-by-christof-paar-.pdf#page=306&rect=51,72,391,151|]]
[[2.understanding-cryptography-by-christof-paar-.pdf#page=306&rect=51,72,391,151|]]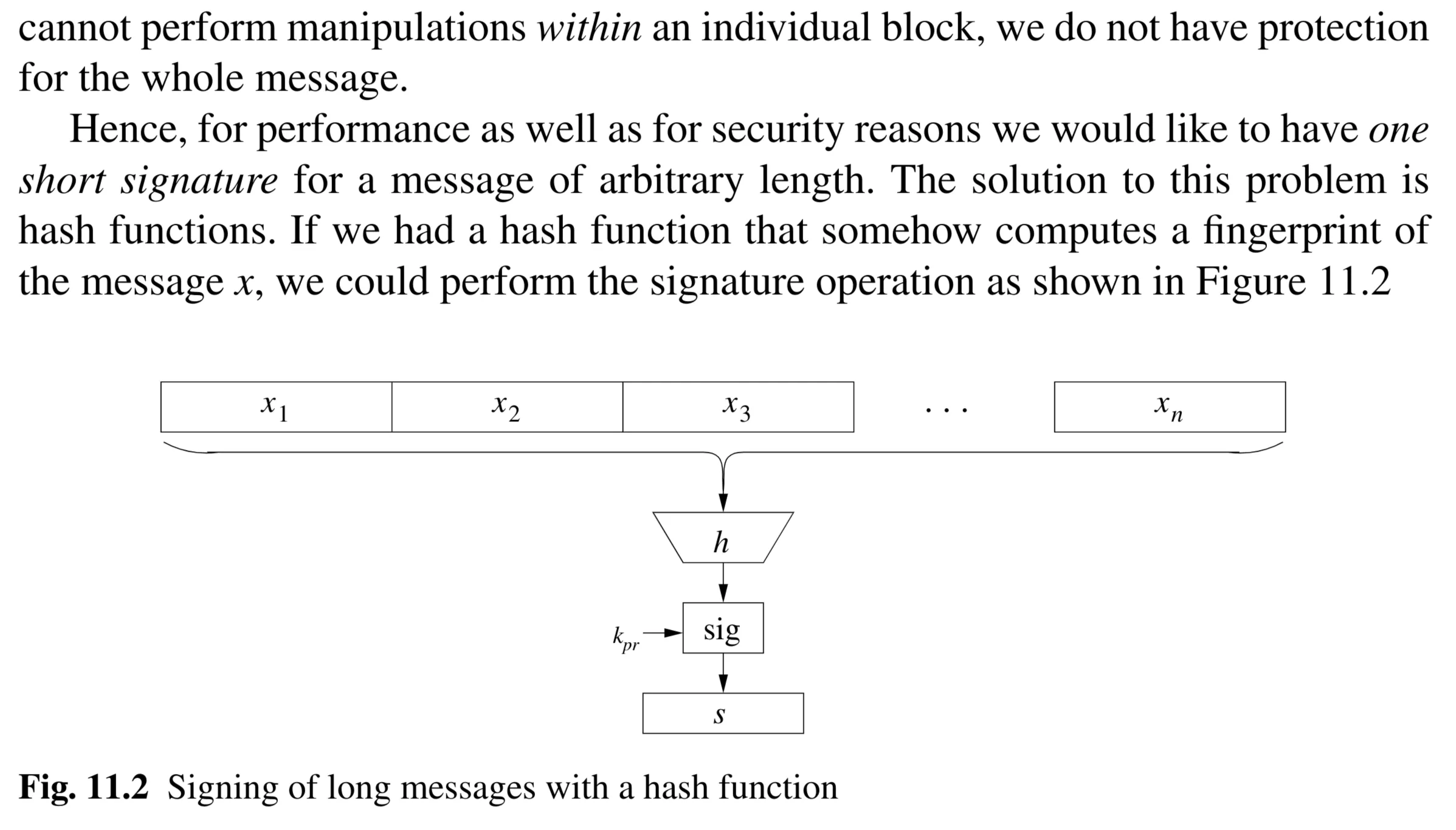 [[2.understanding-cryptography-by-christof-paar-.pdf#page=307&rect=50,415,392,610|]]
[[2.understanding-cryptography-by-christof-paar-.pdf#page=307&rect=50,415,392,610|]]
Security Requirements of Hash Functions

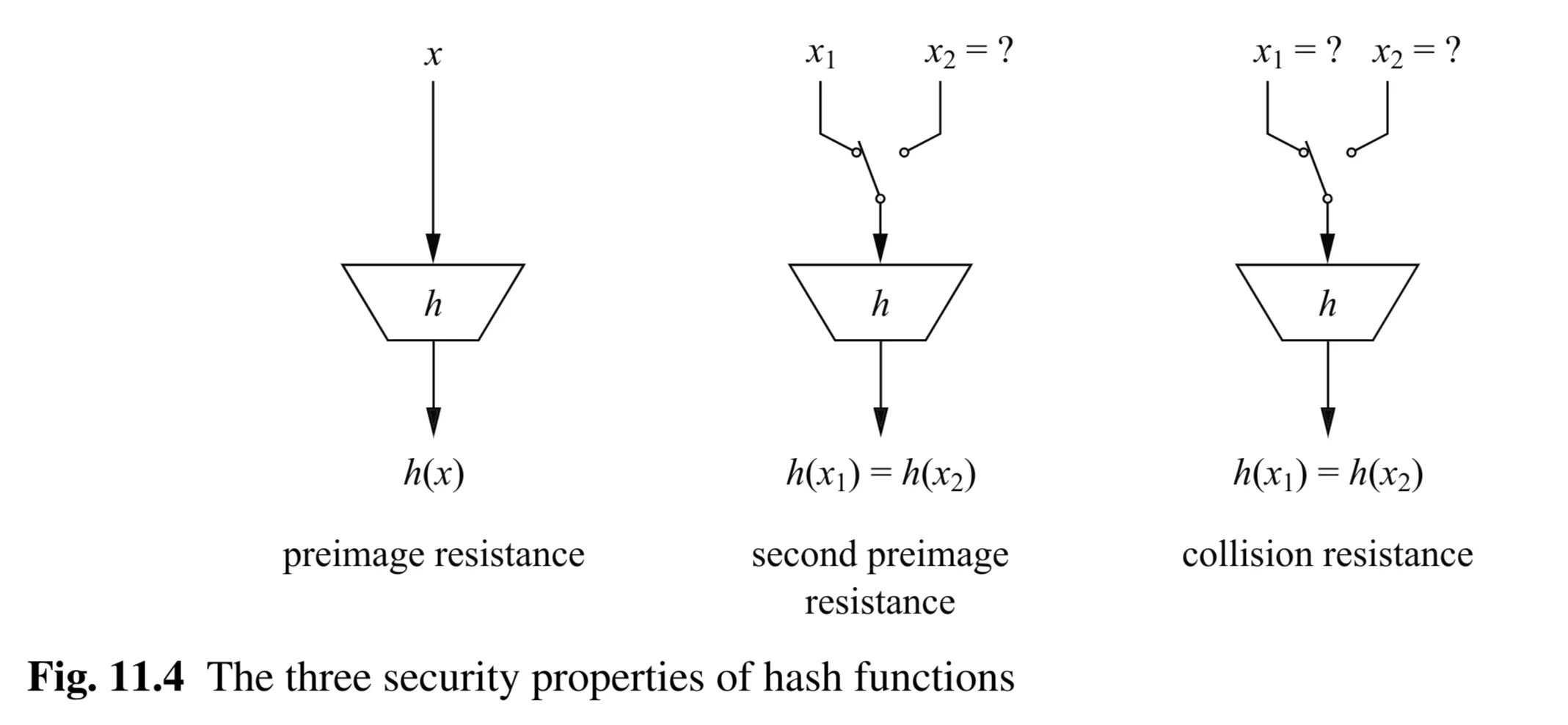
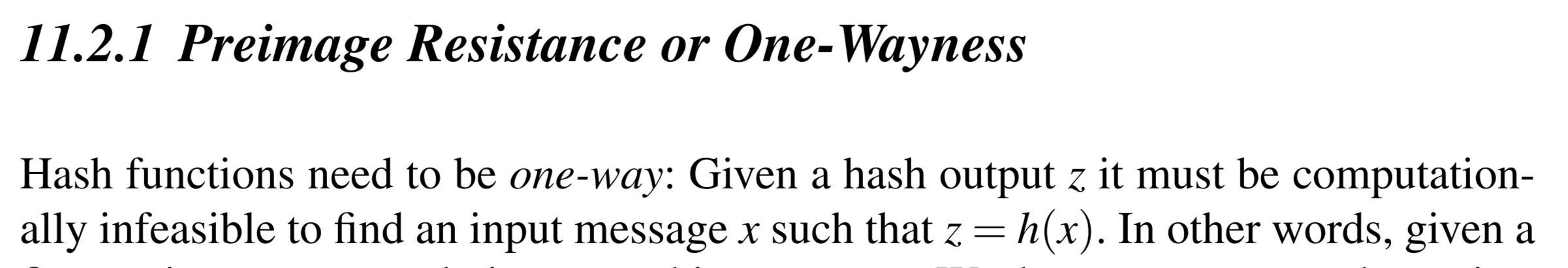


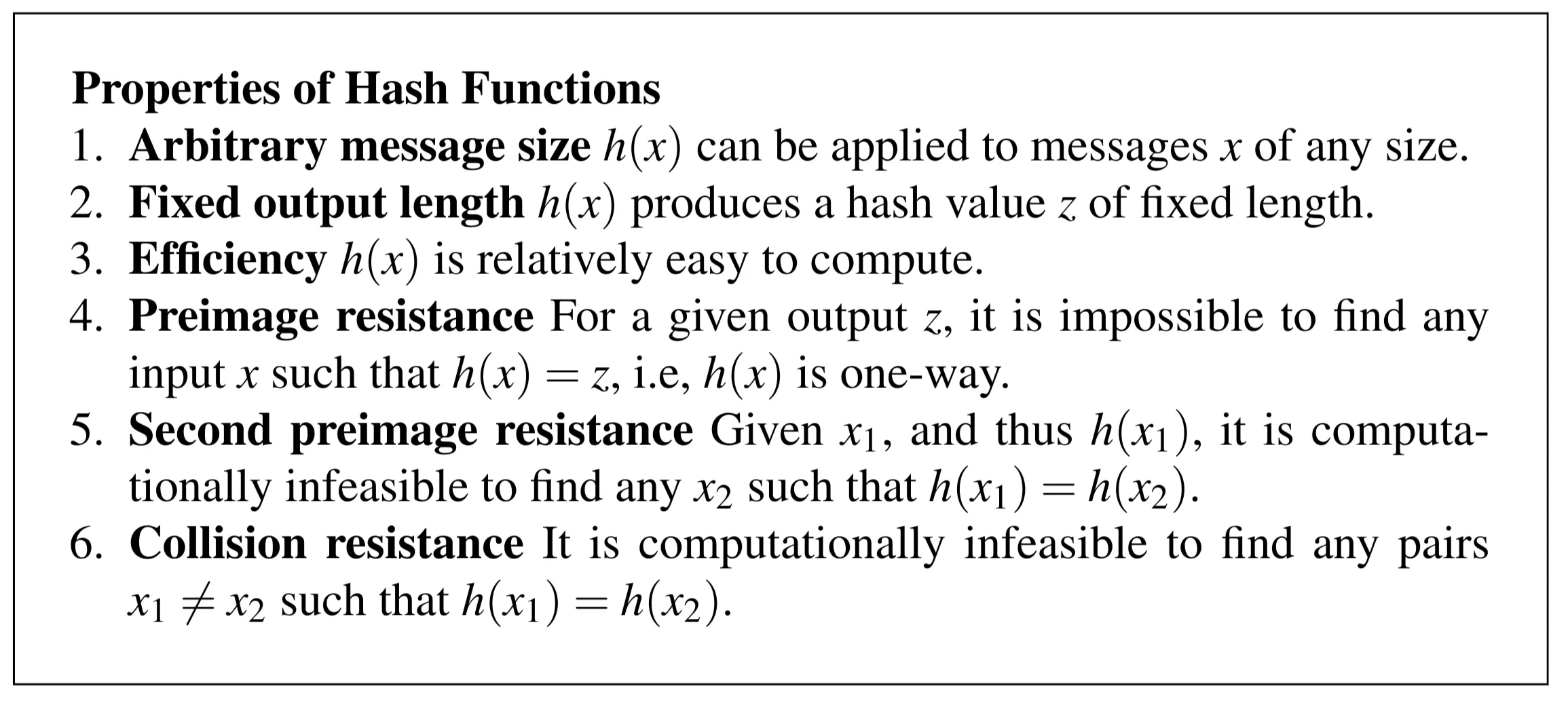
