Level 1: The “Why” and “What” of Key Establishment
What’s the Big Deal with Keys?
You’ve learned about powerful cryptographic tools:
- Confidentiality: Keeping secrets using encryption (symmetric or asymmetric).
- Integrity: Ensuring data isn’t tampered with (using MACs or digital signatures).
- Authentication: Verifying who sent a message (using MACs or digital signatures).
- Non-repudiation: Proving someone sent a message and can’t deny it (using digital signatures).
The Catch: ALL these tools rely on keys.
- Symmetric methods (AES, MACs) need Alice and Bob to share the exact same secret key.
- Asymmetric methods (RSA, signatures) need Alice to know Bob’s authentic public key and vice-versa.
Getting these keys to the right people securely before you can even start encrypting or signing is a fundamental challenge. This process is called Key Establishment.
Two Main Flavors of Key Establishment
Think about how Alice and Bob could end up with a shared secret key: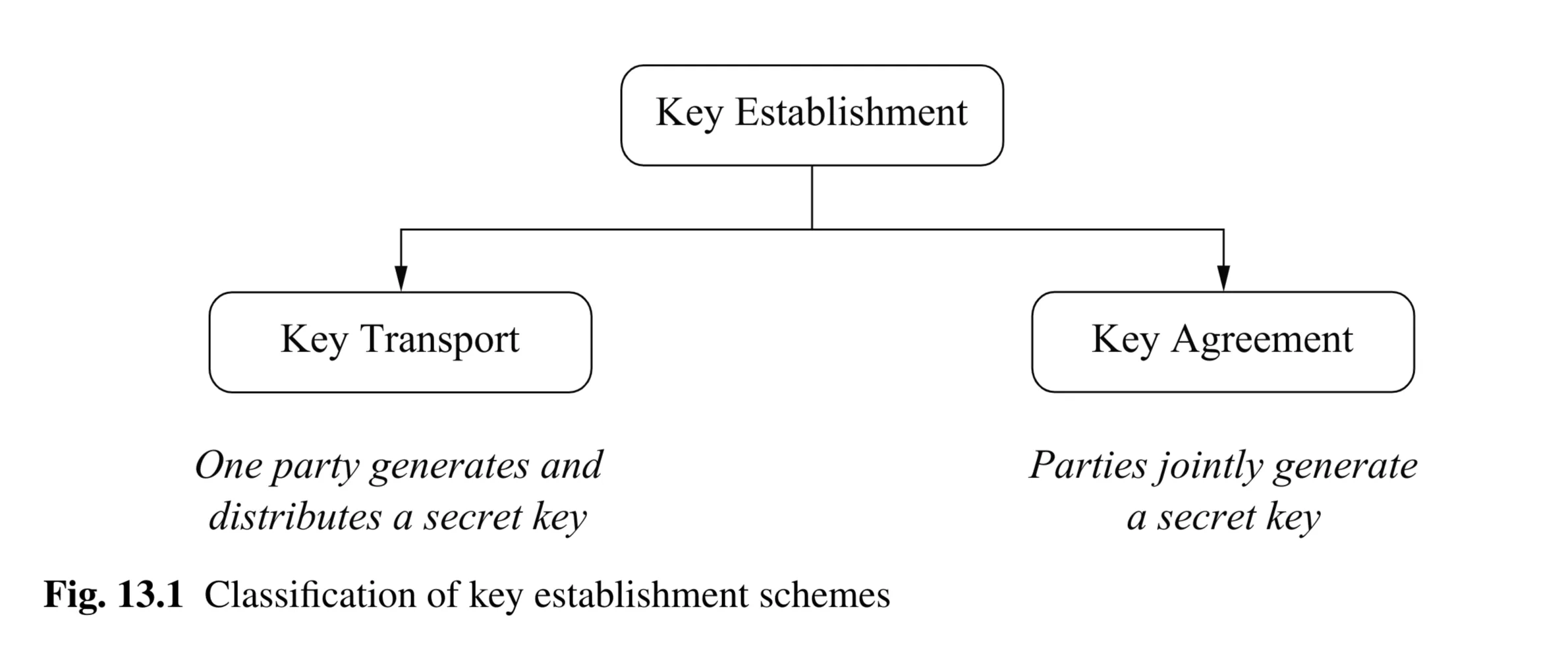
- Key Transport: Alice creates a secret key, then securely sends it to Bob. Alice is in control of the key value initially.
- Key Agreement: Alice and Bob work together, exchanging some information publicly, and both derive the same shared secret key independently. Ideally, neither party alone controls the final key value. (Diffie-Hellman is the classic example you might have seen).
The Headache of Scaling Up: The Problem
Imagine a small group of 4 people (Alice, Bob, Chris, Dana) who all want to talk securely with each other using symmetric keys.
- Alice needs a key for Bob (), for Chris (), and for Dana (). That’s 3 keys for Alice.
- Bob needs keys for Alice (), Chris (), and Dana ().
- …and so on.
The Problem:
- Each person needs to store keys (where is the number of people).
- The total number of unique key pairs in the network is . This grows quadratically (roughly ).
- For 4 users: unique keys ().
- For 750 users (Example 13.1): unique keys!
- Worse: If a new person (Noah) joins, you need to establish a new secure key between Noah and every single existing person. This requires new secure key distributions.
Manually distributing keys (e.g., on a USB stick, over the phone - “out-of-band”) works for very small, static groups but breaks down quickly. We need better methods.
Key Takeaway Level 1: Key establishment is crucial but non-trivial. Simple manual distribution doesn’t scale. We need automated, secure ways to transport or agree on keys.
Level 2: Using a Helper - The Key Distribution Center (KDC)
Solving the Problem with a Trusted Friend
Instead of everyone managing keys with everyone else, what if we introduce a trusted central server? Let’s call it the Key Distribution Center (KDC).
The Setup:
- Every user (Alice, Bob, …) trusts the KDC completely.
- When a user joins the network initially, they establish one secret key just between them and the KDC. This is called a Key Encryption Key (KEK).
- Alice has (shared only with KDC).
- Bob has (shared only with KDC).
- The KDC stores all these KEKs ().
- This initial KEK distribution still needs a secure channel (like manual setup), but it’s only one key per user joining, not .