Properties of Hash Functions
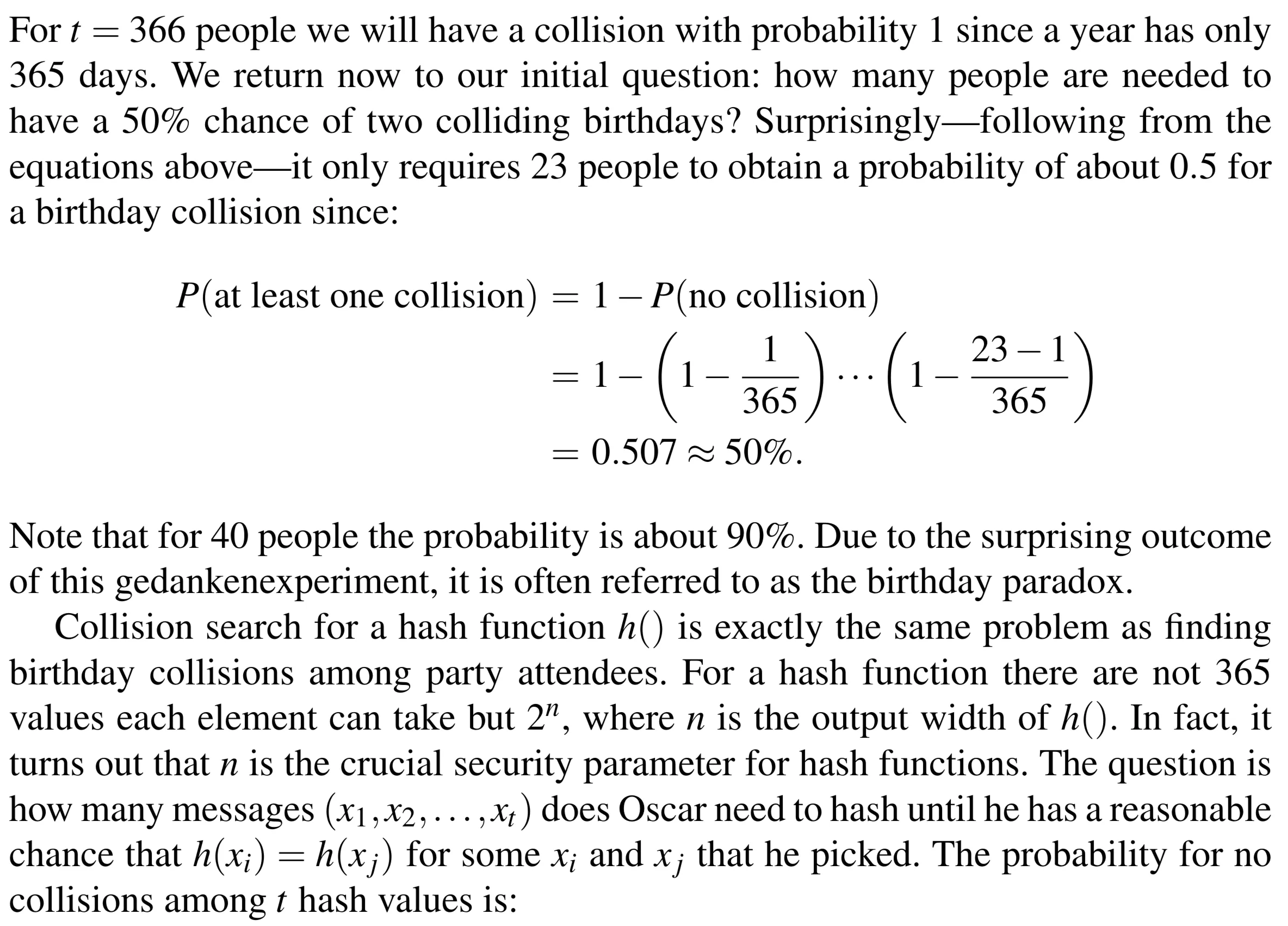
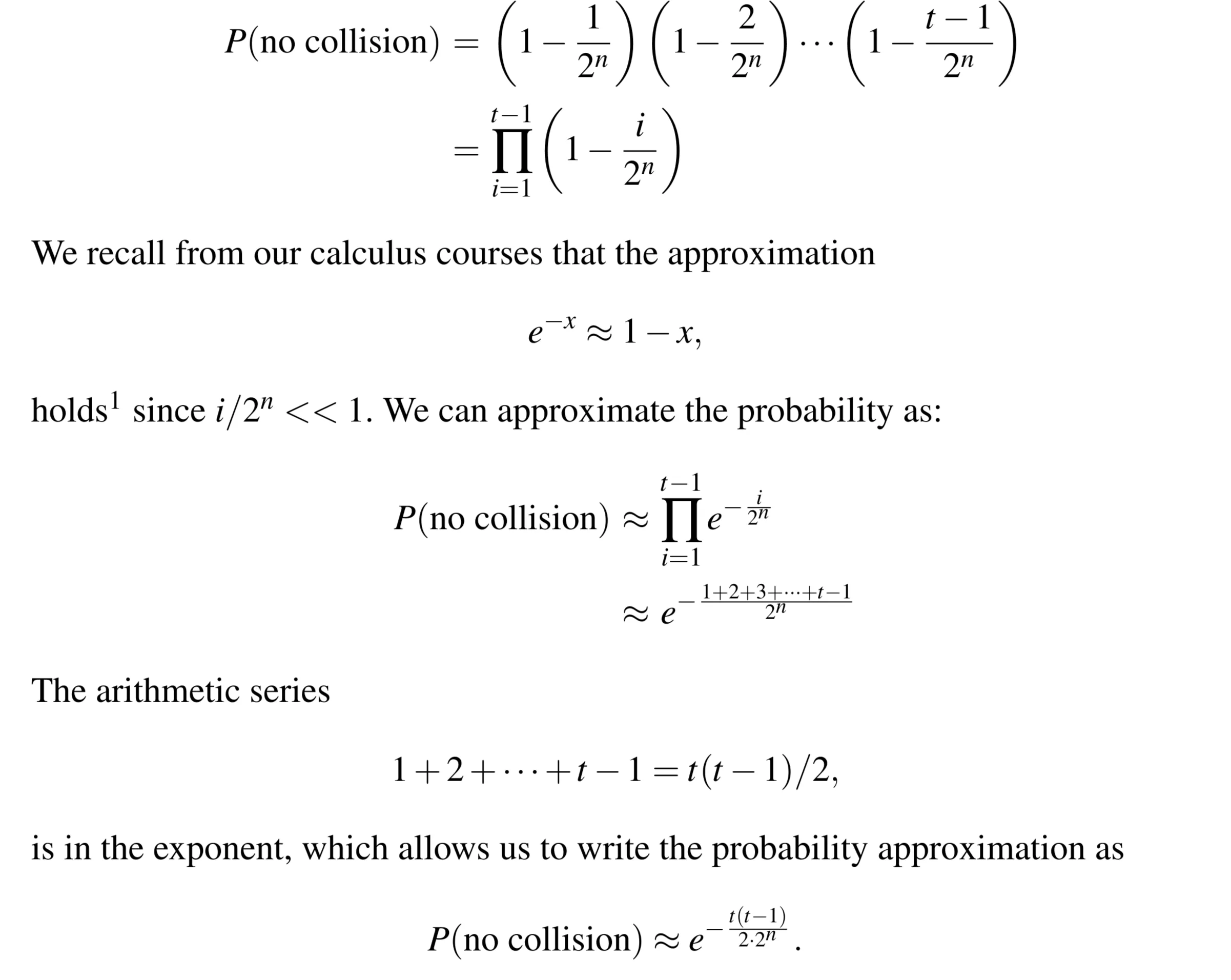
Birthday Attack




Block Ciphers as Hash Functions