Basic KDC Protocol (Key Transport)
Now, how does Alice get a key to talk to Bob?
- Request: Alice tells the KDC, “I () want to talk to Bob ().” (
RQST(IDA, IDB)) - KDC Action:
- The KDC generates a brand new, random key for this specific conversation. This is called a session key (). Session keys are temporary (more on this later).
- The KDC encrypts this session key twice:
- Once using Alice’s KEK:
- Once using Bob’s KEK:
- Distribution: The KDC sends to Alice and to Bob. (Or sends both to Alice, who forwards to Bob).
- Decryption:
- Alice uses her KEK to decrypt and get .
- Bob uses his KEK to decrypt and get .
- Success! Alice and Bob now share and can communicate securely using it.
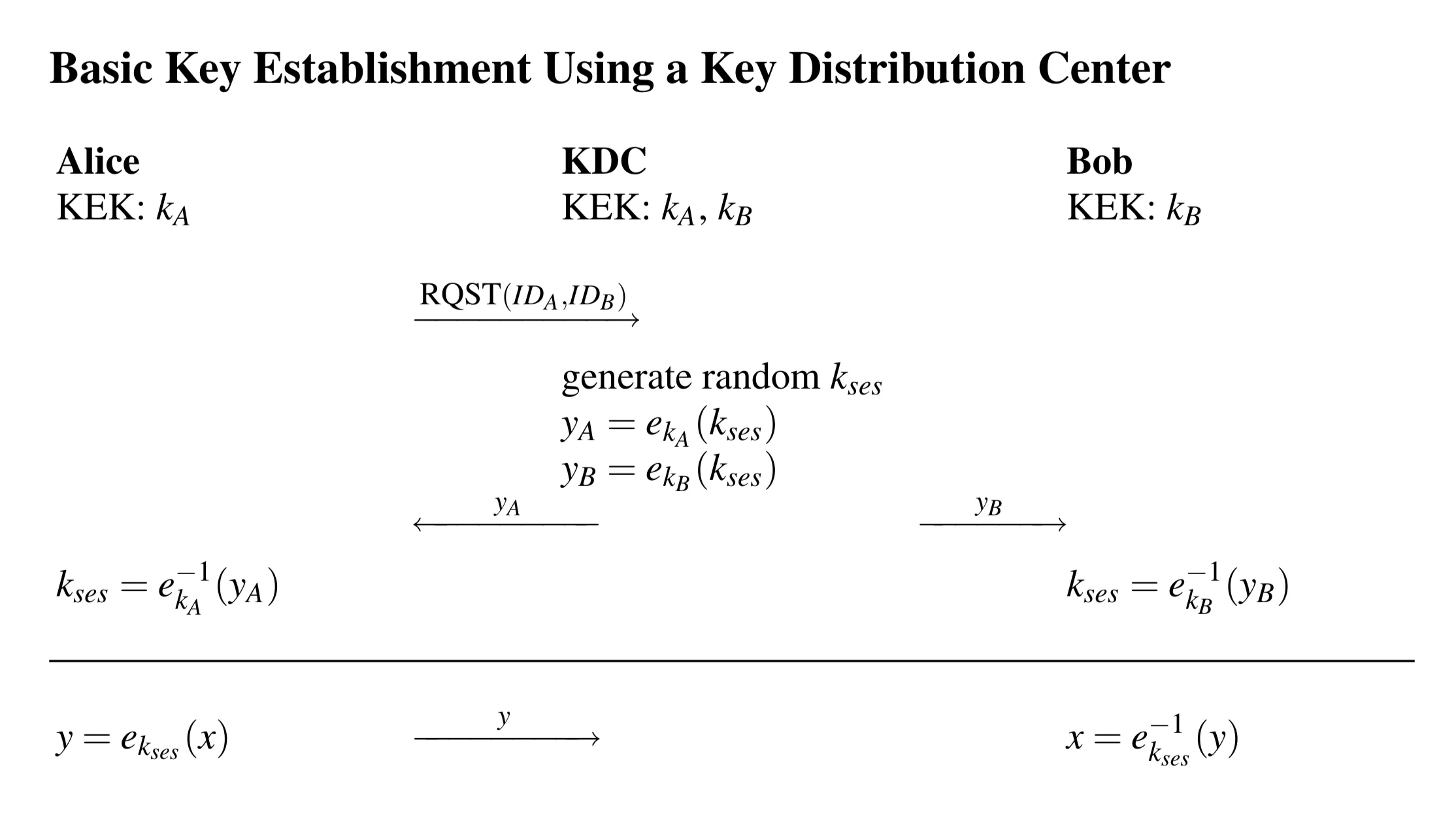
Key Advantage: Only long-term KEKs are needed. Adding a user requires only establishing one new KEK with the KDC. Much better than .
Key Freshness and Key Derivation
Why use temporary session keys?
- Damage Limitation: If a session key is somehow compromised (e.g., attacker guesses it later), only the communication protected by that specific key is revealed. Past and future sessions (using different session keys) remain secure.
- Attack Difficulty: An attacker has less ciphertext encrypted with any single key, making cryptanalysis harder.
How to get fresh keys without contacting the KDC every single time? If Alice and Bob already share a key (maybe it’s a KEK, or a previously established session key they want to update), they can derive a new session key () from it.
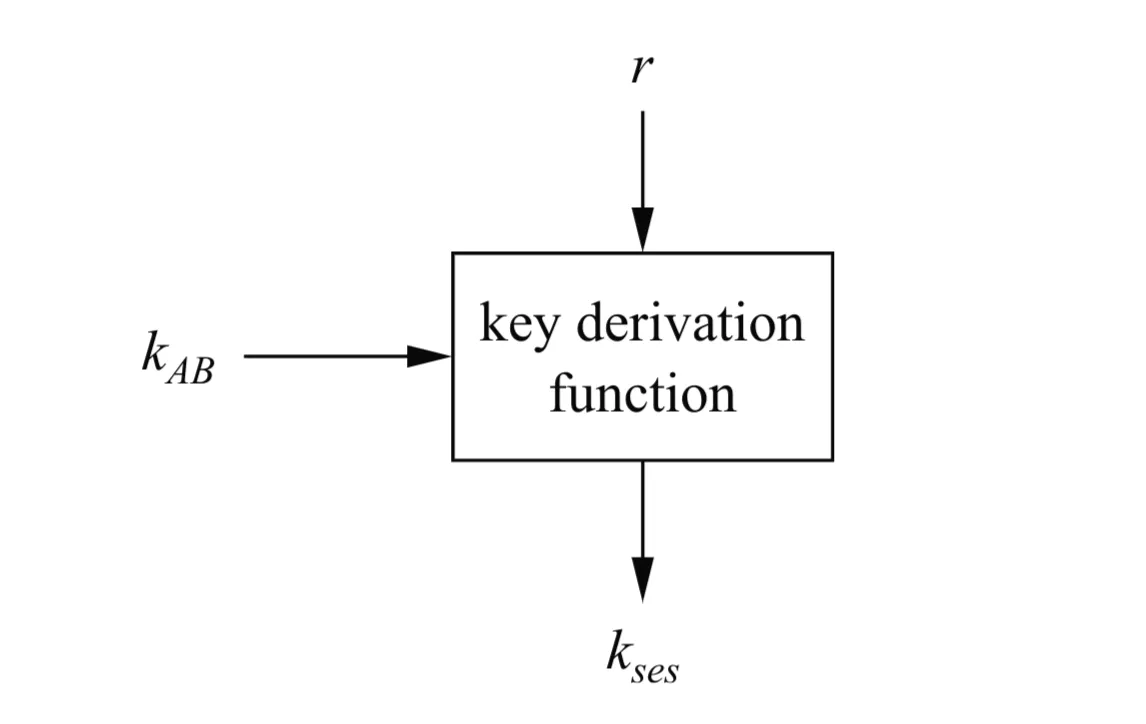 Shows a box labeled “key derivation function” (KDF).
Shows a box labeled “key derivation function” (KDF).
- Inputs: The existing shared secret and some non-secret changing value .
- Output: The new session key .
Methods:
- Nonce-based: One party (say Bob) generates a random number, used only once (a nonce), . He sends to Alice. Both compute . A common KDF is encryption: or using a MAC: .
- Counter-based: If Alice and Bob can keep synchronized counters (), they can both compute periodically, incrementing the counter each time. or . This avoids sending the nonce .
Important KDF Property: The KDF must be a one-way function. Knowing and (or ) should NOT allow an attacker to figure out the original . This protects the master key even if session keys leak.
Key Takeaway Level 2: KDCs centralize trust and key management, solving the problem for symmetric keys. They use long-term KEKs to securely transport short-term session keys. Session keys provide freshness and limit damage. Key derivation functions can generate new keys from existing ones.
Level 3: Making KDCs Robust - Kerberos and Security Concerns
Problems with the Basic KDC Protocol
The simple KDC protocol (Level 2) is conceptually nice, but vulnerable to active attackers (who can intercept, modify, and inject messages).
-
Replay Attack: Suppose Oscar eavesdropped on a past session and recorded and (containing an old session key, ) that Alice and Bob used. If later becomes compromised (e.g., Alice’s computer gets hacked), Oscar can simply resend the old to Alice and to Bob. They will decrypt them, recover , and think they have established a fresh session. Oscar, knowing , can now decrypt their “new” communication or even impersonate Alice or Bob. The basic protocol lacks timeliness or freshness checks.
-