[[W.Stallings - Cryptography and Network Security 6th ed.pdf#page=351&rect=126,534,492,637|]]
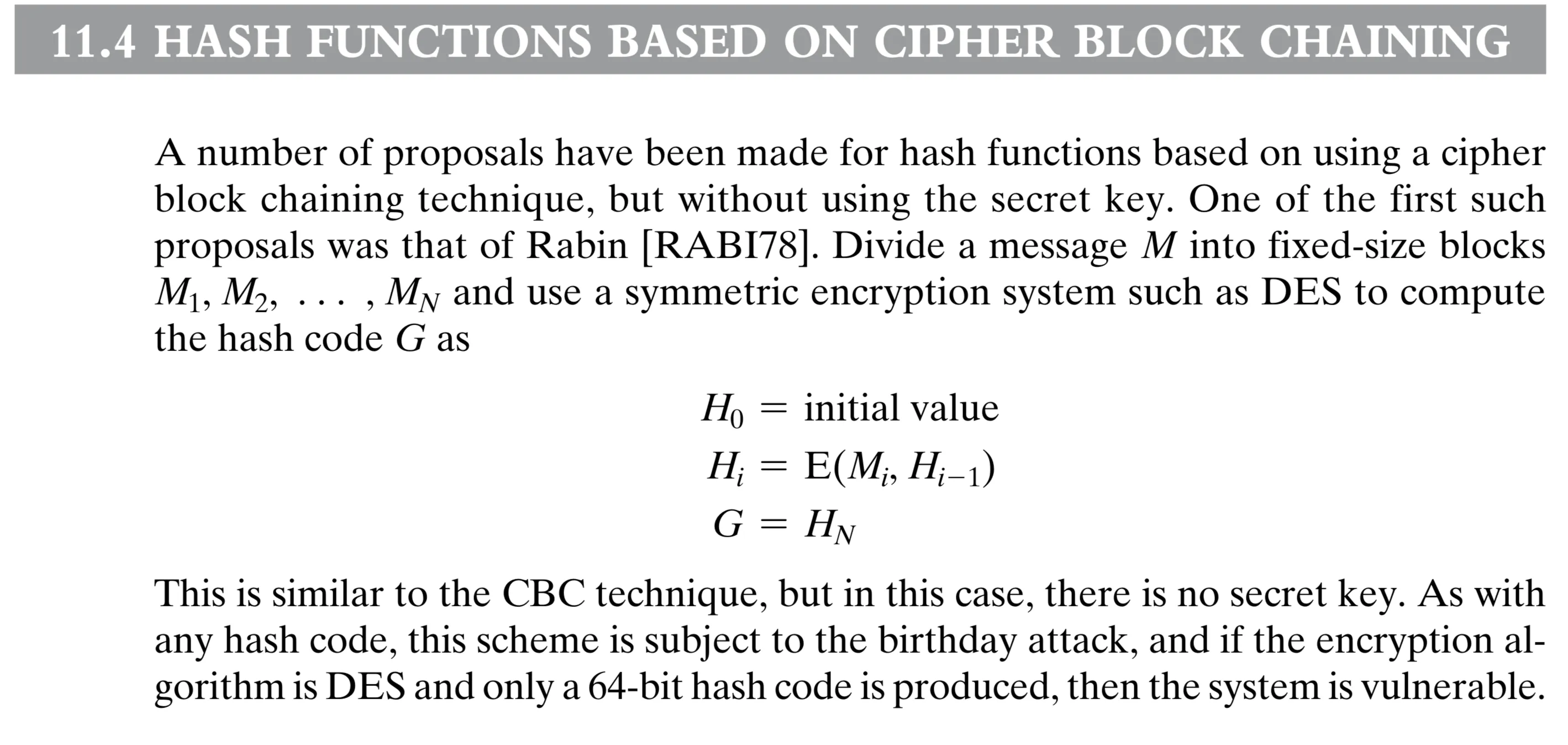 [[W.Stallings - Cryptography and Network Security 6th ed.pdf#page=351&rect=89,101,495,294|]]
[[W.Stallings - Cryptography and Network Security 6th ed.pdf#page=351&rect=89,101,495,294|]]