Key Confirmation Attack (Impersonation): Alice wants to talk to Bob. She sends
RQST(IDA, IDB)to the KDC. Malicious user Oscar intercepts this. He sendsRQST(IDA, IDO)(claiming Alice wants to talk to him) to the KDC. The KDC, doing its job, generates a and sends back and . Oscar intercepts these. He forwards to Alice. Alice decrypts it and gets . Oscar also decrypts with his key and gets the same . Now, Alice thinks the key she received is for talking to Bob (because that’s who she asked for), but the KDC actually generated it for a session between Alice and Oscar. When Alice sends a message encrypted with , supposedly to Bob, Oscar can intercept and decrypt it because he also has . Alice has no way to confirm that the key she received is actually associated with Bob.
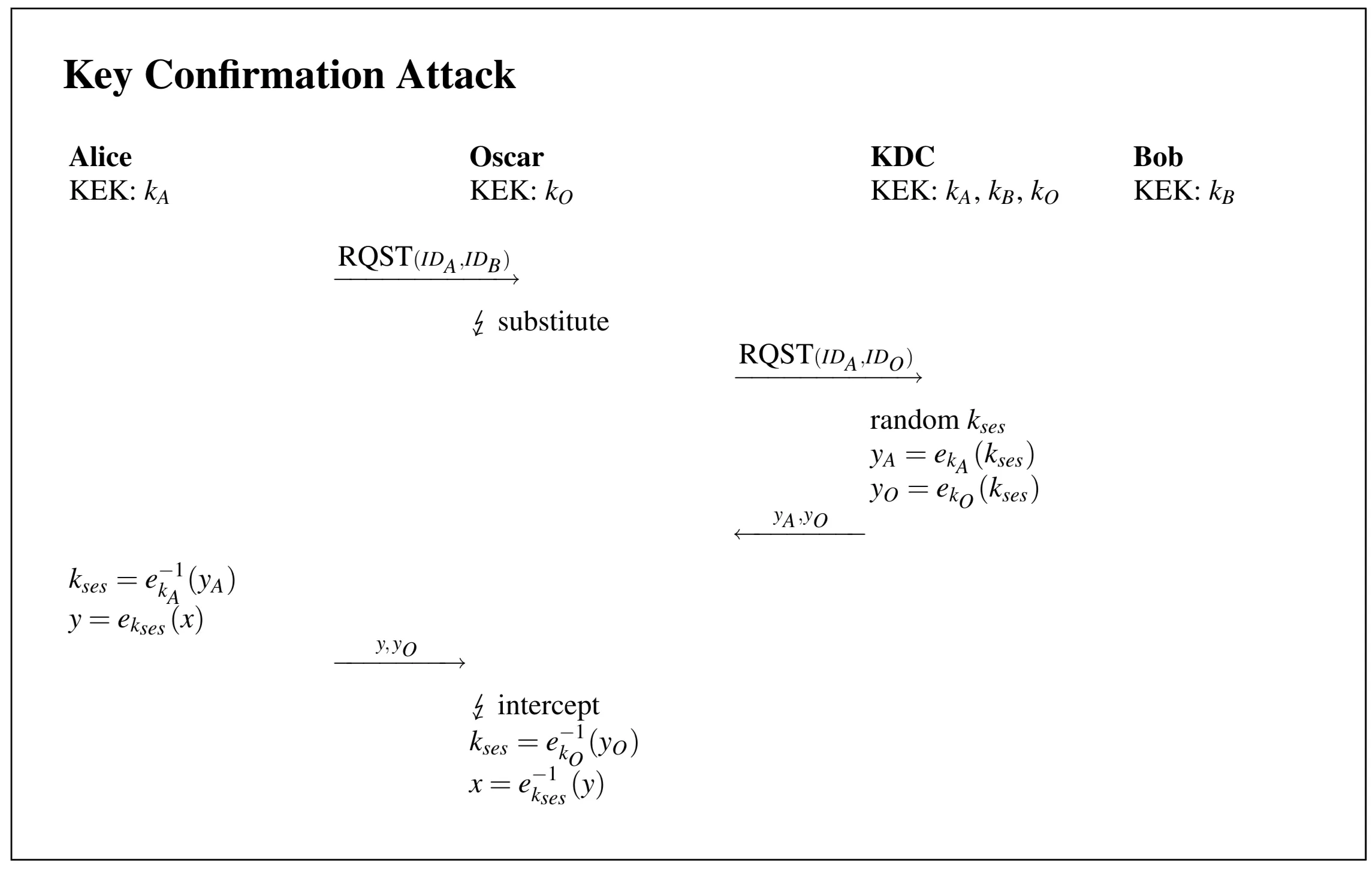 This illustrates the Key Confirmation Attack:
This illustrates the Key Confirmation Attack:
- Alice sends
RQST(IDA, IDB). - Oscar intercepts, substitutes
RQST(IDA, IDO)and sends to KDC. - KDC generates , creates and . Sends back (intended for Alice and Oscar).
- Oscar intercepts . He forwards only to Alice.
- Alice decrypts gets . She thinks this is for Bob.
- Oscar decrypts gets .
- Alice encrypts message as (intending to send to Bob).
- Oscar intercepts and decrypts it using .
Kerberos: A More Secure KDC Protocol
Kerberos is a widely used authentication and key distribution protocol (used in Windows networks, for example) that addresses these flaws. Here’s a simplified view:
Key Ideas:
- Timeliness: Uses timestamps and lifetimes to prevent replays.
- Authentication & Confirmation: Includes identities and nonces within encrypted messages to ensure parties know who they are talking to and that messages are fresh.
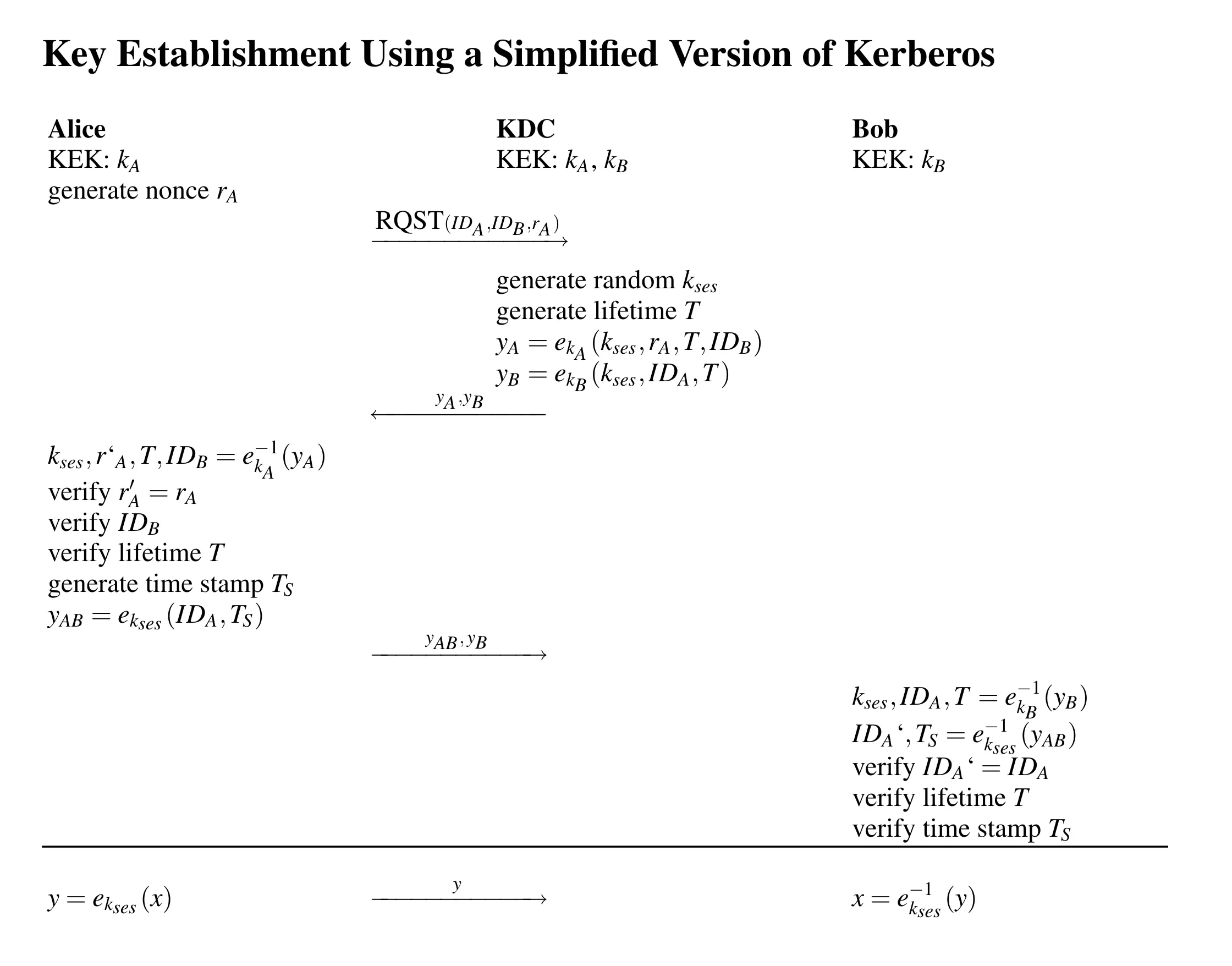
- Alice → KDC: Alice sends her ID (), Bob’s ID (), and a nonce (a random number she just generated).
RQST(IDA, IDB, rA) - KDC → Alice: KDC generates and a lifetime (how long is valid). It sends back two pieces:
- Session Info for Alice: . Encrypted with Alice’s KEK. Contains the session key, her original nonce , the lifetime , and Bob’s ID.
- Ticket for Bob (TGT): . Encrypted with Bob’s KEK. Contains the session key, Alice’s ID, and the lifetime . (This is like a sealed envelope only Bob can open).
- Alice’s Actions:
- Decrypts using .
- Checks : Does the nonce match the one she sent? If yes, she knows this message is a fresh reply from the KDC (not a replay) because only she and the KDC knew . This authenticates the KDC to Alice.
- Checks : Is this the ID of the person she wanted to talk to? If yes, she knows the KDC generated the key for the right session.
- Stores and .
- Creates an Authenticator: . Encrypts her ID and the current timestamp using the new session key .
- Alice → Bob: Alice sends Bob the Ticket () and the Authenticator ().
- Bob’s Actions:
- Decrypts the Ticket using his KEK . Gets , , and .
- Decrypts the Authenticator using the he just extracted. Gets and .
- Checks : Does from the authenticator match from the ticket? Confirms the authenticator is linked to this ticket.
- Checks Timestamp : Is recent (e.g., within 5 minutes of Bob’s clock)? Prevents replay of the authenticator. Requires loosely synchronized clocks.
- Checks Lifetime : Is the ticket still valid according to its lifetime?
- If all checks pass, Bob trusts that the key is fresh, valid, and shared with the user identified as . He now has the session key.
Kerberos Solves the Problems:
- Replay: Prevented by Alice checking nonce and Bob checking timestamp . Old messages/tickets will fail these checks.
- Key Confirmation: Alice confirms she’s getting a key for Bob (checks in ). Bob confirms the key came from Alice (checks in and ).
Lingering Problems with KDC-Based Systems
Even with Kerberos, some fundamental issues remain:
- Single Point of Failure: The KDC holds all the KEKs. If the KDC server is compromised, the entire system is broken. All communication can potentially be decrypted.
- Secure Channel for Initialization: Still need a secure way to distribute the initial KEK (, etc.) to each user when they join.
- No Perfect Forward Secrecy (PFS): This is a subtle but important one. Suppose Oscar records all encrypted traffic between Alice and Bob over months. Later, he manages to steal Alice’s long-term KEK (). Using , he can go back and decrypt all the past messages she received from the KDC, recover all the old session keys (), and then decrypt all the recorded conversations.
- Definition 13.1: Perfect Forward Secrecy (PFS) means that compromising long-term keys (like KEKs) does NOT compromise past session keys.
- KDC-based systems like Kerberos generally do not provide PFS because the session keys are derived directly from (or transported encrypted by) the long-term KEKs.
Key Takeaway Level 3: Basic KDC protocols are vulnerable to replay and impersonation attacks. Kerberos adds nonces, timestamps, lifetimes, and identity checks to fix these. However, all KDC systems suffer from a single point of failure (the KDC itself) and typically lack Perfect Forward Secrecy.
Level 4: Asymmetric Approach & The Man-in-the-Middle (MIM) Attack
Using Public-Key Crypto for Key Establishment
Public-key cryptography seems like a natural fit for key establishment, especially key agreement:
- Diffie-Hellman Key Exchange (DHKE): Alice and Bob can agree on a shared secret key over an insecure channel without any prior shared secrets.
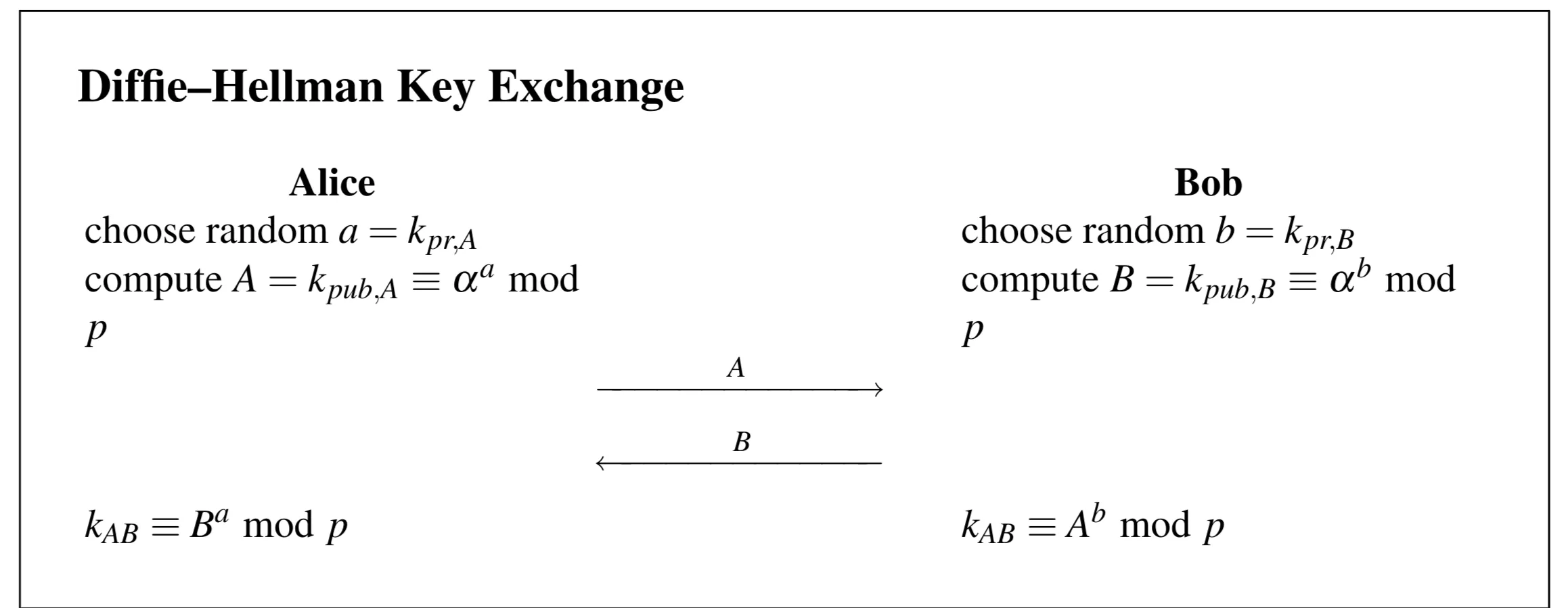
- Alice and Bob agree publicly on large prime and generator .
- Alice chooses private random , computes public , sends to Bob.
- Bob chooses private random , computes public , sends to Alice.
- Alice computes shared secret .
- Bob computes shared secret . They arrive at the same key . An eavesdropper seeing only cannot easily compute or (due to the difficulty of the Discrete Logarithm Problem).
It seems we’ve solved the key establishment problem without needing a KDC or pre-shared keys! … Or have we?
The Man-in-the-Middle (MIM) Attack
DHKE (and other public-key systems used naïvely) is vulnerable to a devastating Man-in-the-Middle (MIM) attack if the public keys ( and ) are not authenticated.
How it Works (DHKE Example): Oscar positions himself between Alice and Bob, intercepting all messages.
- Alice chooses , computes . Sends towards Bob.
- Oscar intercepts . He chooses his own secret random , computes (or maybe just uses for both directions). Oscar sends (or ) to Bob, pretending it came from Alice.
- Bob chooses , computes . Sends towards Alice.
- Oscar intercepts . He computes (or uses the same ). Oscar sends (or ) to Alice, pretending it came from Bob.
- Alice’s Calculation: Alice receives (thinking it’s ). She computes her key as . She thinks she shares this key with Bob.
- Bob’s Calculation: Bob receives (thinking it’s ). He computes his key as . He thinks he shares this key with Alice.
- Oscar’s Calculation: Oscar knows (no, he knows ), (no, he knows ), and his own secret .
- He computes the key he shares with Alice: .
- He computes the key he shares with Bob: .
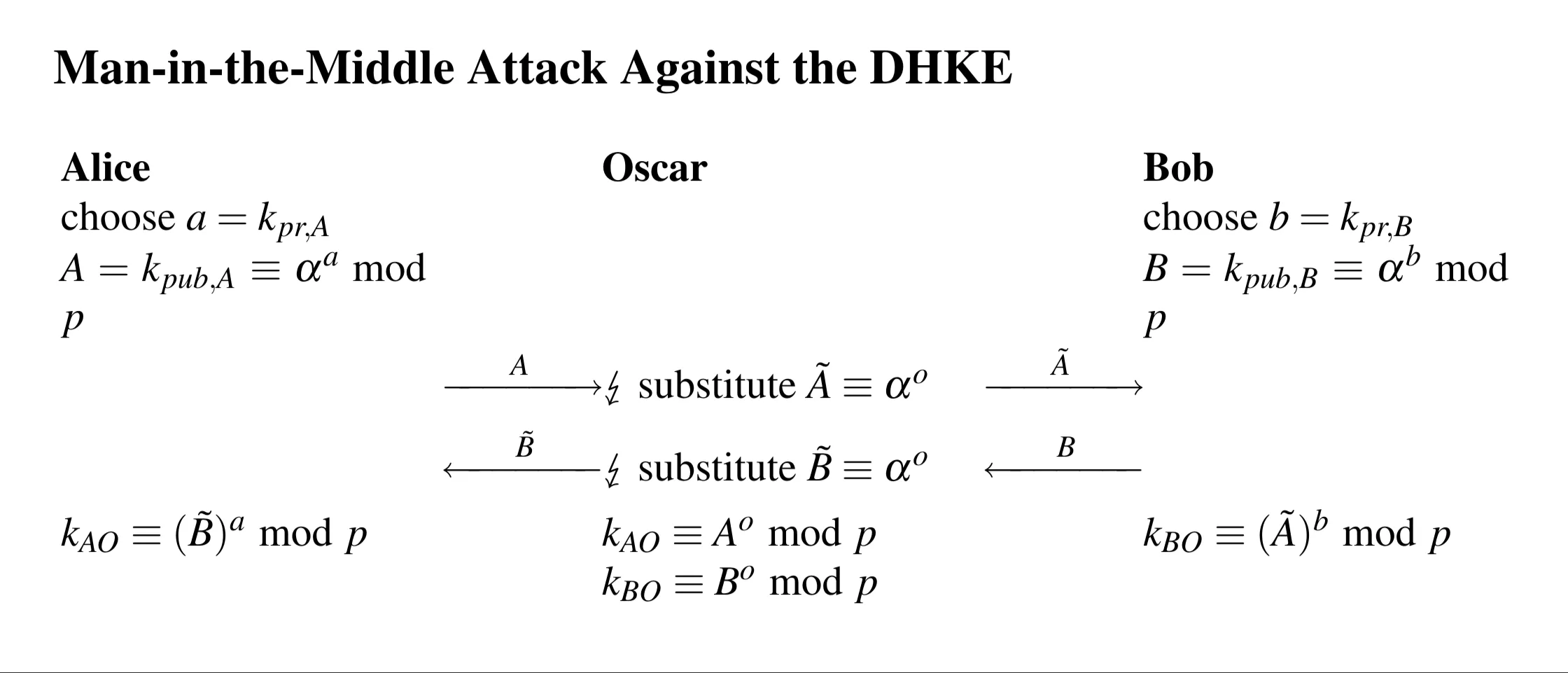 Shows the intercept and substitute flow:
Shows the intercept and substitute flow:
- Alice sends Oscar intercepts. Oscar sends (his value) Bob receives.
- Bob sends Oscar intercepts. Oscar sends (his value) Alice receives.
- Alice computes . Bob computes .
- Oscar computes and .
The Result:
- Alice and Bob think they performed a secure key exchange and share a key .
- In reality, Alice shares key with Oscar, and Bob shares key with Oscar.
- Oscar sits in the middle. When Alice sends a message encrypted with (thinking it’s for Bob), Oscar intercepts, decrypts it with , reads it (and can modify it!), then re-encrypts it with and sends it to Bob. Bob decrypts it with and thinks it came directly from Alice.
(Diagram Explanation - Fig. 13.12) Illustrates the message relay after the MIM key exchange:
- Alice sends .
- Oscar intercepts . Decrypts . Reads/modifies to . Re-encrypts .
- Oscar sends to Bob.
- Bob receives . Decrypts .
The Core Problem: Alice has no way to verify that the public value she received actually came from Bob. Bob has no way to verify came from Alice. Public keys need authentication.
Critical Statement: Even though public-key schemes do not require a secure channel [like symmetric keys initially do], they require authenticated channels for the distribution of the public keys.
Key Takeaway Level 4: Public-key methods like DHKE offer key agreement without pre-shared secrets but are vulnerable to Man-in-the-Middle attacks if the public keys exchanged are not authenticated. Authentication is crucial.
Level 5: The Solution - Certificates, PKI, and Trust
Authenticating Public Keys with Digital Signatures: Certificates
How can Alice be sure that the public key really belongs to Alice? We need to tie an identity () to a public key () in a verifiable way. Digital signatures are perfect for this!
The Idea: Certificates
- We need a trusted third party again, but this one doesn’t hold everyone’s secrets. Let’s call it a Certification Authority (CA).
- Everyone trusts the CA. The CA has its own public/private key pair (). Everyone knows the CA’s authentic public key . (This still needs secure distribution initially, maybe bundled with your OS or browser).
- When Alice wants her public key to be trusted, she goes to the CA.
- The CA verifies Alice’s identity () through some real-world process (e.g., checking documents).
- The CA then creates a certificate which contains:
- Alice’s identity information ().
- Alice’s public key ().
- Other info (like validity period).
- The CA’s digital signature over all this information, created using the CA’s private key .
Formal Structure (Simplified): where
How Certificates Prevent MIM: Now, let’s redo DHKE with certificates.
- Alice generates , . She gets her certificate from the CA, which includes and , signed by the CA.
- Bob generates , . He gets his certificate from the CA, which includes and , signed by the CA.
- Alice sends to Bob. Bob sends to Alice.
- Alice’s Actions:
- Receives .
- Uses the CA’s public key (, which she already trusts) to verify the signature on .
- If the signature is valid, she knows the CA vouches for the contents. She trusts that the public key inside the certificate really belongs to the identity .
- She extracts and computes .
- Bob’s Actions:
- Receives .
- Uses to verify the signature on .
- If valid, he trusts that the public key inside the certificate really belongs to .
- He extracts and computes .
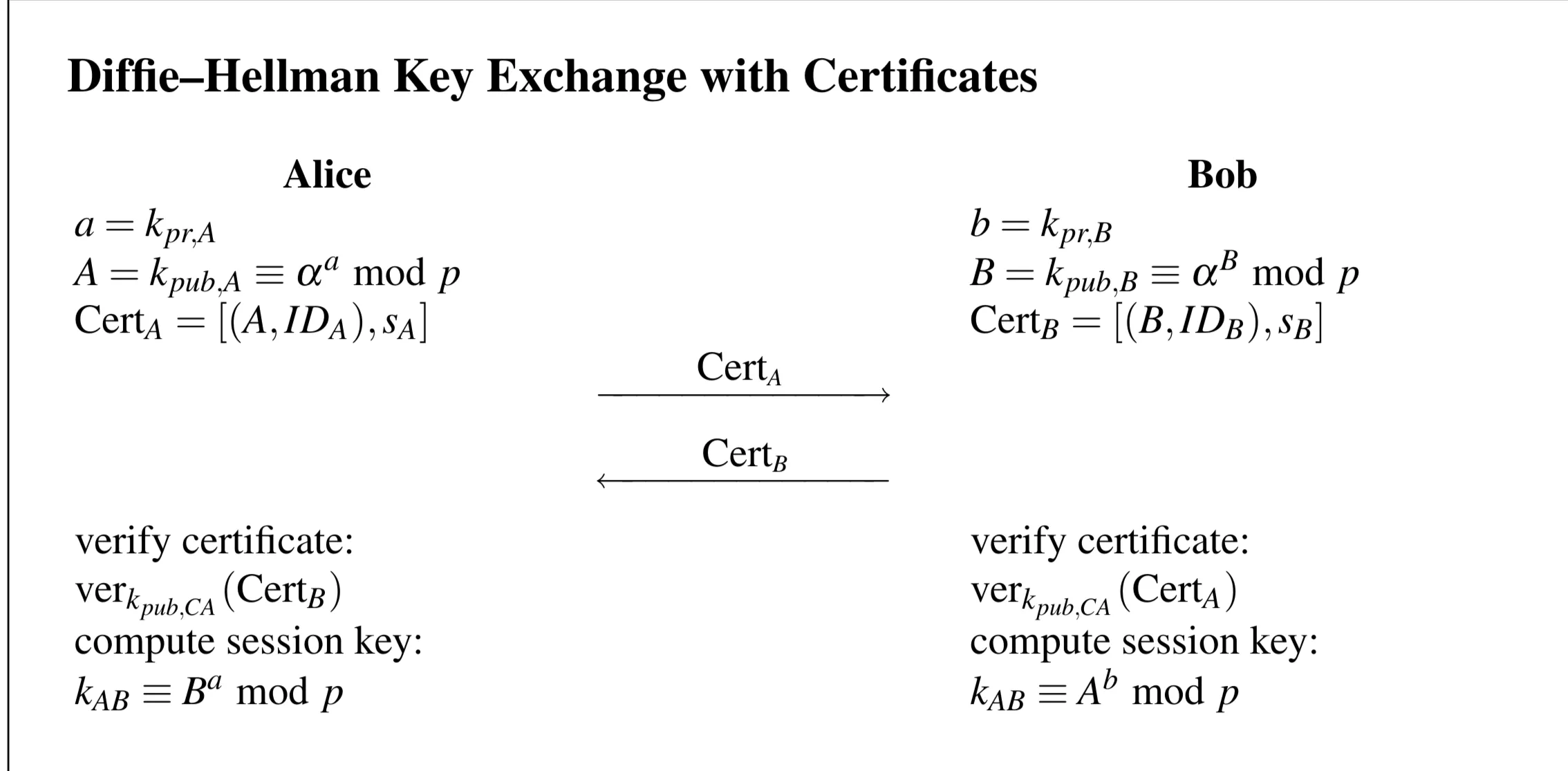
Shows DHKE with Certificates:
- Alice has , computes , has (where is CA’s signature).
- Bob has , computes , has .
- They exchange and .
- Alice verifies using . If ok, computes .
- Bob verifies using . If ok, computes .
MIM ATTACK FAILED
MIM Attack Failed: If Oscar tries the MIM attack now:
- He intercepts . He can’t replace inside with his own because that would invalidate the CA’s signature .
- He could try to get his own certificate from the CA for his key . But this certificate would contain his identity . When Alice or Bob verify it, they would see it’s from Oscar, not from the person they intended to talk to. (Unless Oscar can fool the CA into issuing a certificate with Alice’s ID but Oscar’s key, which is a different attack on the CA’s identity verification process).
Transfer of Trust: Alice and Bob don’t need to trust each other’s keys directly. They only need to trust the CA’s public key. By verifying the CA’s signature, they transfer their trust from the CA to the public key contained in the certificate.
Public-Key Infrastructure (PKI) and The Real World
The whole system of CAs, certificates, policies, procedures for issuing and revoking certificates, etc., is called a Public-Key Infrastructure (PKI).
Real-World Complexities:
- Certificate Generation: Who generates the public/private key pair?
- User-Provided: Alice generates her own and submits to the CA for signing. Requires an authenticated channel for the request. (Fig 13.14 top)
- CA-Generated: Alice requests a certificate. The CA generates for her, creates the certificate, and sends both the certificate and the private key back to Alice. Requires a secure and authenticated channel for the response (since the private key is sent). (Fig 13.14 bottom)
X.509
- X.509 Certificates: A standard format for certificates used widely (e.g., in web browsers for HTTPS/SSL/TLS).
Shows typical X.509 fields:
Serial Number: Unique ID for the certificate.Certificate Algorithm: Which signature algorithm the CA used (e.g., RSA with SHA-256).Issuer: Which CA issued this certificate.Period of Validity: “Not Before” and “Not After” dates. Keys/certificates expire!Subject: The identity () of the key owner (person, server name, etc.).Subject's Public Key: The actual public key and its algorithm (e.g., RSA, ECC) and parameters.Signature: The CA’s digital signature covering all the above fields.
- Multiple CAs & Chains of Trust: What if Alice trusts CA1, but Bob has a certificate from CA2? Alice can’t verify Bob’s certificate directly.
- Solution: Cross-Certification. CA1 issues a certificate for CA2’s public key.
- Chain of Trust: Alice gets (signed by CA2). She also gets (CA2’s public key, signed by CA1).
- Alice verifies using CA1’s public key (which she trusts). If valid, she now trusts CA2’s public key.
- She then uses CA2’s public key to verify . If valid, she now trusts Bob’s public key.
- This can form chains: Root CA certifies intermediate CAs, which certify user certificates. Your browser comes pre-loaded with the public keys of many trusted Root CAs.
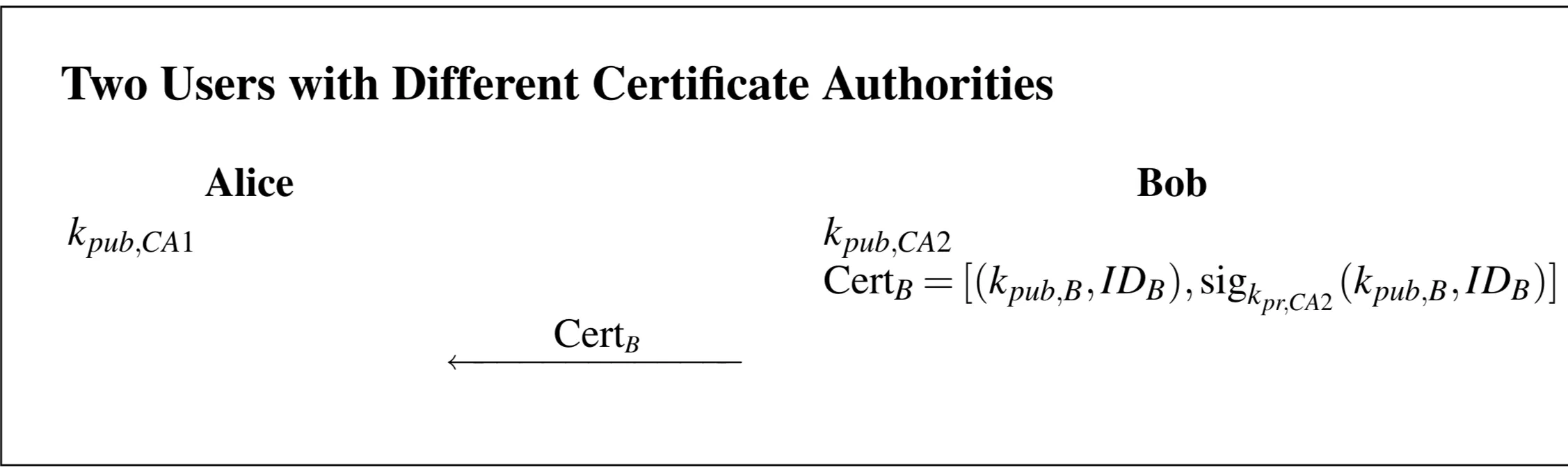 Illustrates this:
Illustrates this:
- Alice has . Bob has and (signed by CA2).
- Bob sends to Alice. Alice can’t verify it.
- Alice requests/receives a certificate for CA2, signed by CA1:
- Alice verifies using . Now she trusts .
- Alice uses to verify . Now she trusts .